Chapter: Cryptography and Network Security Principles and Practice : One Symmetric Ciphers : Classical Encryption Techniques
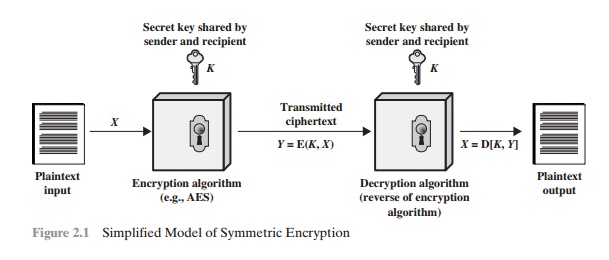
Symmetric Cipher Model
SYMMETRIC CIPHER MODEL
A symmetric encryption scheme has five
ingredients (Figure 2.1):
•
Plaintext:
This is the original
intelligible message or data that is fed into the algorithm as input.
•
Encryption
algorithm: The
encryption algorithm performs various substitu-tions and transformations on the
plaintext.
•
Secret
key: The
secret key is also input to the encryption algorithm. The key is a value
independent of the plaintext and of the algorithm. The algorithm will produce a
different output depending on the specific key being used at the time. The
exact substitutions and transformations performed by the algorithm depend on
the key.
•
Ciphertext:
This is the scrambled
message produced as output. It depends on the plaintext and the secret
key. For a given message, two different keys will produce two different
ciphertexts. The ciphertext is an apparently random stream of data and, as it
stands, is unintelligible.
•
Decryption
algorithm: This is
essentially the encryption algorithm run in reverse. It takes the
ciphertext and the secret key and produces the original plaintext.
There are
two requirements for secure use of conventional encryption:
1.
We
need a strong encryption algorithm. At a minimum, we would like the algorithm
to be such that an opponent who knows the algorithm and has access to one or
more ciphertexts would be unable to decipher the ciphertext or figure out the
key. This requirement is usually stated in a stronger form: The
opponent
should be unable to decrypt ciphertext or discover the key even if he or she is
in possession of a number of ciphertexts together with the plaintext that
produced each ciphertext.
2.
Sender
and receiver must have obtained copies of the secret key in a secure fashion
and must keep the key secure. If someone can discover the key and knows the
algorithm, all communication using this key is readable.
We assume
that it is impractical to decrypt a message on the basis of the ciphertext plus
knowledge of the encryption/decryption algorithm. In other words, we do not
need to keep the algorithm secret; we need to keep only the key secret. This
feature of symmetric encryption is what makes it feasible for widespread use.
The fact that the algorithm need not be kept secret means that manufacturers
can and have developed low-cost chip implementations of data encryption
algorithms. These chips are widely available and incorporated into a number of products.
With the use of symmetric encryption, the principal security problem is
maintaining the secrecy of the key.
Let us take a closer look
at the essential elements of a symmetric encryp-tion scheme, using Figure 2.2.
A source produces a message in plaintext, X = [X1, X2, ..... , XM]. The M elements of X are
letters in some finite alphabet. Traditionally, the alphabet usually
consisted of the 26 capital letters. Nowadays, the binary alphabet {0, 1} is
typically used. For encryption, a key of the form K = [K1, K2, ..... , KJ] is generated. If the key is
generated at the message source, then it must also be provided to the
destination by means of some secure chan-nel. Alternatively, a third party
could generate the key and securely deliver it to both source and destination.
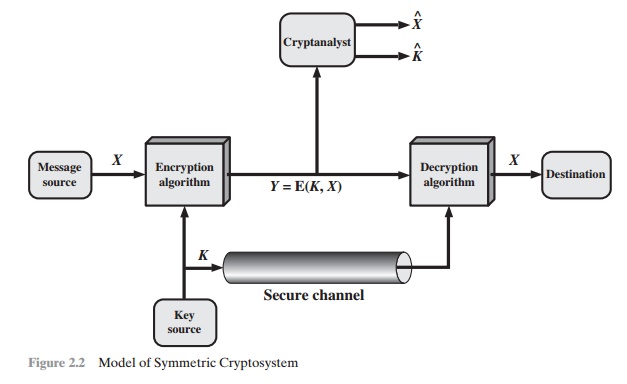
With the
message X and the encryption key K as input, the encryption
algo-rithm forms the ciphertext Y = [Y1, Y2, ..... , YN]. We can write this as
Y = E(K, X)
This
notation indicates that Y is produced by using encryption algorithm E as
a function of the plaintext X , with the specific function determined by
the value of the key K .
