Chapter: Cryptography and Network Security Principles and Practice : One Symmetric Ciphers : Pseudorandom Number Generation and Stream Ciphers
RC4
RC4
RC4 is a stream cipher
designed in 1987 by Ron Rivest for RSA Security. It is a variable key size stream cipher with byte-oriented operations. The algorithm
is based on the
use of a random permutation. Analysis shows that
the period of the cipher
is over- whelmingly likely
to be greater than 10100 [ROBS95a]. Eight to sixteen machine
oper- ations are required per output byte, and the cipher can be
expected to run very quickly in software. RC4 is used
in the Secure
Sockets Layer/Transport Layer Security
(SSL/TLS) standards that have been defined for communication between Web browsers and servers.
It is also used in the Wired Equivalent Privacy (WEP)
protocol and the newer WiFi Protected Access (WPA) protocol that are part of the IEEE
wireless LAN standard. RC4 was kept as a trade secret by RSA Security.
In September 1994, the RC4 algorithm was anonymously posted
on the Internet on the Cypherpunks anonymous remailers list.
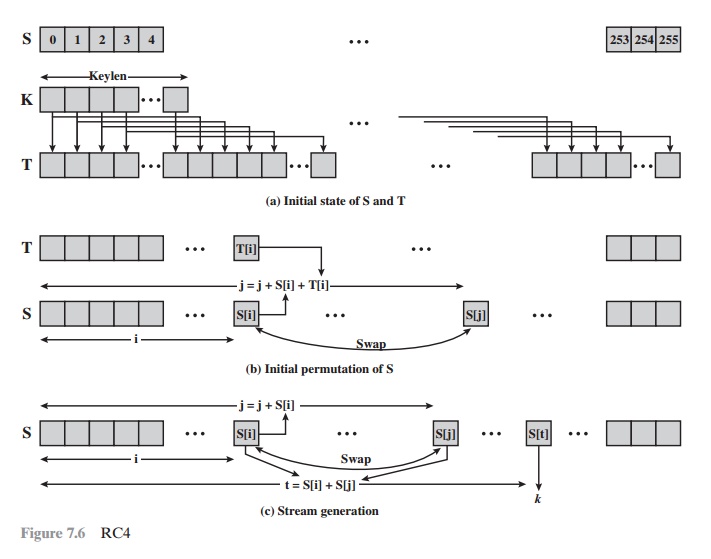
The RC4 algorithm is remarkably simple and
quite easy to explain. A vari- able-length key of from 1 to 256 bytes (8 to 2048 bits) is used to initialize a 256-byte
state vector S, with elements S[0],
S[1], Á , S[255]. At all times,
S contains a permu-
tation of all 8-bit numbers from 0 through 255. For encryption and decryption, a byte k (see Figure 7.5) is generated from S by selecting one of the 255
entries in a systematic fashion. As each value of k is generated, the entries in S are once again permuted.
Initialization of S
To begin, the
entries of S are set
equal to the
values from 0 through 255
in ascending order; that is, S[0] = 0, S[1] = 1, Á , S[255] = 255 . A temporary
vector, T, is also
created. If the length of the key K is 256 bytes,
then T is transferred to T. Otherwise, for a key of length keylen bytes, the first keylen elements of T are copied from K,
and then K is repeated
as many times
as necessary to fill out T. These
preliminary operations can be summarized as
/* Initialization
*/ for i = 0 to 255 do S[i] = i;
T[i] = K[i mod keylen];
Next we use T to produce the initial
permutation of S. This involves starting with S[0] and going through to S[255],
and for each S[i], swapping S[i] with another byte in S according to a scheme
dictated by T[i]:
/* Initial
Permutation of S */ j = 0;
for i = 0 to
255 do
j = (j + S[i] + T[i]) mod 256;
Swap (S[i], S[j]);
Because the only operation
on S is a swap, the only effect is a
permutation.
S still contains all the numbers from 0
through 255.
Stream Generation
Once the S vector is initialized, the input key is no longer used. Stream generation involves cycling through all the elements
of S[i], and for each S[i], swapping
S[i] with another byte in S according to a scheme dictated by the current
configuration of S. After
S[255] is reached,
the process continues, starting over again
at S[0]:
/* Stream
Generation */ i, j = 0;
while (true)
i = (i + 1) mod 256;
j = (j + S[i]) mod 256;
Swap (S[i], S[j]);
t = (S[i] + S[j]) mod 256; k = S[t];
To encrypt, XOR the value
k
with the next byte of plaintext. To decrypt,
XOR the value k with
the next byte of ciphertext.
Figure 7.6 illustrates the RC4 logic.
Strength of RC4
A number of papers have been
published analyzing methods of attacking
RC4 (e.g., [KNUD98],
[MIST98], [FLUH00], [MANT01]). None of these
approaches is practical against
RC4 with a reasonable key length, such
as 128 bits. A more serious
problem is reported in [FLUH01]. The authors demonstrate that the WEP proto- col, intended
to provide confidentiality on 802.11 wireless LAN networks, is vulnerable to a particular attack
approach. In essence,
the problem is not with RC4
itself but the way in which keys are generated for use as input to RC4. This partic-
ular problem does not appear to be relevant to other applications using
RC4 and
can be remedied in WEP by
changing the way in which keys are generated. This problem points out the
difficulty in designing a secure system that involves both cryptographic
functions and protocols that make use of them.
Related Topics