Chapter: Cryptography and Network Security Principles and Practice : System Security : Intruders
Intruders: Behavior Patterns and Techniques
INTRUDERS
One of the two most publicized threats to security is the
intruder (the other is viruses), often referred to as a hacker or cracker. In
an important early study of intrusion, Anderson [ANDE80] identified three
classes of intruders:
•
Masquerader: An individual who is not authorized to use the computer
and who penetrates a system’s access
controls to exploit
a legitimate user’s
account
•
Misfeasor: A legitimate user
who accesses data, programs, or resources for
which such access is not authorized, or who is authorized for such access but
misuses his or her privileges
•
Clandestine user: An individual who seizes supervisory control of the system
and uses this control to evade auditing
and access controls
or to suppress audit
collection
The masquerader is likely to be an outsider;
the misfeasor generally is an insider; and the clandestine user can be either
an outsider or an insider.
Intruder attacks range from the benign to the serious.
At the benign end of the
scale, there are many people who simply wish to explore internets and see what
is out there. At the serious end are individuals who are attempting to read privileged
data, perform unauthorized modifications to data, or disrupt the system.
[GRAN04] lists the following examples
of intrusion:
•
Performing a remote root compromise of an e-mail server
•
Defacing a Web server
•
Guessing and cracking passwords
•
Copying a database containing credit card numbers
•
Viewing sensitive
data, including payroll records and medical information,
without authorization
•
Running a packet
sniffer on a workstation to capture usernames and pass- words
•
Using a permission
error on an anonymous FTP server to distribute pirated software and
music files
•
Dialing into an unsecured modem and gaining
internal network access
•
Posing as an executive, calling the help desk, resetting
the executive’s e-mail password, and learning the new password
•
Using an unattended, logged-in workstation without permission
Intruder Behavior Patterns
The techniques and behavior patterns
of intruders are constantly shifting,
to exploit newly discovered
weaknesses and to evade detection and countermeasures. Even so, intruders typically follow one of a number
of recognizable behavior
patterns, and these patterns
typically differ from those of ordinary users.
In the following, we look at three broad examples of intruder
behavior patterns, to give the reader some feel for the challenge facing the security
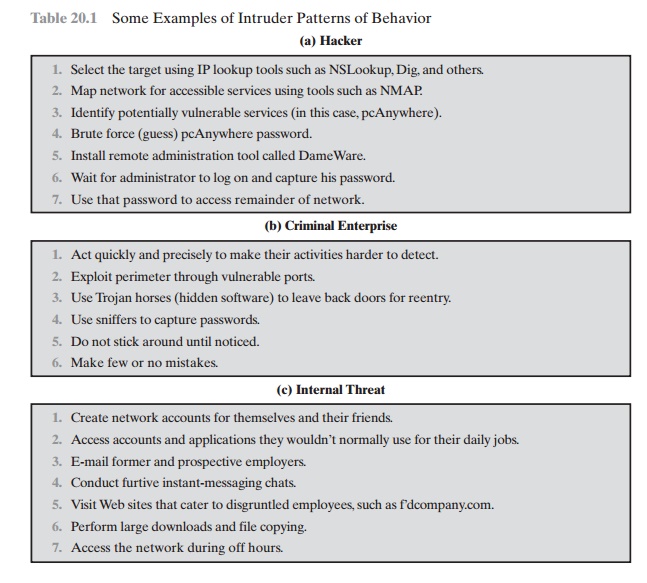
administrator. Table 20.1, based
on [RADC04], summarizes the behavior.
HACKERS Traditionally, those
who hack into computers do so for the thrill of it or for status. The hacking
community is a strong meritocracy in
which status is determined by level of competence.
Thus, attackers often look for targets
of opportunity and then share the
information with others. A typical example is a break-in at a large
financial institution reported in [RADC04]. The
intruder took advantage of the fact that the corporate
network was running
unprotected services, some of
which were not even needed. In this case, the key to the break-in was the
pcAnywhere application. The manufacturer, Symantec, advertises this program as a
remote control solution that enables secure connection to remote devices. But
the attacker had an easy time gaining access
to pcAnywhere; the administrator used the
same three-letter username
and password for the program.
