Chapter: Computer Networks : Routing
Areas
AREAS
An area
is a set of routers that are administratively configured to exchange link-state
information with each other. There is one special area—the backbone area, also
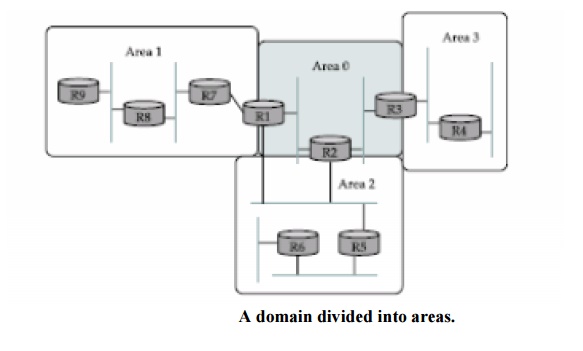
known as area 0. An example of a routing domain divided into areas is shown in
Figure . Routers R1, R2, and R3 are members of the backbone area. They are also
members of at least one no backbone area; R1 is actually a member of both area
1 and area 2. A router that is a member of both the backbone area and a
nonbackbone area is an area border router (ABR). Note that these are distinct
from the routers that are at the edge of an AS, which are referred to as AS
border routers for clarity. All the routers in the area send link-state
advertisements to each other, and thus develop a complete, consistent map of
the area. However, the link-state advertisements of routers that are not area
border routers do not leave the area in which they originated. This has the
effect of making the flooding and route calculation processes considerably more
scalable. For
example,
router R4 in area 3 will never see a link-state advertisement from router R8 in
area 1. As a consequence, it will know nothing about the detailed topology of
areas other than its own.
The route
from sending node to mobile node can be significantly suboptimal. One of the
most extreme examples is when a mobile node and the sending node are on the
same network, but the home network for the mobile node is on the far side of
the Internet.
The
sending node addresses all packets to the home network; they traverse the
Internet to reach the home agent, which then tunnels them back across the
Internet to reach the foreign agent. Clearly it would be nice if the sending
node could find out that the mobile node is actually on the same network and
deliver the packet directly.
In the
more general case, the goal is to deliver packets as directly as possible from
sending node to mobile node without passing through a home agent.
This is
sometimes referred to as the triangle routing problem since the path from
sender to mobile node via home agent takes two sides of a triangle, rather than
the third side that is the direct path. The basic idea behind the solution to
triangle routing is to let the sending node know the care-of address of the
mobile node.
The
sending node can then create its own tunnel to the foreign agent. This is
treated as an optimization of the process just described. If the sender has
been equipped with the necessary software to learn the care of address and
create its own tunnel, then the route can be optimized; if not, packets just
follow the suboptimal route.
Mobile
routing provides some interesting security challenges. For example, an attacker
wishing to intercept the packets destined to some other node in an internetwork
could contact the home agent for that node and announce itself as the new
foreign agent for the node. Thus, it is clear that some authentication
mechanisms are required.
When a
home agent sees a packet destined for one of the mobile nodes that it supports,
it can deduce that the sender is not using the optimal route. Therefore, it
sends a binding update message back to the source, in addition to forwarding
the data packet to the foreign agent.
The
source, if capable, uses this binding update to create an entry in a binding
cache, which consists of a list of mappings from mobile node addresses to
care-of addresses. The next time this source has a data packet to send to that
mobile node, it will find the binding in the cache and can tunnel the packet
directly to the foreign agent.
Related Topics