Chapter: Computer Networks : Network Layer
Forwarding Techniques
Forwarding
Forwarding
means to place the packet in its route to its destination. Forwarding requires
a host or a router to have a routing table. When a host has a packet to send or
when a router has received a packet to be forwarded, it looks at this table to
find the route to the final destination. However, this simple solution is
impossible today in an internetwork such as the Internet because the number of
entries needed in the routing table would make table lookups inefficient.
Forwarding Techniques
Several
techniques can make the size of the routing table manageable and also handle
issues such as security.
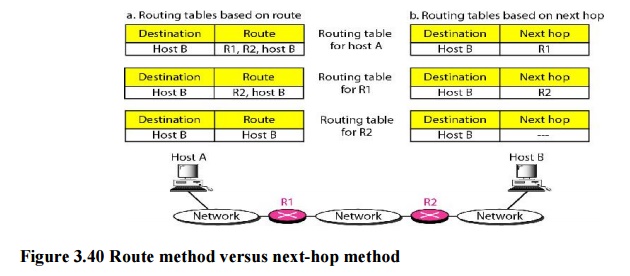
a. Next-Hop Method versus Route Method
One
technique to reduce the contents of a routing table is called the next-hop
method. In this technique, the routing table holds only the address of the next
hop instead of information about the complete route (route method). The entries
of a routing table must be consistent with one another.
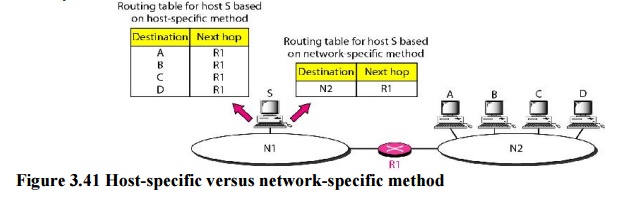
b. Network-Specific Method versus Host-Specific
Method
A second
technique to reduce the routing table and simplify the searching process is
called the network-specific method. Here, instead of having an entry for every
destination host connected to the same physical network (host-specific method),
we have only one entry that defines the address of the destination network
itself.
Host-specific
routing is used for purposes such as checking the route or providing security
measures
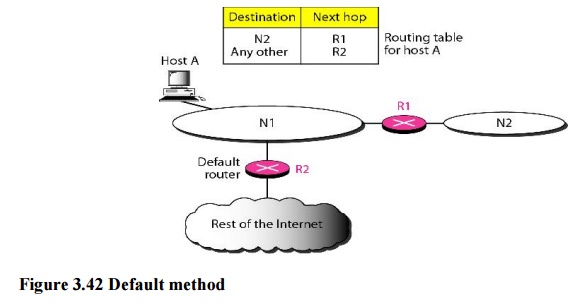
c. Default Method
Another
technique to simplify routing is called the default method. Host A is connected
to a network with two routers. Router R1 routes the packets to hosts connected
to network N2. However, for the rest of the Internet, router R2 is used. So
instead of listing all networks in the entire Internet, host A can just have
one entry called the default (normally defined as network address 0.0.0.0).
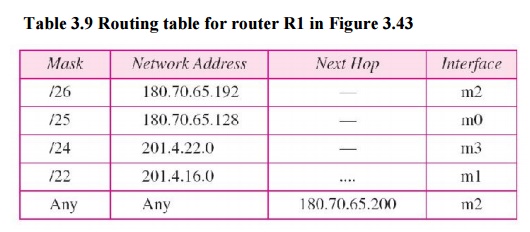
Example 3.18
Make a
routing table for router R1, using the configuration in Figure 3.43
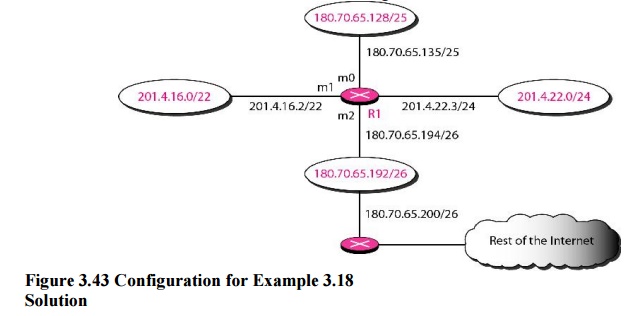
Example 3.19
Show the
forwarding process if a packet arrives at R1 with the destination address
180.70.65.140.
Solution
The
router performs the following steps:
1. The first
mask (/26) is applied to the destination address. The result is 180.70.65.128,
which does not match the corresponding network address.
2. The
second mask (/25) is applied to the destination address. The result is
180.70.65.128, which matches the corresponding network address. The next-hop
address (the destination address of the packet in this case) and the interface
number m0 are passed to ARP for further processing.
Example 3.20
Show the
forwarding process if a packet arrives at R1 with the destination address
201.4.22.35.
Solution
The
router performs the following steps:
·
The first mask (/26) is applied to the destination
address. The result is 201.4.22.0, which does not match the corresponding
network address (row 1).
· The
second mask (/25) is applied to the destination address. The result is
201.4.22.0, which does not match the corresponding network address (row 2).
· The third
mask (/24) is applied to the destination address. The result is 201.4.22.0,
which matches the corresponding network address. The destination address of the
packet and the interface number m3 are passed to ARP.
Example 3.21
Show the
forwarding process if a packet arrives at R1 with the destination address
18.24.32.78.
Solution
This time
all masks are applied, one by one, to the destination address, but no matching
network address is found. When it reaches the end of the table, the module
gives the next-hop address 180.70.65.200 and interface number m2 to ARP. This
is probably an outgoing package that needs to be sent, via the default router,
to someplace else in the Internet.
Related Topics