Chapter: Computer Networks : Transport Layer
User Datagram Protocol (UDP)
USER DATAGRAM PROTOCOL (UDP)
The User
Datagram Protocol (UDP) is called a connectionless, unreliable transport
protocol. It does not add anything to the services of IP except to provide
process-to process communication instead of host-to-host communication. Also, it
performs very limited error checking.
UDP is a
very simple protocol using a minimum of overhead. If a process wants to send a
small message and does not care much about reliability, it can use UDP. Sending
a small message by using UDP takes much less interaction between the sender and
receiver than using TCP or SCTP.
1. Well-Known Ports for UDP:
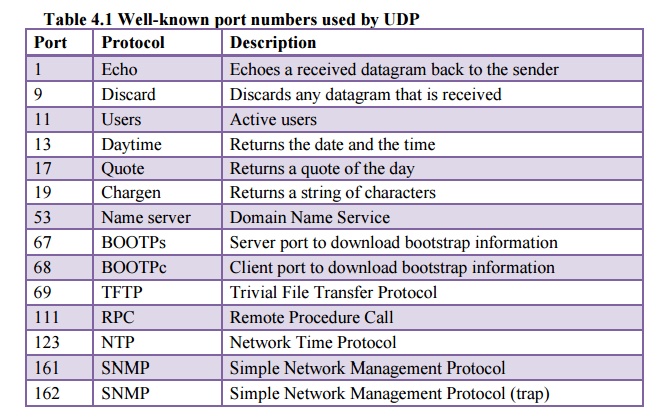
Table 4.1
shows some well-known port numbers used by UDP. Some port numbers can be used
by both UDP and TCP1
2. User Datagram
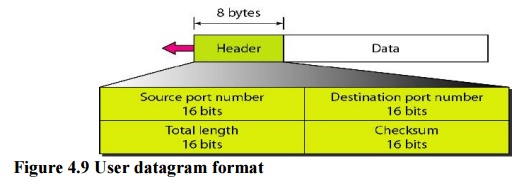
UDP
packets, called user datagrams, have a fixed-size header of 8 bytes. Figure 4.9
shows the format of a user datagram.
The
fields are as follows:
·
Source
port number. This is the port number used by the process
running on the sourcehost. It is 16 bits long, which means that the port number
can range from 0 to 65,535.
·
Destination
port number. This is the port number used by the process
running on thedestination host. It is also 16 bits long.
·
Length. This is
a 16-bit field that defines the total length of the user datagram, headerplus
data. The 16 bits can define a total length of 0 to 65,535 bytes.
UDP
length = IP length - IP header's length
·
Checksum. This
field is used to detect errors over the entire user datagram (header plusdata).
3. Checksum
The UDP
checksum calculation is different from the one for IP and ICMP. Here the
checksum includes three sections: a pseudoheader, the UDP header, and the data
coming from the application layer
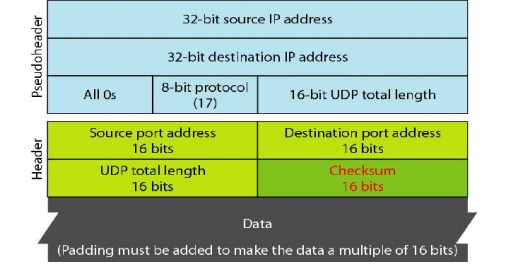
Figure 4.10 Pseudoheader for checksum calculation
The
pseudoheader is the part of the header of the IP packet in which the user
datagram is to be encapsulated with some fields filled with Os (see Figure
4.10).
