Computer Ethics and Cyber Security | Computer Science - Answer the following questions | 11th Computer Science : Chapter 17 : Computer Ethics and Cyber Security
Chapter: 11th Computer Science : Chapter 17 : Computer Ethics and Cyber Security
Answer the following questions
Computer Ethics and Cyber Security
Evaluation
PART - II
Answer to all the questions (2 Marks):
1. What is harvesting?
Answer: A person or program collects login and password information from a legitimate user to illegally gain access to others, account(s).
2. What are Warez?
Answer: Commercial programs that are made available to the public illegally are often called warez.
3. Write a short note on cracking.
Answer: "Cracking" means trying to get into computer systems in order to steal, corrupt, or illegitimately view data.
4. Write two types of cyber attacks.
Answer: (i) Virus
(ii) Worms.
5. What is a Cookie?
Answer: A cookie (also called HTTP cookie, web cookie, Internet cookie, browser cookie, or simply cookie) is a small piece of data sent from a website and stored on the user's computer memory (Hard drive) by the user's web browser while the user is browsing Internet.
PART - III
Answer to all the questions (3 Marks):
1. What is the role of firewalls?
Answer: A firewall is a computer network security based system that monitors and controls incoming and outgoing network traffic based on predefined security rules. A firewall commonly establishes a block between a trusted internal computer network and entrusted computer outside the network.
2. Write about encryption and decryption.
Answer:
(i) Encryption : Encryption is the process of encoding a message or information so that only authorized users can decrtypt it.
(ii) Decryption : Decryption is the process of decoding the encrypted text by converting it back into normal text.
3. Explain symmetric key encryption.
Answer: Symmetric encryption is a technique to use the same key for both encryption and decryption. The main disadvantage of the symmetric key encryption is that all authorized persons involved, have to exchange the key used to encrypt the data before they can decrypt it. If anybody intercepts the key information, they may read all message
4. What are the guidelines to be followed by any computer user?
Answer:
(i) Honesty : Users should be truthful while using the internet.
(ii) Confidentiality: Users should not share any important information with unauthorized people.
(iii) Respect: Each user should respect the privacy of other users.
(iv) Professionalism: Each user should maintain professional conduct.
(v) Obey The Law: Users should strictly obey the cyber law in computer usage.
(vi) Responsibility: Each user should take ownership and responsibility for their actions
5. What are ethical issues? Name some.
Answer: Some of the common ethical issues are listed below:
(i) Cyber crime
(ii) Software Piracy
(iii) Unauthorized Access
(iv) Hacking
(v) Use of computers to commit fraud
(vi) Sabotage in the form of viruses
(vii) Making false claims using computers.
PART - IV
Answer to all the questions (5 Marks):
1. What are the various crimes happening using computer?
Crime : Function
Crime Functions : Hacking, threats, and blackmailing towards a business or a person.
Cyber stalking: Harassing through online.
Malware: Malicious programs that can perform a variety of functions including stealing, encrypting or deleting sensitive data, altering or hijacking core computing functions and monitoring user's computer activity without their permission.
Denial of service attack: Overloading a system with fake requests so that it cannot serve normal legitimate requests.
Fraud: Manipulating data, for example changing the banking records to transfer money to an unauthorized account.
Harvesting: A person or program collects login and password information from a legitimate user to illegally gain access to others, account(s).
Identity theft: It is a crime where the criminals impersonate individuals, usually for financial gain.
Intellectual property theft: Stealing practical or conceptual information developed by another person or company
Salami slicing: Stealing tiny amounts of money from each transaction.
Scam: Tricking people into believing something that is not true.
Spam: Distribute unwanted e-mail to a large number of internet users.
Spoofing: It is a malicious practice in which communication is send from unknown source disguised as a source known to the receiver.
2. What is piracy? Mention the types of piracy? How can it be prevented?
Answer:
(i) Software Piracy is about the copyright violation of software created originally by an individual or an institution. It includes stealing of codes/ programs and other information illegally and creating duplicate copies by unauthorized means and utilizing this data either for one's own benefit or for commercial profit.
(ii) In simple words, Software Piracy is "unauthorized copying of software” The following show as a digrammatical representation of software piracy.
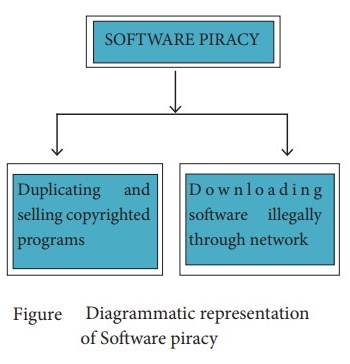
(iii) Most of the commercial software is licensed for use at a single computer site or for use by only one user at any time. When a user buys any software, he becomes a licensed user for that software. He is allowed to make copies of the program for backup purposes, but it is against the law to distribute duplicate copies to others. Such illegal copying and distribution of commercial software should not be practiced
(iv) An entirely different approach to software piracy is called shareware, acknowledges the futility of trying to stop people from copying software and instead relies on people's honesty.
(v) Shareware publishers encourage users to give copies of programs to friends and colleagues but ask everyone who uses that program regularly to pay a registration fee to the program's author directly. Commercial programs that are made available to the public illegally are often called warez.
3. Write the different types of cyber attacks.
Answer:
1. Virus
Function: Avirus is a small piece of computer code that can repeat itself and spreads from one computer to another by attaching itself to another computer file. One of the most common virus is Trojan.
Trojan: A Trojan virus is a program that appears to perform one function (for example, virus removal) but actually performs malicious activity when executed.
2. Worms
Function: Worms are self- repeating and do not require a computer program to attach themselves. Worms continually look for vulnerabilities and report back to the author of the worm when weaknesses are discovered.
3. Spyware
Function: Spyware can be installed on the computer automatically when the attachments are open, by clicking on links or by downloading infected software.
4. Ransomware
Function: Ransomware is a type of malicious program that demands payment after launching a cyber-attack on a computer system. This type of malware has become increasingly popular among criminals and costs the organizations millions each year.
Related Topics