Chapter: Cryptography and Network Security Principles and Practice : System Security : Malicious Software
Computer or Network Worms
WORMS
A worm is a program that can replicate
itself and send copies from computer to computer across network connections. Upon arrival, the worm may be activated to replicate and propagate
again. In addition to propagation, the worm usually performs some unwanted function. An e-mail virus has some of the
characteristics of a worm because it propagates itself
from system to system. However, we can still classify it as a virus because it
uses a document modified to contain viral macro content and requires human
action. A worm actively seeks out more machines to infect and each machine that
is infected serves as an automated launching pad for attacks on other machines.
The concept of a computer worm was introduced in John Brunner’s 1975 SF novel The Shockwave Rider. The first known
worm implementation was done in Xerox Palo Alto Labs in the early 1980s. It was
nonmalicious, searching for idle systems to use to run a computationally
intensive task.
Network worm programs use network
connections to spread from system to system. Once active within a system, a
network worm can behave as a computer virus or bacteria,
or it could implant Trojan horse programs or perform any number
of disruptive or destructive actions.
To replicate itself, a network
worm uses some sort of network vehicle.
Examples include the following:
•
Electronic mail facility: A worm mails a copy of itself to other systems, so that
its code is run when the e-mail or an attachment is received or viewed.
•
Remote execution capability: A worm executes a copy of itself on another system, either
using an explicit remote execution facility or by exploiting a program flaw in a network service
to subvert its operations.
•
Remote login capability: A worm logs
onto a remote
system as a user and
then uses commands to copy itself from one system to the other, where it
then executes.
The new copy of the worm program
is then run on the remote system where, in addition to any functions
that it performs at that system, it continues to spread in the
same fashion.
A network
worm exhibits the same characteristics as a computer virus: a dormant phase,
a propagation phase,
a triggering phase,
and an execution phase. The propagation phase
generally performs the following functions:
1.
Search for other systems
to infect by examining host tables or similar reposi- tories of remote system
addresses.
2.
Establish a connection with a remote
system.
3.
Copy itself to the remote system and cause the copy to be run.
The network
worm may also attempt to determine whether a system has previously been infected before
copying itself to the system.
In a multiprogramming system, it may
also disguise its
presence by naming
itself as a system process
or using some other name that may not be noticed
by a system operator.
As with viruses, network worms are difficult
to counter.
The Morris Worm
Until the current generation of worms,
the best known
was the worm released onto the
Internet by Robert
Morris in 1988 [ORMA03]. The Morris
worm was designed
to spread on UNIX systems and used a number of different techniques for propagation.
When a copy began execution, its first task was to discover other hosts known to this host
that would allow
entry from this
host. The worm performed this task by examin-
ing a variety of lists and tables, including system tables that declared which
other machines were trusted
by this host,
users’ mail forwarding files, tables
by which users gave themselves permission for access to remote accounts, and from a program that reported the status of network connections. For each discovered host,
the worm tried a
number of methods
for gaining access:
1.
It attempted
to log on to a remote host as a legitimate user. In this method, the worm
first attempted to crack the local
password file and then used the
discovered passwords and corresponding user IDs. The assumption was that many users would use the same
password on different systems. To obtain the passwords, the worm ran a password-cracking program that tried
a.
Each user’s account name and simple permutations of it
b.
A list of 432
built-in passwords that Morris thought to be likely candidates2
c.
All the words in the local
system dictionary
2.
It exploited a bug in the UNIX finger protocol, which reports the whereabouts of a remote user.
3.
It exploited a trapdoor in the debug
option of the remote process
that receives and sends mail.
If any of these attacks
succeeded, the worm achieved communication with the operating
system command interpreter. It then sent this interpreter a short boot- strap program,
issued a command
to execute that program, and then logged off. The bootstrap
program then called back the parent program and downloaded the remainder of the worm.
The new worm was then executed.
Worm Propagation
Model
[ZOU05] describes a model
for worm propagation based on an analysis of recent worm attacks. The speed of
propagation and the total number of hosts infected depend on a number
of factors, including the mode of propagation, the vulnerability
or vulnerabilities exploited, and the degree of similarity to preceding
attacks. For the latter factor, an
attack that is a variation of a recent previous attack may be countered more effectively than a more novel attack.
