Chapter: Cryptography and Network Security Principles and Practice : System Security : Malicious Software
Distributed Denial of Service Attacks
DISTRIBUTED
DENIAL OF SERVICE ATTACKS
Distributed
denial of service
(DDoS) attacks present
a significant security
threat to corporations, and the threat appears to be growing
[VIJA02]. In one study, covering
a three-week period in 2001, investigators observed more than 12,000 attacks against more than 5000 distinct targets,
ranging from well-known ecommerce com- panies such as Amazon
and Hotmail to small foreign
ISPs and dial-up
connections [MOOR01]. DDoS attacks
make computer systems
inaccessible by flooding servers, networks, or even end user systems with useless traffic
so that legitimate users can no longer gain access to those resources. In a typical
DDoS attack, a large number of
compromised hosts are amassed to send useless
packets. In recent
years, the attack methods and tools have become more sophisticated, effective, and more difficult
to trace to the real attackers, while defense technologies have been
unable to with- stand large-scale attacks
[CHAN02].
A denial of service (DoS) attack is an attempt
to prevent legitimate users of a service from using that service. When
this attack comes from a single host or net- work node, then it is simply
referred to as a DoS attack. A more serious threat is posed by a DDoS attack.
In a DDoS attack, an attacker is able to recruit a number of hosts throughout the Internet to simultaneously or in a coordinated fashion launch an attack upon the target. This section is concerned with DDoS attacks.
First, we look at the nature and types of attacks. Next, we examine
means by which an attacker is able to recruit a network of hosts for attack
launch. Finally, this section looks
at countermeasures.
DDoS Attack Description
A DDoS attack attempts to consume the target’s resources
so that it cannot provide service. One way to classify DDoS attacks is in terms
of the type of resource
that is consumed. Broadly speaking, the resource
consumed is either an internal host
resource on the target system or data transmission capacity in the local
network to which the target is attacked.
A simple example of an internal resource attack is the SYN flood attack.
Figure 21.9a shows the steps involved:
1.
The attacker takes control of multiple hosts over the Internet, instructing them to contact the target Web server.
2.
The slave hosts begin sending TCP/IP SYN (synchronize/initialization) packets,
with erroneous return IP address
information, to the target.
3.
Each
SYN packet is a request to open a TCP
connection. For each such
packet, the Web server responds with a SYN/ACK (synchronize/acknowl- edge) packet,
trying to establish
a TCP connection with a TCP entity at a spu-
rious IP address. The Web server
maintains a data structure for each SYN request waiting
for a response back and becomes bogged down as more traffic floods in. The result is that legitimate connections are denied
while the victim machine is waiting to complete bogus
“half-open” connections.
The TCP state data structure is a popular
internal resource target but by no means the only one. [CERT01] gives the
following examples:
1.
In many systems, a
limited number of data structures are available to hold process information (process identifiers, process table entries, process
slots, etc.). An intruder
may be able to consume
these data structures by writing a simple program or script that does nothing
but repeatedly create
copies of itself.
2.
An intruder may also attempt to consume disk
space in other ways,
including
•
generating excessive
numbers of mail messages
•
intentionally generating errors that must be logged
•
placing files
in anonymous ftp areas or network-shared areas
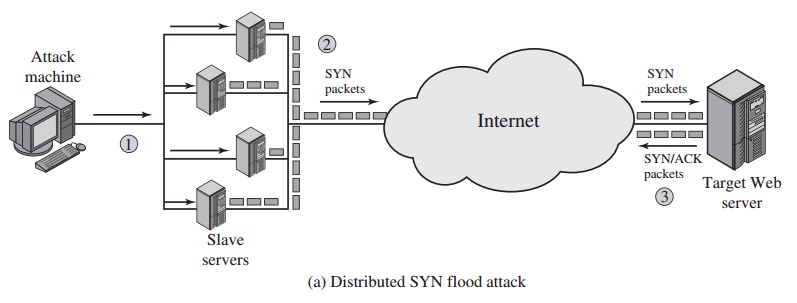
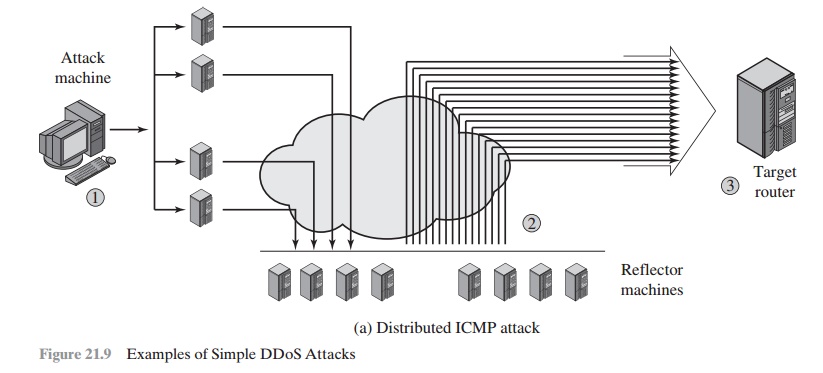
Figure 21.9b illustrates an example of an attack that consumes data transmis- sion resources. The following steps are involved:
1.
The attacker takes control of multiple hosts over the Internet, instructing them to send ICMP ECHO packets3 with the target’s spoofed IP address to a group
of hosts that act as reflectors, as described subsequently.
2.
Nodes at the bounce site receive multiple spoofed requests and respond
by send- ing echo reply packets
to the target site.
3.
The target’s router
is flooded with packets from the bounce site, leaving no data transmission capacity for legitimate traffic.
