Chapter: 11th Computer Science : Chapter 17 : Computer Ethics and Cyber Security
Cyber Security and Threats
Cyber
Security and Threats
Cyber
attacks are launched primarily for causing significant damage to a computer
system or for stealing important information from an individual or from an
organization. Cyber security is a collection of various technologies, processes
and measures that reduces the risk of cyber attacks and protects organizations
and individuals from computer based threats.
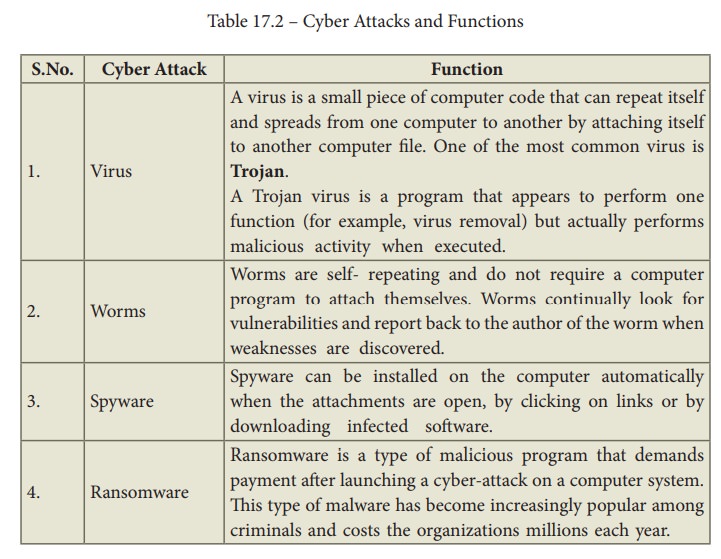
TYPES OF CYBER ATTACKS
Malware
is a type of software designed through which the criminals gain illegal access
to software and cause damage. Various types of cyber-attacks and their
functions are given inTable 17.2.
Cyber Security Threats
In
recent years, most of the individuals and enterprises are facing problems due
to the weaknesses inherent in security systems and compromised organizational
infrastructures. Different types of Cyber Security Threats are categorized as
below:
Social engineering
A
misuse of an individual’s weakness, achieved by making them to click malicious
links, or by physically accessing the computer through tricks. Phishing and
pharming are examples of social engineering.
Phishing
Phishing
is a type of computer crime used to attack, steal user data, including login
name, password and credit card numbers. It occurs when an attacker targets a
victim into opening an e-mailor an instant text message. The attacker uses
phishing to distribute malicious links or attachments that can perform a
variety of functions, including the extraction of sensitive login credentials
from victims.
Pharming
Pharming
is a scamming practice in which malicious code is installed on a personal
computer or server, misdirecting users to fraudulent web sites without their
knowledge or permission. Pharming has been called "phishing without a
trap”. It is another way hackers attempt to manipulate users on the Internet.
It is a cyber-attack intended to redirect a website's traffic to a fake site.
Man In The Middle (MITM)
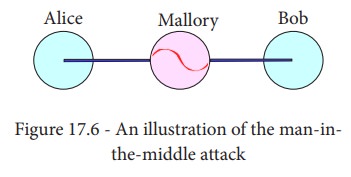
![]() Man-in-the-middle attack (MITM; also Janus attack) is an
attack where the attacker secretly relays and possibly alters the communication
between two parties who believe they are directly communicating with each
other.
Man-in-the-middle attack (MITM; also Janus attack) is an
attack where the attacker secretly relays and possibly alters the communication
between two parties who believe they are directly communicating with each
other.
Example: Suppose Alice wishes to communicate with Bob. Meanwhile,
Mallory wishes to intercept the conversation to overhear and optionally to
deliver a false message to Bob.
Cookies
A cookie (also called HTTP cookie, web cookie, Internet cookie, browser cookie, or simply cookie) is a small piece of data sent from a website and stored on the user's computer memory (Hard drive) by the user's web browser while the user is browsing internet. Cookies were designed to be a reliable mechanism for websites to remember stateful information (such as items added in the shopping cart in an online store) or to record the user's browsing activity (including clicking particular buttons, logging in etc.). They can also be used to remember arbitrary pieces of information that the user previously entered into form fields such as names, addresses, passwords, and credit card numbers. From the security point of view, if cookie data is not encrypted, any anonymous user (hacker) can access the cookie information and misuse it.
Web sites typically use cookies for the following reasons:
•
To collect demographic information about who has visited the Web site.
•
Sites often use this information to track how often visitors come to the site
and how long they remain on the site.
•
It helps to personalize the user's experience on the Web site.
•
Cookies can help store personal information about users so that when a
usersubsequently returns to the site, a more personalized experience is
provided.
If
you ever returned to a site and have seen your name mysteriously appear on the
screen, it is because on a previous visit, you gave your name to the site and
it was stored in a cookie. A good example of this is the way some online
shopping sites will make recommendations to users based on their previous purchases.