Figure 21.6 shows the dynam- ics for one typical
set of parameters. Propagation proceeds
through three phases.
In the initial phase, the number of hosts increases exponentially. To see that this is so, consider a simplified case in which
a worm is launched from a single
host and infects two nearby hosts. Each of these hosts infects
two more hosts,
and so on. This results in exponential growth. After a time, infecting hosts waste some time attacking
already infected hosts,
which reduces the
rate of infection. During this middle
phase, growth is approximately linear, but the rate of infection is rapid. When most vulner- able
computers have been infected, the attack
enters a slow finish phase as the worm
seeks out those
remaining hosts that are difficult to identify.
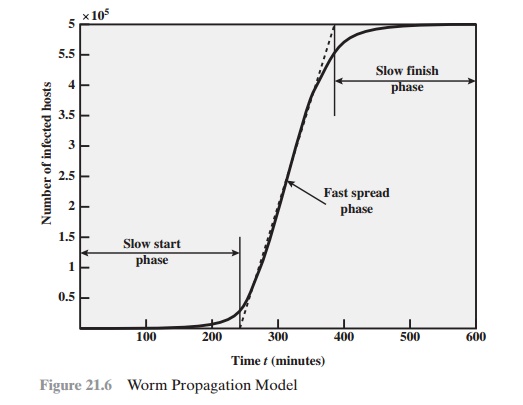
Clearly, the objective in countering a worm is to catch
the worm in its slow start phase, at a time when few hosts have been infected.
Recent Worm Attacks
The contemporary era of worm threats began
with the release of the Code Red worm
in July of 2001. Code Red exploits a
security hole in the Microsoft Internet Information Server (IIS) to penetrate
and spread. It also disables the system file checker in Windows.
The worm probes random
IP addresses to spread to other hosts.
During a certain period of time, it
only spreads. It then initiates a
denial-of-service attack against a government Web site by flooding
the site with packets from numer-
ous hosts. The worm then suspends activities and reactivates periodically. In the second
wave of attack,
Code Red infected
nearly 360,000 servers
in 14 hours. In addi-
tion to the havoc it caused at the targeted server, Code Red consumed enormous
amounts of Internet capacity,
disrupting service.
Code Red II is a variant that targets
Microsoft IISs. In addition, this newer worm installs a backdoor, allowing a
hacker to remotely execute commands on victim
computers.
In early 2003, the SQL Slammer
worm appeared. This worm exploited a buffer overflow vulnerability in Microsoft SQL server. The Slammer
was extremely com- pact and spread rapidly,
infecting 90% of vulnerable hosts
within 10 minutes.
Late 2003 saw the arrival of the Sobig.f
worm, which exploited open proxy servers
to turn infected machines
into spam engines.
At its peak, Sobig.f reportedly accounted for one in every 17 messages and produced more than one million copies
of itself within the first 24 hours.
Mydoom is a mass-mailing e-mail worm that appeared in 2004. It followed a growing
trend of installing a backdoor in infected computers, thereby enabling
hackers to gain remote access to data such as passwords and credit card
numbers. Mydoom replicated up to 1000 times per minute and reportedly
flooded the Internet with
100 million infected messages in 36 hours.
A recent worm that rapidly became prevalent
in a variety of versions is the Warezov family of worms [KIRK06]. When the worm is launched,
it creates several executable in system directories and sets itself
to run every time Windows
starts, by creating a
registry entry. Warezov scans
several types of files for e-mail addresses and sends itself as an e-mail attachment. Some variants are capable of downloading
other malware, such as Trojan horses
and adware. Many variants disable security related products and/or disable
their updating capability.
State of Worm Technology
The state of the art in worm technology
includes the following:
•
Multiplatform: Newer worms are not limited
to Windows machines
but can attack a variety of platforms, especially the popular varieties of UNIX.
•
Multi-exploit: New worms penetrate systems in a variety of
ways, using exploits against Web servers, browsers, e-mail, file
sharing, and other network- based applications.
•
Ultrafast spreading: One
technique to accelerate the spread of a worm is to conduct a prior Internet
scan to accumulate Internet addresses of vulnerable machines.
