Chapter: Cryptography and Network Security Principles and Practice : One Symmetric Ciphers : Classical Encryption Techniques
Steganography
STEGANOGRAPHY
We conclude with a discussion of a
technique that (strictly speaking), is not encryp-tion, namely, steganography.
A plaintext message may be hidden in one of two ways. The methods of steganography conceal the existence of the message, whereas the methods of cryp-tography render the message unintelligible to outsiders by various transformations of the text.
A simple form of steganography, but
one that is time-consuming to construct, is one in which an arrangement of
words or letters within an apparently innocuous text spells out the real
message. For example, the sequence of first letters of each word of the overall
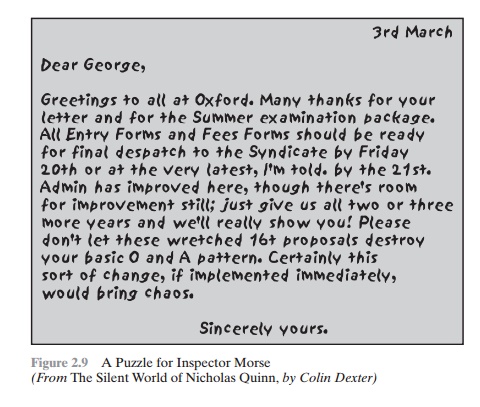
message spells out the hidden message. Figure 2.9 shows an example in which a
subset of the words of the overall message is used to convey the hidden
message. See if you can decipher this; it’s not too hard.
Various other techniques have been
used historically; some examples are the following [MYER91]:
•
Character marking: Selected letters of printed or typewritten text are over-written
in pencil. The marks are ordinarily not visible unless the paper is held at an
angle to bright light.
•
Invisible ink: A number of substances can be used for writing but leave no visible
trace until heat or some chemical is applied to the paper.
•
Pin punctures: Small pin punctures on selected letters are ordinarily not
visi-ble unless the paper is held up in front of a light.
•
Typewriter correction
ribbon: Used between lines typed with a black
ribbon, the results of typing with the correction tape are visible only
under a strong light.
Although these techniques may seem
archaic, they have contemporary equiv-alents. [WAYN93] proposes hiding a
message by using the least significant bits of frames on a CD. For example, the
Kodak Photo CD format’s maximum resolution is 2048 _
3072 pixels, with each pixel containing 24 bits of RGB color information. The
least significant bit of each 24-bit pixel can be changed without greatly
affecting the quality of the image. The result is that you can hide a
2.3-megabyte message in a single digital snapshot. There are now a number of
software packages available that take this type of approach to steganography.
Steganography has a number of
drawbacks when compared to encryption. It requires a lot of overhead to hide a
relatively few bits of information, although using a scheme like that proposed
in the preceding paragraph may make it more effective.Also, once the system is
discovered, it becomes virtually worthless. This problem, too, can be overcome
if the insertion method depends on some sort of key (e.g., see Problem 2.20).
Alternatively, a message can be first encrypted and then hidden using
steganography.
The advantage of steganography is that
it can be employed by parties who have something to lose should the fact of
their secret communication (not necessar-ily the content) be discovered.
Encryption flags traffic as important or secret or may identify the sender or
receiver as someone with something to hide.
Related Topics