It helps to monitor advertisements. Cookies do not act maliciously on computer
system. They are merely text files that can be deleted at any time.
Cookies
cannot be used to spread viruses and they cannot access your hard drive.
However, any personal information that you provide to a Web site, including
credit card information, will most likely be stored in a cookie unless the
cookie feature is explicitly turned off in your browser. This is the way in
which cookies threaten privacy.
Firewall and Proxy Servers
![]() A firewall is a computer network security based system that
monitors and controls incoming and outgoing network traffic based on predefined
security rules. A firewall commonly establishes a block between a trusted
internal computer network and entrusted computer outside the network. They are
generally categorized as network-based or host-based. Network based firewalls
are positioned on the gateway computers of LANs [local area Network], WANs
[Wide Area Network] and intranets. Host-based firewalls are positioned on the
network node itself. The host-based firewall may be a service as a part of the
operating system or an agent application such as endpoint security or
protection. Each has advantages and disadvantages. However, each has a role in
layered security. Firewalls also vary in type depending on where communication
originates, where it is intercepted, and the state of communication being
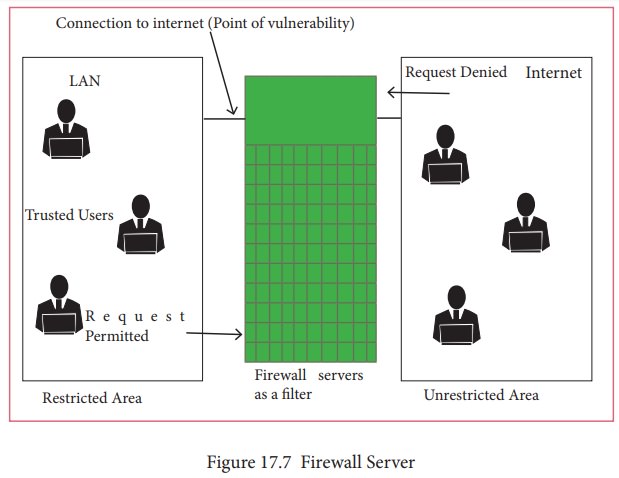
traced. Figure 17.7 shows the
working of firewall server.
A firewall is a computer network security based system that
monitors and controls incoming and outgoing network traffic based on predefined
security rules. A firewall commonly establishes a block between a trusted
internal computer network and entrusted computer outside the network. They are
generally categorized as network-based or host-based. Network based firewalls
are positioned on the gateway computers of LANs [local area Network], WANs
[Wide Area Network] and intranets. Host-based firewalls are positioned on the
network node itself. The host-based firewall may be a service as a part of the
operating system or an agent application such as endpoint security or
protection. Each has advantages and disadvantages. However, each has a role in
layered security. Firewalls also vary in type depending on where communication
originates, where it is intercepted, and the state of communication being
traced. Figure 17.7 shows the
working of firewall server.
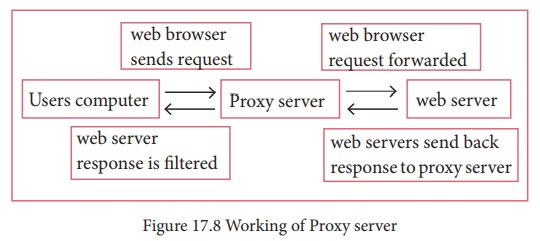
A
proxy server acts as an intermediary between the endusersand a web server. A
client connects to the proxy server, requesting some service, such as a file,
connection, web page, or other resources available from a different server. The
proxy server examines the request, checks authenticity and grants the request
based on that. Proxy servers typically keep the frequently visited site
addresses in its cache which leads to improved response time.
Figure 17.8 shows the working of a proxy server.
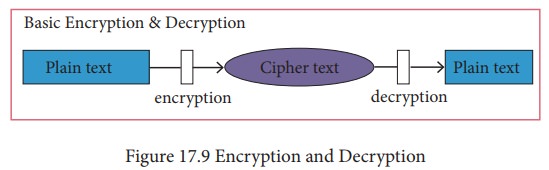
Encryption and Decryption
Encryption
and decryption are processes that ensure confidentiality that only authorized
persons can access the information.
Encryption
is the process of translating the plain text data (plaintext) into random and
mangled data (called cipher-text).
Decryption
is the reverse process of converting the cipher-text back to plaintext.
Encryption and decryption are done by cryptography. In cryptography a key is a
piece of information (parameter) that determines the functional output of a
cryptographic algorithm.
Figure 17.9 shows the encryption and decryption
process.
Encryption
has been used by militaries and governments to facilitate secret communication.