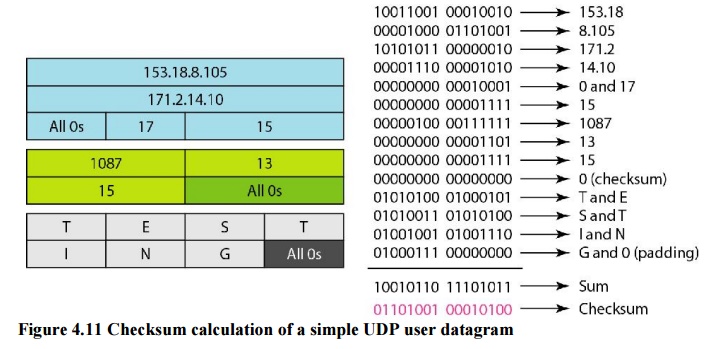
Example 4.1
Figure
4.11 shows the checksum calculation for a very small user datagram with only 7
bytes of data. Because the number of bytes of data is odd, padding is added for
checksum calculation. The pseudoheader as well as the padding will be dropped
when the user datagram is delivered to IP.
Optional
use of the checksum:
The
calculation of the checksum and its inclusion in a user datagram are optional.
If the checksum is not calculated, the field is filled with 1s. Note that a
calculated checksum can never be all 1s because this implies that the sum is
all 0s, which is impossible because it requires that the value of fields to be
0s.
4. UDP Operation:
UDP uses
concepts common to the transport layer.
Connectionless
Services
UDP
provides a connectionless service. This means that each user datagram sent by
UDP is an independent datagram. There is no relationship between the different
user datagrams even if they are coming from the same source process and going
to the same destination program. The user datagrams are not numbered. Also,
there is no connection establishment and no connection termination. This means
that each user datagram can travel on a different path.
Flow and
Error Control
UDP is a
very simple, unreliable transport protocol. There is no flow control and hence
no window mechanism. The receiver may overflow with incoming messages. There is
no error control mechanism in UDP except for the checksum. This means that the
sender does not know if a message has been lost or duplicated. When the
receiver detects an error through the checksum, the user datagram is silently
discarded. The lack of flow control and error control means that the process
using UDP should provide these mechanisms.
Encapsulation
and Decapsulation
To send a
message from one process to another, the UDP protocol encapsulates and
decapsulates messages in an IP datagram.
Queuing
In UDP,
queues are associated with ports. (Figure 4.12).
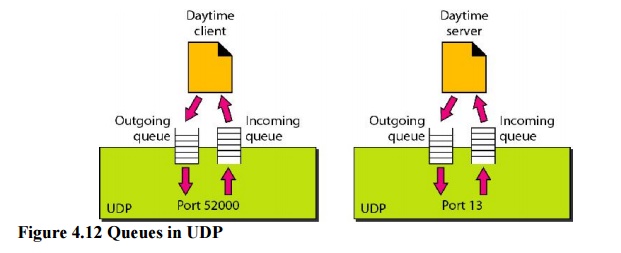
At the
client site, when a process starts, it requests a port number from the
operating system. Some implementations create both an incoming and an outgoing
queue associated with each process. Other implementations create only an
incoming queue associated with each process.
Note that
even if a process wants to communicate with multiple processes, it obtains only
one port number and eventually one outgoing and one incoming queue. The queues
opened by the client are, in most cases, identified by ephemeral port numbers.
The queues function as long as the process is running. When the process
terminates, the queues are destroyed.
The
client process can send messages to the outgoing queue by using the source port
number specified in the request. UDP removes the messages one by one and, after
adding the UDP header, delivers them to IP. An outgoing queue can overflow. If
this happens, the operating system can ask the client process to wait before
sending any more messages.
5. Use of UDP
The
following lists some uses of the UDP protocol:
·
UDP is suitable for a process that requires simple
request-response communication with little concern for flow and error control.
It is not usually used for a process such as FTP that needs to send bulk data.
·
UDP is suitable for a process with internal flow
and error control mechanisms. For example, the Trivial File Transfer Protocol
(TFTP) process includes flow and error control. It can easily use UDP.
·
UDP is a suitable transport protocol for
multicasting. Multicasting capability is embedded in the UDP software but not
in the TCP software.
·
UDP is used for management processes such as SNMP.
·
UDP is used for some route updating protocols such
as Routing Information Protocol (RIP).
Related Topics