Chapter: Mobile Communication
Mobile Network and Transport Layers
Mobile Network and Transport Layers
Contents:
1.
Mobile IP
2.
Dynamic Host Configuration Protocol
3.
Mobile Ad Hoc Routing Protocols
4.
Multicast routing
5.
TCP over Wireless Networks
6.
Indirect TCP
7.
Snooping TCP
8.
Mobile TCP
9.
Fast Retransmit / Fast Recovery
10.
Transmission/Timeout
Freezing-Selective Retransmission
11.
Transaction Oriented TCP- TCP over
2.5 / 3G wireless Networks
Pre requisite Discussion :
In
this unit we discuss what is cellular systems and how the frequency and
channels are allocated. Medium access control tells how to reduce traffic in
the network and we discuss about frequency , time, space and code division
multiple access.
1. Mobile IP:
Concept:
Goals
For Mobile IP
The Internet is the network for
global data communication with hundreds of millions of users. The reason is
quite simple:
You will not receive a single packet
as soon as you leave your home network, ie., The network your computer is
configured for, and reconnect your computer (wireless or wired) at another
place. A host sends an IP packet with the header containing a destination
address besides other fields.
The destination address not only
determines the receiver of the packet, but also the physical subnet of the
receiver.
Routers in the Internet now look at
the destination addresses of incoming pack-ets and forward them according to
internal look-up tables.
To avoid an explosion of routing
tables, only prefixes are stored and further optimizations are applied.
Otherwise a router would have to
store the addressed of all computers in the Internet which is obviously not
feasible.
As long as the receiver can be
reached within its physical subnet it gets the packets as soon as it moves
outside the subnet, no packet will reach it anymore.
Thus a host needs a so called
topologically correct address.
Solutions:
Assigning the computer a new
topologically correct IP address.
So moving to a new location would
also mean assigning a new address.
Now the problem is that nobody knows
of this new address.
It is almost impossible to find a (mobile) host
in the Internet which has just changed its address. Especially the Domain Name
System (DNS) needs some time before it update its internal tables necessary for
the mapping of a logical name to an IP address.
This approach does not work if the mobile node
moves quite often. Furthermore the Internet and DNS have not been built for
frequent updates.
Significance:
∑ IP packet Delivery
∑ Path Delivery
2.
DYNAMICHOST
CONFIGURATION PROTOCOL
Concept:
The Dynamic Host Protocol (DHCP,RFC 2131)
mainly used
TO simply the installation
Maintenance of networked computers
∑ If a new computer is connected to a network
DHCP can provide it with all the necessary Information for full system integration
into the network e.g:-Addresses of DNS server and Default router Subnet Mask
Domain name IP address
∑ Providing an IP address makes DHCP very
attractive for mobile IP as well source of care-of address.
Basic
DHCP configuration
DHCP clients send a request to a server to
which the server responds.
A client sends requests using MAC broadcasts to
reach all devices in the LAN.
A DHCP relay might be needed to forward
requests across inter-working units to a DHCP server.
Client Initialization
The client broadcasts a DHCP DISCOVER into
subnet. There may be relay to forwards this broadcast.
Two servers receive this broadcast and
determine the configuration they offer to the client. Servers reply to the
client s request with DHCPOFFER and
offer a list of configuration parameters.
The client can now choose one of the
configurations offered.
The client in turn replies to the servers
accepting one of the configurations and rejecting the others using DHCP
REQUEST.
If a server receives a DHCP REQUEST with a
rejection it can free the reserved configuration for other possible clients.
The server with the configuration accepted by
the client now confirms the configuration with DHCP ACK.This completes the
initialization phase.
If a client leaves the subnet it should release
the configuration received by the server using
DHCP RELEASE.
Now the server can free the context stored for
the client and offer the configuration again.
The configuration a client from a server is
only leased for a certain amount of time it has to be reconfirmed from time to
time.
Otherwise the server will be free the
configuration. This timeout of configuration helps in the case of crashed nodes
or nodes moved away without realizing the context.
DHCP
Features
DHCP supporting the acquisition of
care-of-address for mobile nodes
A DHCP server should located in the subnet of
the access point of the mobile note.
DHCP relay should provide forwarding of the
Messages.
RFC 3118 specifies authentication for DHCP
messages which id needed to protect mobile nodes from malicious DHCP servers.