•
Polymorphic: To evade detection, skip past filters,
and foil real-time analysis, worms adopt the virus polymorphic technique. Each
copy of the worm has new code
generated on the fly using functionally equivalent instructions and encryption techniques.
•
Metamorphic: In addition to changing their
appearance, metamorphic worms have a repertoire of behavior patterns
that are unleashed at different stages
of propagation.
•
Transport vehicles: Because worms
can rapidly compromise a large number
of systems, they are ideal for spreading other distributed attack tools,
such as distributed denial of service bots.
•
Zero-day exploit: To achieve maximum surprise and distribution, a
worm should exploit an unknown
vulnerability that is only discovered by the general network community when the worm is launched.
Mobile Phone Worms
Worms first appeared on mobile phones in 2004. These
worms communicate through Bluetooth wireless connections or via the
multimedia messaging service (MMS). The target is the smartphone, which is a mobile phone that permits
users to install software
applications from sources
other than the cellular network
operator. Mobile phone malware
can completely disable
the phone, delete
data on the phone,
or force the device to send costly messages to premium-priced numbers.
An example of a mobile
phone worm is CommWarrior, which
was launched in 2005.
This worm replicates by means of Bluetooth to other phones in the receiving
area. It also sends itself
as an MMS file to numbers in the phone’s
address book and in
automatic replies to incoming text messages and MMS messages. In addition, it copies
itself to the removable memory card and inserts
itself into the program installation files on the phone.
Worm Countermeasures
There is considerable overlap in techniques
for dealing with viruses and worms. Once a worm is resident
on a machine, antivirus software
can be used to detect
it. In addition, because
worm propagation generates considerable network activity, net- work activity and usage monitoring can form the basis of a worm defense.
To begin, let us consider
the requirements for an effective worm countermea-
sure scheme:
•
Generality: The approach taken
should be able to handle a wide variety of worm attacks, including polymorphic worms.
•
Timeliness: The approach should
respond quickly so as to limit the number of infected systems and the number of
generated transmissions from infected systems.
•
Resiliency: The approach should be resistant
to evasion techniques employed by attackers to evade worm countermeasures.
•
Minimal denial-of-service costs: The approach should
result in minimal
reduc- tion in capacity or service due to the actions of the
countermeasure software. That is,
in an attempt to contain worm propagation, the countermeasure
should not significantly disrupt normal operation.
•
Transparency: The countermeasure software
and devices should not require modification to existing (legacy) OSs, application software, and hardware.
•
Global and local coverage: The approach should be
able to deal with attack sources both from outside and inside the enterprise network.
No existing worm countermeasure scheme
appears to satisfy
all these require- ments. Thus, administrators typically need to use multiple
approaches in defending against worm attacks.
COUNTERMEASURE
APPROACHES
Following [JHI07], we list
six classes of worm defense:
A.
Signature-based worm scan
filtering: This type of approach generates a worm signature,
which is then used to prevent worm scans from entering/leaving a network/host. Typically, this approach involves
identifying suspicious flows and generating a worm signature. This approach is
vulnerable to the use of polymorphic worms: Either
the detection software
misses the worm or, if it is sufficiently sophisticated to deal with
polymorphic worms, the scheme may take a long time to react.
[NEWS05] is an example of this approach.
Filter-based worm containment: This approach is similar to class A but focuses
on worm content rather than a scan signature. The filter checks a message
to determine if it contains worm code. An example
is Vigilante [COST05], which relies
on collaborative worm detection
at end hosts. This
approach can be quite
effective but requires
efficient detection algorithms and rapid alert dissemination.
B.
Payload-classification-based worm containment: These network-based tech- niques examine
packets to see if they contain a
worm. Various anomaly detection
techniques can be used, but care is needed
to avoid high levels of false positives or negatives. An example of
this approach is reported in [CHIN05], which looks for exploit code in network flows. This approach does not generate
signatures based on byte patterns but rather looks for control and
data flow structures that suggest an exploit.
C.
Threshold random
walk (TRW) scan detection: TRW exploits randomness in picking destinations to connect to as a way of
detecting if a scanner is in operation [JUNG04]. TRW is suitable for deployment in high-speed, low-cost network
devices. It is effective against the common behavior seen in worm scans.
D.