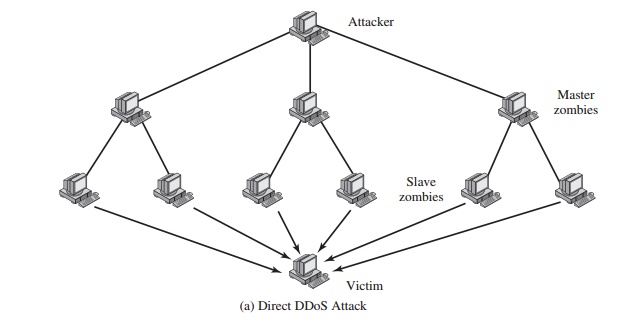
Another way to classify DDoS attacks is as either
direct or reflector DDoS attacks. In a direct DDoS
attack (Figure 21.10a),
the attacker is able to implant zom- bie software on a number of sites
distributed throughout the Internet. Often, the DDoS attack involves two levels of zombie machines: master zombies and slave zom- bies. The hosts
of both machines
have been infected
with malicious code. The attacker coordinates and triggers the
master zombies, which in turn coordinate and trigger the slave zombies.
The use of two
levels of zombies
makes it more
difficult to trace
the attack back to its source and provides for a more resilient network
of attackers.
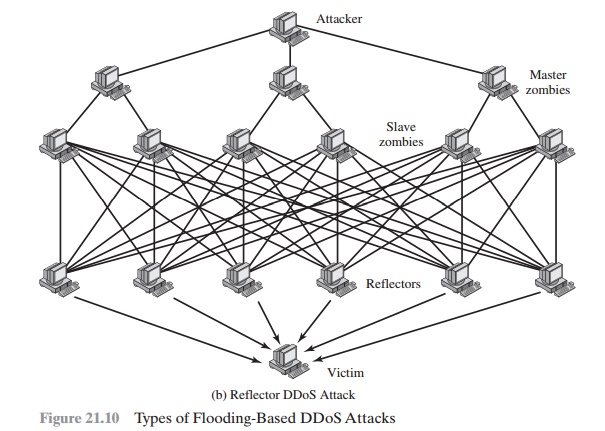
A reflector
DDoS attack adds another layer of machines (Figure 21.10b). In this type of
attack, the slave zombies construct packets requiring a response that contains
the target’s IP address as the source IP address in the packet’s IP header.
These packets are sent to uninfected machines
known as reflectors. The uninfected machines respond with packets
directed at the target machine. A reflector DDoS attack can easily involve
more machines and more traffic
than a direct DDoS attack and hence be more damaging.
Further, tracing back the attack or filtering out the attack packets is more
difficult because the attack comes from widely dispersed uninfected machines.
Constructing the Attack Network
The first step in a DDoS attack is for the attacker to infect
a number of machines with zombie software
that will ultimately be used to carry out the attack.
The essen- tial ingredients in this phase of the attack are the following:
1.
Software that can carry out the DDoS attack.
The software must be able to run
on a large number of machines, must be able to conceal
its existence, must be
able to communicate with the attacker or have some sort of time-triggered mechanism, and must be able to launch the intended attack
toward the target.
2.
A vulnerability in a large number of systems.
The attacker must become aware of a vulnerability that many system administrators and individual users have failed
to patch and that enables the attacker
to install the zombie software.
3.
A strategy
for locating vulnerable machines, a process
known as scanning.
In the scanning process, the attacker first
seeks out a number of vulnerable machines and infects
them. Then, typically, the zombie software
that is installed in the infected machines repeats the same scanning process,
until a large distributed network of infected machines is created. [MIRK04] lists the
following types of scan-
ning
strategies:
Random: Each compromised host probes random
addresses in the IP address space, using a different
seed. This technique
produces a high volume of Internet
traffic, which may cause generalized disruption even before
the actual attack is launched.
•
Hit-List: The attacker first compiles
a long list of potential vulnerable
machines. This can be a slow process
done over a long period
to avoid detec- tion that an attack is underway. Once the list is compiled, the
attacker begins infecting machines on
the list.
Each infected machine is provided
with a portion of the list to scan. This strategy results
in a very short scanning
period, which may make it difficult to detect that infection is taking place.
•
Topological: This method uses
information contained on an infected victim machine to find more hosts to scan.
•
Local subnet: If a host can be infected
behind a firewall,
that host then looks
for targets in its own local network.
The host uses the subnet address
structure to find other
hosts that would
otherwise be protected by the firewall.
DDoS Countermeasures
In general, there are three lines of defense
against DDoS attacks [CHAN02]:
•
Attack prevention and
preemption (before the attack): These mechanisms enable the victim to endure
attack attempts without denying service to
legiti- mate clients. Techniques include
enforcing policies for resource consumption and providing backup resources available on demand.
In addition, prevention mechanisms modify systems and protocols on the Internet
to reduce the possi-
bility of DDoS attacks.
•
Attack detection and
filtering (during the
attack): These mechanisms attempt to detect the attack as it begins and respond immediately.This minimizes the impact of
the attack on the target. Detection involves looking for suspicious patterns of behavior.
Response involves filtering out packets
likely to be part of the attack.
•
Attack source traceback and identification (during
and after the
attack): This is an attempt to identify the source of the attack as a first step in
preventing future attacks. However,
this method typically does not yield results fast enough, if at all, to mitigate an ongoing attack.
The challenge in coping with DDoS attacks is
the sheer number of ways in which they can operate. Thus DDoS countermeasures
must evolve with the threat.
Related Topics