Significance:
Provides a protocol for the
countries where the calls and IPs are dynamically allotted.
3. Mobile Adhoc Routing:
Concept:
In wireless networks using an infrastructure
cells have been defines. within a cell the bse station can reach all mobile
nodes.
In -hoc networks each node must be able to
forward data for other nodes. At a certain time t1 the network topology
consists of five nodes N1 to N5.
Nodes are connected depending upon
the current transmission characteristics between them. In this network N4 can
receive N1 over a good link.
But N1 receive N4 via a weak link.
Links do not necessarily have the
same characteristics in both directions.
Reason:
Different antenna characteristics or
transmit power. N1 cannot receive N2 at all
N2 receives a signal from N1. At a
certain time t2 the network topology consists of five nodes N1 to N5.This
situation can change quite fast N1 cannot receive N4 any longer
N4 receives N1 only via a weak link.
But N1 has as asymmetric but
bi-directional link to N2 that did not exist before.
The Fundamental differences between
wired networks and ad-hoc networks related to routing.
Asymmetric
Links
Node A receives a signal from node
B.
But this does not tell anything
about the quality of the connection in reverse. Node B might
Receive nothing
Have a weak link
Even have a better link than the reverse
direction.
Routing information collected for
one direction is of almost no use for the other direction.
Redundant
Links
Wired networks too have a redundant
links to survive link failures.
There is only some redundancy in
wired networks which additionally are controlled by a network administrator.
In ad-hoc networks nobody controls
redundancy so there might be many redundant links up to the extreme of a
completely meshed topology.
Routing algorithms for wired
networks can handle some redundancy but a high redundancy can cause a large
computational overhead for routing table updates.
Signifiacance:
Gives a protocol for configuring the
mobiles.
4. Multicast Routing:
Concept:
Multicast IP Routing protocols are
used to distribute data (for example, audio/video streaming broadcasts) to
multiple recipients. Using multicast, a source can send a single copy of data
to a single multicast address, which is then distributed to an entire group of
recipients.
A multicast group identifies a set
of recipients that are interested in a particular data stream, and is
represented by an IP address from a well-defined range. Data sent to this IP
address is forwarded to all members of the multicast group.
Routers between the source and
recipients duplicate data packets and forward multiple copies wherever the path
to recipients diverges. Group membership information is used to calculate the
best routers at which to duplicate the packets in the data stream to optimize
the use of the network.
A source host sends data to a
multicast group by simply setting the destination IP address of the datagram to
be the multicast group address. Any host can become a source and send data to a
multicast group. Sources do not need to register in any way before they can
begin sending data to a group, and do not need to be members of the group
themselves.
There are many different multicast
protocols and modes of operation, each optimized for a particular scenario.
Many of these are still at an early stage of standardization. However, they all
operate in the same general way, as follows.
∑ A Multicast Group Membership Discovery protocol is used by receiving
hosts to advertise their group membership to a local multicast router, enabling
them to join and leave multicast groups. The main Multicast Group Membership
Discovery protocols are Internet Group Management Protocol (IGMP) for IPv4 and
Multicast Listener Discovery (MLD) for IPv6.
∑ A Multicast Routing Protocol is used to communicate between multicast
routers and enables them to calculate the multicast distribution tree of
receiving hosts. Protocol Independent Multicast (PIM) is the most important
Multicast Routing Protocol.
The multicast distribution tree of
receiving hosts holds the route to every recipient that has joined the
multicast group, and is optimized so that
∑ multicast traffic does not reach
networks that do not have any such recipients (unless the network is a transit
network on the way to other recipients)
∑ duplicate copies of packets are kept
to a minimum.
Significance:
This one provides a protocol for
sending the call/data from one mobile station to several other stations.
5. TCP over Wireless networks:
Concept:
Slow
Start
TCP s
reaction to a missing acknowledgement is quite drastic but it is necessary to
get rid of congestion quickly.
The behavior shows after the detection of
congestion is called Slow start. The sender always calculates a Congestion
window for a receiver.
The start size of the congestion window is one
segment (TCP Packet). The sender sends one packet and waits for
acknowledgement.