In this case,
there was no intrusion detection system on the
700-node corporate network. The intruder was only discovered when a vice
president walked into her office and saw the cursor moving files
around on her Windows workstation.
Table 20.1 Some Examples of Intruder Patterns of Behavior
Benign intruders might
be tolerable, although
they do consume
resources and may slow performance for legitimate users. However,
there is no way in advance to know whether
an intruder will be benign or malign.
Consequently, even for systems with no particularly sensitive resources, there is a motivation to control this
problem. Intrusion detection systems (IDSs) and intrusion
prevention systems (IPSs)
are designed to counter this type of hacker threat.
In addition to using such systems,
organizations can consider
restricting remote logons
to specific IP addresses and/or use virtual private network
technology.
One of the results of the growing
awareness of the intruder problem
has been the establishment of
a number of computer emergency response teams (CERTs). These cooperative
ventures collect information about system vulnerabilities and disseminate it to systems managers. Hackers also routinely read CERT reports. Thus, it is important for system administrators to quickly insert
all software patches to discovered vulnerabilities. Unfortunately,
given the complexity of many IT systems,
and the rate at which patches are released, this is increasingly difficult to achieve without automated updating. Even then,
there are problems caused by incompatibilities resulting from the updated
software. Hence the need for multiple
layers of defense in managing
security threats to IT systems.
CRIMINALS Organized groups of hackers have become a widespread and
common threat to Internet-based systems. These groups can be in the employ of a
corpo- ration or government but often
are loosely affiliated gangs of hackers. Typically,
these gangs are young, often
Eastern European, Russian, or southeast
Asian hackers who do business
on the Web [ANTE06].
They meet in underground forums with names like DarkMarket.org and
theftservices.com to trade tips and data and coordinate attacks. A common
target is a credit card file at an e-commerce server. Attackers attempt to gain root access.
The card numbers are used by organized
crime gangs to purchase expensive
items and are then posted to carder sites, where others can access and use the
account numbers; this obscures usage patterns and complicates investigation.
Whereas traditional hackers look for targets
of opportunity, criminal hackers
usually have specific targets,
or at least classes of targets in mind. Once
a site is pene- trated, the attacker acts quickly,
scooping up as much valuable
information as possi- ble and exiting.
IDSs and IPSs can also be used for these
types of attackers, but may be less effective
because of the quick in-and-out nature
of the attack. For e-commerce sites, database encryption should
be used for sensitive customer
information, espe- cially
credit cards. For hosted e-commerce
sites (provided by an outsider service), the e-commerce organization should
make use of a dedicated server (not used to support multiple customers) and
closely monitor the provider’s security services.
INSIDER ATTACKS Insider attacks are among the most difficult
to detect and prevent.
Employees already have access and knowledge about the structure and content of
corporate databases. Insider
attacks can be motivated by revenge or simply a feeling
of entitlement. An example of the former is the case of Kenneth Patterson,
fired from his position as data communications manager for American Eagle Outfitters. Patterson disabled the
company’s ability to process credit card purchases during five days of the
holiday season of 2002. As for a sense of entitlement, there have
always been many employees who felt entitled to take extra office supplies for home use, but this now extends to corporate data. An example is that of a vice president of sales for a stock analysis firm who quit to go to a competitor. Before
she left, she copied
the customer database to take with
her. The offender reported feeling no animus toward her former employee; she simply wanted the data because
it would be useful to her.
Although IDS and IPS facilities can be
useful in countering insider attacks, other more direct approaches are of higher priority.
Examples include the following:
•
Enforce least
privilege, only allowing
access to the resources employees need to do their job.
•
Set logs to see what users
access and what commands they are entering.
•
Protect sensitive
resources with strong authentication.
•
Upon termination, delete employee’s computer
and network access.