The
intended receiver, in possession of the key, is able to invert the transformation:
X = D(K, Y)
An
opponent, observing Y but not having access to K or X ,
may attempt to recover X or K or both X and K. It
is assumed that the opponent knows the encryption
(E) and
decryption (D) algorithms. If the opponent is interested in only this
particular message, then the focus of the effort is to recover X by
generating a plaintext estimate
N
X . Often, however, the opponent is interested in being able to
read future messages as N well, in which case an attempt is made to recover K
by generating an estimate K.
Cryptography
Cryptographic systems are
characterized along three independent dimensions:
1.
The
type of operations used for transforming plaintext to ciphertext. All encryption algorithms are
based on two general principles: substitution, in which each element in the
plaintext (bit, letter, group of bits or letters) is mapped into another
element, and transposition, in which elements in the plaintext are rearranged.
The fundamental requirement is that no informa-tion be lost (that is, that all
operations are reversible). Most systems, referred to as product systems,
involve multiple stages of substitutions and transpositions.
2.
The
number of keys used. If
both sender and receiver use the same key, the system is referred to as
symmetric, single-key, secret-key, or conventional encryp-tion. If the sender
and receiver use different keys, the system is referred to as asymmetric,
two-key, or public-key encryption.
3.
The
way in which the plaintext is processed. A block cipher processes the input
one block of elements at a time, producing an output block for each input
block. A stream cipher processes the input elements continuously,
producing output one element at a time, as it goes along.
Cryptanalysis and Brute-Force Attack
Typically,
the objective of attacking an encryption system is to recover the key in use
rather than simply to recover the plaintext of a single ciphertext. There are
two gen-eral approaches to attacking a conventional encryption scheme:
Cryptanalysis:
Cryptanalytic attacks
rely on the nature of the algorithm plus perhaps some knowledge of the
general characteristics of the plaintext or even some sample plaintext–ciphertext pairs. This type of attack
exploits the characteristics of the algorithm to attempt to deduce a specific
plaintext or to deduce the key being used.
•
Brute-force
attack: The
attacker tries every possible key on a piece of cipher-text until an
intelligible translation into plaintext is obtained. On average, half of all
possible keys must be tried to achieve success.
If either type of attack succeeds in
deducing the key, the effect is catastrophic: All future and past messages
encrypted with that key are compromised.
We first consider cryptanalysis and then discuss brute-force
attacks.
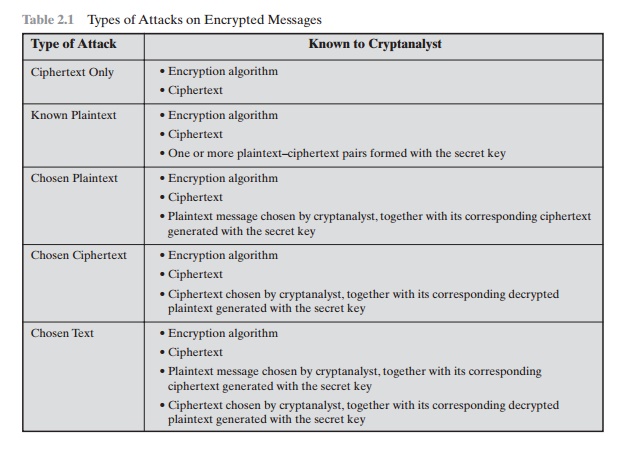
Table 2.1 summarizes the various types
of cryptanalytic attacks based on the amount of information known to the
cryptanalyst. The most difficult problem is pre-sented when all that is
available is the ciphertext only. In some cases, not even the encryption
algorithm is known, but in general, we can assume that the opponent does know
the algorithm used for encryption. One possible attack under these
cir-cumstances is the brute-force approach of trying all possible keys. If the
key space is very large, this becomes impractical. Thus, the opponent must rely
on an analysis of the ciphertext itself, generally applying various statistical
tests to it. To use this approach, the opponent must have some general idea of
the type of plaintext that is concealed, such as English or French text, an EXE
file, a Java source listing, an accounting file, and so on.