If this acknowledgement arrives the sender
increases the congestion window by one now sending two packets (congestion
window=2)
After arrival of the two corresponding
acknowledgements now the congestion window equals 4. This scheme doubles the
congestion window every time the acknowledgements come back which takes one Round
Trip Time (RIT).This is
called the exponential growth of the congestion window in the slow start
mechanism.
It is too dangerous to double the congestion
window each time because the steps might become too large. The exponential
growth stops at the Congestion Threshold.
The congestion window reaches the congestion
threshold further increase of the transmission rate is only linear by adding 1
to the congestion window each time the acknowledgements come back.
Linear increase continues until a time-out at
the sender occurs due to a missing acknowledgement or until the sender detects
a gap in transmitted data because of continuous acknowledgements for the same
packet.
In either case the sender sets the congestion
threshold to half of the current congestion window. The congestion window
itself is set to one segment and the sender starts sending a single segment.
The exponential growth starts once more up to
the new congestion threshold then the window grows in Linear fashion.
Significance:
Can be used in wireless communications too.
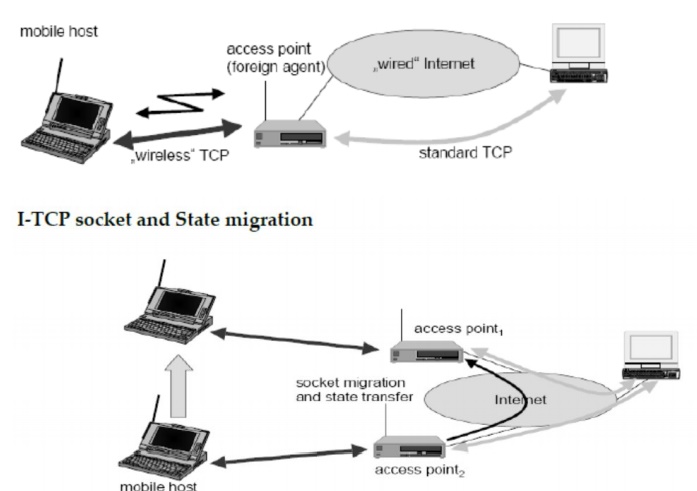
6. Indirect TCP or I-TCP Concept:
Indirect
TCP Advantages and Disadvantages
Disadvantages
Loss of end-to-end semantics, an
acknowledgement to a sender does now not any longer mean that a receiver really
got a packet, foreign agents might crash.
Higher latency possible due to
buffering of data with the foreign agent and forwarding to a new foreign agent
High trust at foreign agent;
end-to-end encryption impossible
Significance:
No changes in the fixed network
necessary, no changes for the hosts (TCP protocol) necessary, all current
optimizations to TCP still work
Transmission errors on the wireless
link do not propagate into the fixed network simple to control, mobile TCP is
used only for one hop, between a foreign agent and a mobile host Therefore, a
very fast retransmission of packets is possible, the short delay on the mobile
hop is known
7. Snooping TCP
Concepts:
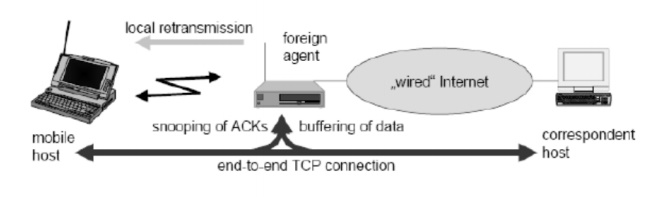
The foreign agent buffers all packets with Destination
mobile host.
Additionally snoops
the packet flow in both directions to recognize acknowledgements.
The reason for buffering the packets toward the
mobile node is to enable the foreign agent to perform a local transmission in
case of packet loss on the wireless link.
The foreign agent buffers every packet until it
receives an acknowledgement from the mobile host.
If the foreign agent does not receive an
acknowledgement from the mobile host within a certain amount of time either the
packet or
the acknowledgement has been lost.
Alternatively the foreign agent could receive a
duplicate ACK which also shows the loss of a packet.
Now the foreign agent
·
Retransmits
the packet directly from the buer.
·
Performing
a much faster retransmission completed to the correspondent host.
·
The
time out for acknowledgements can be much shorter because it reflects only the
delay of one hop plus processing time.
·
To remain
transparent the foreign agent must not acknowledge data to the correspondent
host.