It is now commonly used in protecting information within many kinds of civilian
systems. It is also used to protect data in communication system, for example
data being transferred via networks (e.g. the Internet, ecommerce), mobile
telephones, wireless microphones, wireless intercom systems, Bluetooth devices
and bank automatic teller machines. There have been numerous reports of data in
communication being intercepted in recent years. Data should also be encrypted
when transmitted across networks in order to protect against the network
traffic by unauthorized users.
TYPES OF ENCRYPTION
There
are two types of encryption schemes as listed below:
•
Symmetric Key encryption
•
Public Key encryption
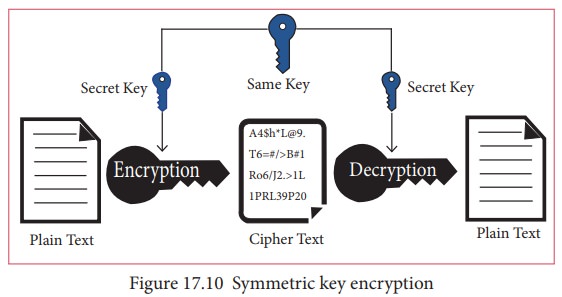
SYMMETRIC KEY ENCRYPTION
Symmetric
encryption is a technique to use the same key for both encryption and
decryption. The main disadvantage of the symmetric key encryption is that all
authorized persons involved, have to exchange the key used to encrypt the data
before they can decrypt it. If anybody intercepts the key information, they may
read all message. Figure 17.10
depicts the working of symmetric key encryption.
PUBLIC KEY ENCRYPTION
Public
key encryption isalso called Asymmetric encryption. It uses the concept of a
key value pair, a different key is used for the encryption and decryption
process. One of the keys is typically known as the private key and the other is
known as the public key.
The
private key is kept secret by the owner and the public key is either shared
amongst authorized recipients or made available to the public at large.
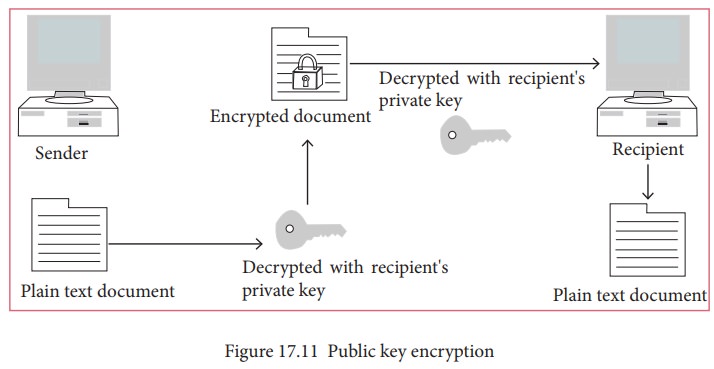
The
data encrypted with the recipient’s public key can only be decrypted with the
corresponding private key. Figure 17.11
shows the public key encryption.
Asymmetric Encryption in Digital Certificates:
A
digital certificate in a client-server model of communication is one of the
example of Asymmetric Encryption. A certificate is a package of information
that identifies a user and a server. It contains information such as an
organization’s name, the organization that issued the certificate, the users’
email address and country, and user’s public key.
When
a server and a client require a secure encrypted communication, they send a
query over the network to the other party, which sends back a copy of the
certificate. The other party’s public key can be extracted from the
certificate. A certificate can also be used to uniquely identify the holder.
Digital Signature
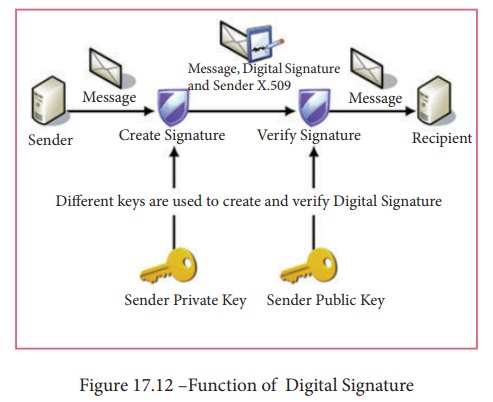
Digital signatures are based on asymmetric cryptography and can provide assurances of evidence to origin, identity and status of an electronic document, transaction or message, as well as acknowledging informed by the signer.
To
create a digital signature, signing software (email) creates a one-way hash of
the electronic data to be signed. The user's private key to encrypt the hash,
returning a value that is unique to the hashed data. The encrypted hash, along
with other information such as the hashing algorithm, forms the digital
signature. Any change in the data, even to a single bit, results in a different
hash value. This attribute enables others to validate the integrity of the data
by using the signer's public key to decrypt the hash. If the decrypted hash
matches a second computed hash of the same data, it proves that the data hasn't
changed since it was signed. If the two hashes don't match, the data has either
been tampered with in some way (indicating a failure of integrity) or the
signature was created with a private key that doesn't correspond to the public
key presented by the signer (indicating a failure of authentication). Figure 17.12 shows the function of a
digital signature.
Related Topics