•
Upon termination, make a mirror
image of employee’s hard drive before
reis- suing it. That evidence might be needed if your company information turns up at a competitor.
In this section,
we look at the techniques used for intrusion. Then we examine ways to detect intrusion.
Intrusion Techniques
The objective of the intruder
is to gain access to a system
or to increase the range
of privileges accessible on a system.
Most initial attacks
use system or software vulner- abilities that allow a user to
execute code that opens a back door into the system. Alternatively, the
intruder attempts to acquire information that should have been protected. In
some cases, this information is in the form of a user password. With knowledge
of some other user’s password, an intruder can log in to a system and exercise all the privileges accorded to the legitimate user.
Typically, a system must maintain a file that associates a password
with each authorized user.
If such a file is stored with no protection, then it is an easy matter to gain
access to it and learn
passwords. The password file can be protected in one of two ways:
•
One-way function: The system stores only
the value of a function based on the user’s password. When the user
presents a password, the system transforms that password and compares it with
the stored value. In practice, the system usually
performs a one-way transformation
(not reversible) in which the password is used to generate a key for
the one-way function and in which a fixed-length output is produced.
•
Access control: Access
to the password file is limited to one or a very few accounts.
If one or both of these countermeasures are in place,
some effort is needed for a potential intruder
to learn passwords. On the basis of a survey of the literature and interviews with a number of password crackers, [ALVA90]
reports the following techniques for learning passwords:
1.
Try
default passwords used with standard
accounts that are shipped with the system. Many administrators do not bother
to change these
defaults.
2.
Exhaustively try all short passwords (those of one to three characters).
3.
Try words in the system’s
online dictionary or a list of likely
passwords. Examples
of the latter are readily
available on hacker bulletin
boards.
4.
Collect information
about users, such as their full names, the names of their spouse and children, pictures
in their office, and books in their office
that are related to hobbies.
5.
Try users’ phone numbers, Social Security numbers, and room numbers.
6.
Try all legitimate license plate numbers for this state.
7.
Use a Trojan horse (described in Chapter
21) to bypass restrictions on access.
8.
Tap the line between
a remote user and the host system.
The first six methods are various
ways of guessing
a password. If an intruder
has to verify the guess by attempting to log in, it is a tedious and easily
countered means of attack. For example, a system can simply
reject any login after three password
attempts,
thus requiring the intruder to
reconnect to the host to try again. Under these circum- stances,
it is not practical to try more than a handful of passwords. However,
the intruder is unlikely to try such crude methods. For
example, if an intruder can gain access with a low level of privileges to an encrypted password file, then the strategy would be to capture
that file and then use the encryption mechanism of that particular system at leisure
until a valid password
that provided greater privileges was discovered. Guessing attacks
are feasible, and indeed highly effective, when a large num-
ber of guesses
can be attempted automatically and each guess
verified, without the guessing process being detectable. Later in this chapter, we have much to say about
thwarting guessing attacks.
The seventh method of attack listed earlier, the Trojan horse,
can be particularly difficult to counter.
An example of a program
that bypasses access
controls was cited in [ALVA90]. A low-privilege user produced a game program
and invited the system operator to use it in his or her spare time. The program
did indeed play a game, but in
the background it also contained code to copy the password file, which was
unen- crypted but access
protected, into the user’s
file. Because the game was running
under the operator’s high-privilege mode, it was
able to gain
access to the
password file.
The eighth attack listed, line tapping, is a
matter of physical security.
Other intrusion techniques do not require
learning a password. Intruders can get access to a system by exploiting attacks such as
buffer overflows on a program that runs with certain privileges. Privilege escalation
can be done this way as well.
We turn now to a discussion of the two principal countermeasures: detection
and prevention. Detection is concerned with learning of an attack, either
before or after its success.
Prevention is a challenging security
goal and an uphill battle
at all times. The difficulty stems from the fact that the defender
must attempt to thwart all possible attacks, whereas the
attacker is free to try to find the weakest link in the defense chain and
attack at that point.
Related Topics