Rate limiting: This class limits the rate of scanlike traffic from an infected
host. Various strategies can be used, including limiting the number
of new machines a host can connect
to in a window of time, detecting a high connection failure rate, and limiting the number of unique IP addresses
a host can scan in a window of time. [CHEN04]
is an example. This class
of countermeasures may introduce
longer delays for normal traffic.
This class is also not suited
for slow, stealthy worms that spread
slowly to avoid detection
based on activity
level.
E.
Rate halting: This approach
immediately blocks outgoing traffic when a threshold is exceeded either
in outgoing connection rate or diversity of con- nection attempts [JHI07]. The approach
must include measures to quickly unblock mistakenly blocked hosts in a transparent way. Rate halting can inte-
grate with a signature- or filter-based approach
so that once a signature
or fil- ter is generated, every blocked host can be unblocked. Rate halting appears
to offer a very effective countermeasure. As with rate limiting, rate halting tech- niques are not suitable
for slow, stealthy worms.
We look now at two approaches in more
detail.
PROACTIVE WORM CONTAINMENT The PWC scheme [JHI07] is host based rather than being based on network devices such as honeypots,
firewalls, and network IDSs. PWC is designed
to address the threat
of worms that spread rapidly.
The software on a host looks for surges in the rate of frequency of outgoing connection attempts and the diversity of
connections to remote hosts. When such a surge is detected, the software immediately blocks its host
from further connection attempts.
The developers estimate that only a
few dozen infected packets may be sent out to other
systems before PWC quarantines that attack. In contrast, the
Slammer worm on average sent out 4000 infected packets
per second.
A deployed PWC system consists of a PWC manager
and PWC agents in hosts. Figure
21.7 is an example of an architecture that includes PWC. In this exam-
ple, the security manager, signature
extractor, and PWC manager are implemented
in a single network device.
In practice, these
three modules could
be implemented as two or three separate devices.
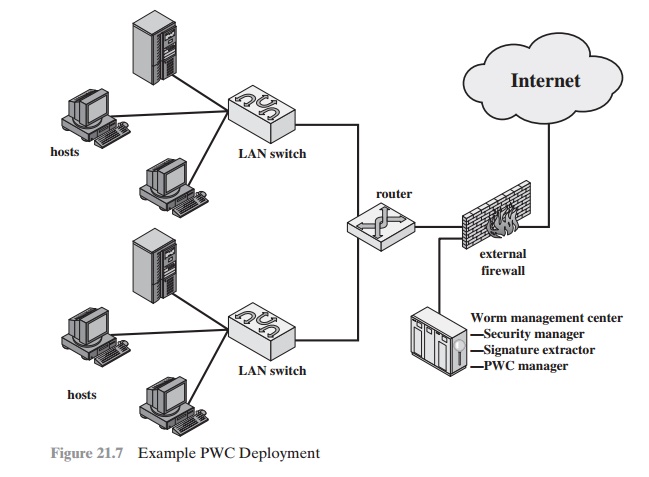
The operation of the PWC architecture can be described as
follows:
A.
A PWC agent monitors outgoing traffic for scan activity, determined by a surge in
UDP or TCP connection attempts to
remote hosts. If a surge is detected, the agent performs
the following actions:
(1) issues an alert to local
system; (2) blocks all outgoing
connection attempts; (3) transmits the alert to the
PWC manager; and (4) starts
a relaxation analysis, described in D.
B.
A PWC manager
receives an alert. The PWC propagates
the alert to all other agents (beside
the originating agent).
C.
The host receives an alert. The agent must decide
whether to ignore
the alert, in the
following way. If the time since the last incoming
packet has been sufficiently long so that the agent
would have detected a worm if
infected, then the alert is ignored. Otherwise, the agent assumes
that it might be infected and performs
the following actions: (1) blocks
all outgoing connection attempts from the specific alerting port; and (2) starts a relaxation analysis, described in D.
D.
Relaxation analysis is performed as follows. An agent monitors outgoing activ-
ity for a fixed window of time to see if outgoing
connections exceed a thresh-
old. If so, blockage is continued and relaxation
analysis is performed for another
window of time.
This process continues until the outgoing
connection rate drops below the threshold, at which time the agent
removes the block. If the threshold continues to be exceeded over a sufficient number of relaxation windows, the agent isolates
the host and reports to the PWC manager.