·
·
The
correspondent host believe that the mobile host had received the data would
violate the end-to end semantic in case of a foreign agent failure.
·
·
The
foreign agent can filter the duplicate acknowledgements to avoid unnecessary
retransmissions of data from the correspondent host.
If the foreign agent now crashes the
time-out of the correspondent host still works and triggers a retransmission.
The foreign agent may discard
duplicates of packets already retransmitted locally and acknowledged by the
mobile host.
Significance:
This avoids unnecessary traffic on
the wireless link.
8.
Mobile TCP
Concept:
Special handling of lengthy and/or
frequent disconnections
M-TCP splits as I-TCP does
unmodified TCP fixed network to supervisory host (SH)
optimized TCP SH to MH Supervisory
host no caching, no retransmission monitors all packets, if disconnection
detected l set sender window size to 0
l sender automatically goes into
persistent mode q old or new SH reopen the window Disadvantages
loss on wireless link propagated
into fixed network adapted TCP on wireless link
Significance:
maintains semantics, supports
disconnection, no buffer forwardin
9.
Fast
Retransmit / Fast Recovery
Concept:
Reduction
of the congestion threshold
A sender receiving continuous
acknowledgements for the same packets. This informs the sender of two things.
One is that the receiver got all packets up to the acknowledged packet in
sequence.
Fast
Retransmit
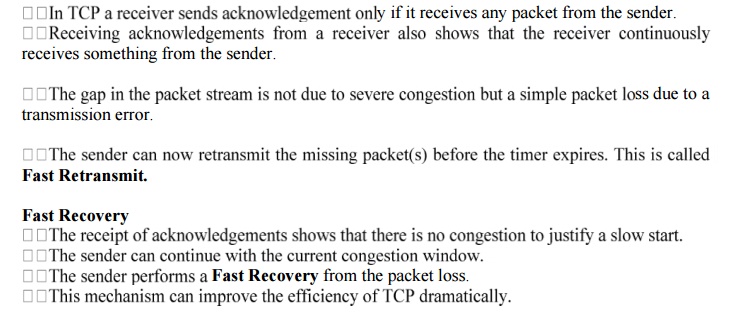
The other reason for activating slow start is a
time-out due to a missing acknowledgement. TCP using Fast Retransmit / Fast
Recovery interprets this congestion in the
network and activates the slow start mechanism.
10. Transmission / Timeout Freezing-Selective Retransmission
Concepts:
Mobile hosts can be disconnected for a longer
time
no packet exchange possible, e.g., in a tunnel, disconnection due to overloaded cells
or mux. with higher priority traffic TCP disconnects after time-out completely
TCP freezing
MAC layer is often able to detect interruption
in advance MAC can inform TCP layer of upcoming loss of connection TCP stops
sending, but does not assume a congested link MAC layer signals again if
reconnected
Disadvantage
TCP on mobile host has to be changed, mechanism
depends on MAC layer
Significance:
Scheme is independent of data
11. Transaction Oriented TCP- TCP over 2.5 / 3G wireless
Networks
Concepts:
Fine tuning today s TCP Learn to live with
_ Data rates: 64 kbit/s upstream, 384 kbit/s
downstream (UMTS release99); asymmetry: 3-6, but also up to 1000 (broadcast
systems), periodic allocation/release of channels
_ High
latency, high jitter, packet loss Suggestions
_ Large (initial) window size, large maximum
transfer unit, selective acknowledgement, explicit congestion notification,
timestamps, no header compression
Already in use _ i-mode in Japan
_ WAP 2.0
( TCP with wireless profile ) Transport layer
_ Local
retransmissions and acknowledgements Additionally on the application layer
_ Content filtering, compression, picture
downscaling _ E.g., Internet/WAP gateways
_ Web service gateways?
Big problem: breaks end-to-end semantics _
Disables use of IP security!
More issues
RFC 3150 (slow links)
_
Recommends header compression, no timestamp RFC 3155 (links with errors)
_ States
that explicit congestion notification cannot be used In contrast to 2.5G/3G
recommendations!
Significance:
Used to differentiate the 2.8G/3G over the TCP
Applications:
o Fine tuned for Mobile usage over the TCP
o Almost all the Devices Makes use of this layer for sending the data o Used for the Mobile devices that are designed these days either2.5/3G