The ciphertext-only attack is the
easiest to defend against because the oppo-nent has the least amount of
information to work with. In many cases, however, the analyst has more
information. The analyst may be able to capture one or more plaintext messages
as well as their encryptions. Or the analyst may know that cer-tain plaintext
patterns will appear in a message. For example, a file that is encoded in the
Postscript format always begins with the same pattern, or there may be a
standardized header or banner to an electronic funds transfer message, and so
on. All these are examples of known plaintext. With this knowledge, the
analyst may be able to deduce the key on the basis of the way in which the
known plaintext is transformed.
Closely related to the known-plaintext
attack is what might be referred to as a probable-word attack. If the opponent
is working with the encryption of some gen-eral prose message, he or she may
have little knowledge of what is in the message. However, if the opponent is
after some very specific information, then parts of the message may be known.
For example, if an entire accounting file is being transmitted, the opponent
may know the placement of certain key words in the header of the file. As
another example, the source code for a program developed by Corporation X might
include a copyright statement in some standardized position.
If the analyst is able somehow to get
the source system to insert into the system a message chosen by the analyst,
then a chosen-plaintext attack is possible. An example of this strategy
is differential cryptanalysis, explored in Chapter 3. In general, if the
analyst is able to choose the messages to encrypt, the analyst may deliberately
pick patterns that can be expected to reveal the structure of the key.
Table 2.1 lists two other types of
attack: chosen ciphertext and chosen text. These are less commonly employed as
cryptanalytic techniques but are nevertheless possible avenues of attack.
Only relatively weak algorithms fail
to withstand a ciphertext-only attack. Generally, an encryption algorithm is
designed to withstand a known-plaintext attack.
Two more definitions are worthy of
note. An encryption scheme is unconditionally secure if the ciphertext
generated by the scheme does not con-tain enough information to determine
uniquely the corresponding plaintext, no matter how much ciphertext is
available. That is, no matter how much time an opponent has, it is impossible
for him or her to decrypt the ciphertext simply because the required
information is not there. With the exception of a scheme known as the one-time
pad (described later in this chapter), there is no encryp-tion algorithm that
is unconditionally secure. Therefore, all that the users of an encryption
algorithm can strive for is an algorithm that meets one or both of the
following criteria:
•
The cost of breaking the
cipher exceeds the value of the encrypted information.
•
The time required to break
the cipher exceeds the useful lifetime of the information.
An encryption scheme is said to be computationally secure
if either of the foregoing two criteria are met. Unfortunately, it is very
difficult to estimate the amount of effort required to cryptanalyze ciphertext
successfully.
All forms of cryptanalysis for
symmetric encryption schemes are designed to exploit the fact that traces of
structure or pattern in the plaintext may survive encryption and be discernible
in the ciphertext. This will become clear as we exam-ine various symmetric
encryption schemes in this chapter. We will see in Part Two that cryptanalysis
for public-key schemes proceeds from a fundamentally different premise, namely,
that the mathematical properties of the pair of keys may make it possible for
one of the two keys to be deduced from the other.
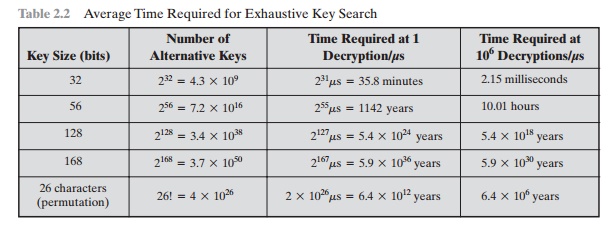
A brute-force attack involves trying every possible key
until an intelligible translation of the ciphertext into plaintext is obtained.
On average, half of all possi-ble keys must be tried to achieve success. Table
2.2 shows how much time is involved for various key spaces. Results are shown
for four binary key sizes. The 56-bit key size is used with the Data Encryption
Standard (DES) algorithm, and the 168-bit key size is used for triple DES. The
minimum key size specified for Advanced Encryption Standard (AES) is 128 bits.
Results are also shown for what are called substitution codes that use a
26-character key (discussed later), in which all possible permutations of the
26 characters serve as keys. For each key size, the results are shown assuming
that it takes 1 μs to perform a single decryption, which is a
reason-able order of magnitude for today’s machines. With the use of massively
parallel organizations of microprocessors, it may be possible to achieve
processing rates many orders of magnitude greater. The final column of Table
2.2 considers the results for a system that can process 1 million keys per
microsecond. As you can see, at this performance level, DES can no longer be
considered computationally secure.
Related Topics