Meanwhile,
a separate aspect of the worm defense
system is in operation. The signature extractor functions as a passive sensor that monitors all traffic
and attempts to detect worms by
signature analysis. When a new worm is detected, its signature is sent by the security
manager to the firewall to filter out any more copies
of the worm. In addition, the PWC manager sends the signature to PWC agents,
enabling them to immediately recognize infection and disable
the worm.
NETWORK-BASED WORM
DEFENSE The
key element of a network-based worm defense is worm monitoring software.
Consider an enterprise network at a site, consisting of one or an
interconnected set of LANs. Two types of monitoring software are needed:
•
Ingress monitors: These are located
at the border between the enterprise net- work and the Internet.They can be part of the ingress filtering software of a bor-
der router or external firewall or a separate passive monitor. A honeypot can also capture
incoming worm traffic. An example of a detection technique for an ingress monitor is to look for incoming traffic
to unused local
IP addresses.
•
Egress monitors: These can be located
at the egress point of individual LANs on the enterprise network as well as
at the border between the enterprise net-
work and the Internet. In the former case, the egress monitor can be part of
the egress filtering software of a LAN router or switch. As with ingress
moni- tors, the external
firewall or a honeypot can house the monitoring software. Indeed, the two types
of monitors can be collocated. The egress monitor is designed to catch the
source of a worm attack by monitoring outgoing
traffic for signs of scanning or other suspicious behavior.
Worm monitors can act in the manner
of intrusion detection systems and gen- erate alerts to a central administrative system. It is also possible
to implement a sys-
tem that attempts to react in real time to a worm attack, so as to counter
zero-day exploits effectively. This is similar to the approach taken with the
digital immune system (Figure 21.4).
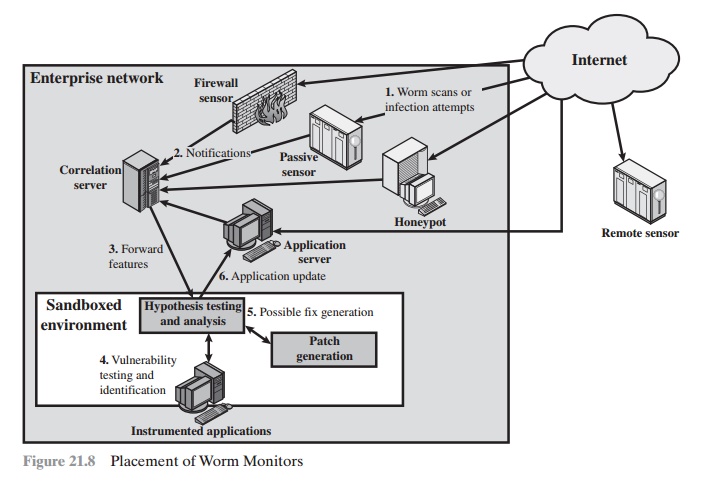
Figure 21.8 shows an example of a worm
countermeasure architecture [SIDI05]. The system works
as follows (numbers in figure refer
to numbers in the following list):
1.
Sensors deployed at
various network locations detect a potential worm. The sensor logic can also be incorporated in IDS sensors.
2.
The sensors send alerts to a central
server that correlates and analyzes
the incom- ing alerts.
The correlation server determines the likelihood that a worm attack
is being observed and the key characteristics of the attack.
3.
The server forwards
its information to a protected environment, where the potential worm may be sandboxed
for analysis and testing.
4.
The protected system
tests the suspicious software against an appropriately instrumented version
of the targeted application to identify
the vulnerability.
5.
The protected system
generates one or more software
patches and tests these.
6.
If the patch is not
susceptible to the infection and does not compromise the application’s functionality, the system sends the patch to the application host to update the targeted application.
The success of such an automated patching
system depends on maintaining a current list of potential attacks and
developing general tools for patching software to counter such attacks.
Examples of approaches are as follows:
•
Increasing the size of buffers
•
Using minor
code-randomization techniques [BHAT03] so that the infection no longer works because the code to be attacked
is no longer in the same form and
location
•
Adding filters
to the application that enable
it to recognize and ignore
an attack
Related Topics