Chapter: Cryptography and Network Security Principles and Practice : Mutual Trust : Key Management and Distribution
X.509 Certificates
X.509
CERTIFICATES
ITU-T recommendation X.509
is part of the X.500
series of recommendations that define a directory service. The directory is, in
effect, a server or distributed set of servers
that maintains a database of information about users. The information includes a mapping from user
name to network address, as well as other attributes and information about the users.
X.509 defines a framework for the provision
of authentication services by the
X.500 directory to its users. The directory may serve as a repository of
public-key certificates of the type discussed in Section 14.3.
Each certificate contains
the public key of a user and is signed with the private
key of a trusted certification authority. In
addition, X.509 defines alternative authentication protocols based on the use
of public-key certificates.
X.509 is an important standard
because the certificate structure and authenti- cation protocols defined in X.509 are used in a variety
of contexts. For example,
the X.509 certificate format
is used in S/MIME (Chapter
18), IP Security
(Chapter 19), and SSL/TLS
(Chapter 16).
X.509 was initially issued in 1988. The
standard was subsequently revised to address some of the security concerns
documented in [IANS90] and [MITC90]; a revised recommendation was issued in 1993.
A third version was issued in 1995 and revised in 2000.
X.509 is based on the use of public-key cryptography and digital signatures. The standard
does not dictate the use of a specific algorithm but recommends RSA.The
dig- ital signature
scheme is assumed
to require the use of a hash function.
Again, the stan- dard does not dictate a specific hash algorithm. The 1988 recommendation included the
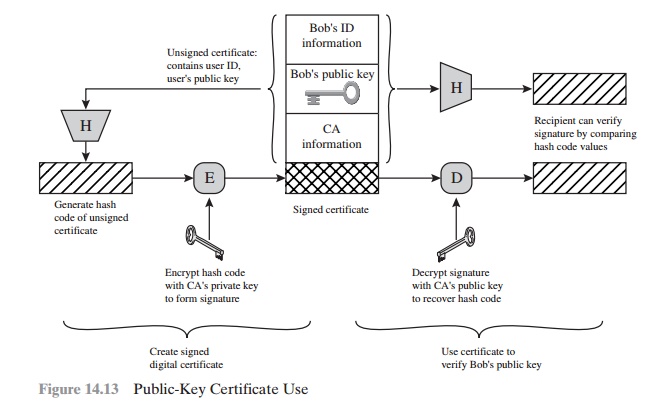
description of a recommended hash algorithm; this algorithm has since been shown to be insecure and was dropped from the 1993 recommendation. Figure 14.13 illustrates
the generation of a public-key certificate.
Certificates
The heart of the X.509 scheme is the
public-key certificate associated with each user. These user certificates are
assumed to be created by some trusted certifica- tion authority (CA) and placed
in the directory by the CA or by the user. The directory server itself is not
responsible for the creation of public keys or for the certification function;
it merely provides an easily accessible location for users to obtain
certificates.
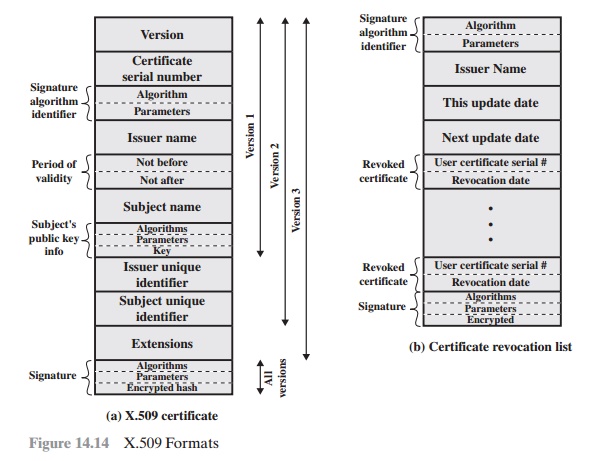
Figure 14.14a shows
the general format
of a certificate, which includes
the fol- lowing elements.
•
Version: Differentiates among successive versions of the certificate format;
the default is version
1. If the issuer unique identifier or subject unique identifier are present, the value
must be version
2. If one or more extensions are present,
the version must be version
3.
•
Serial number: An integer
value unique within
the issuing CA that is unam-
biguously associated with this certificate.
•
Signature algorithm identifier: The algorithm
used to sign the certificate
together with any associated
parameters. Because this
information is repeated in the signature
field at the end of the certificate, this field has little,
if any, utility.
•
Issuer name: X.500 is the name of the CA that created
and signed this certificate.
•
Period of validity: Consists of two
dates: the first and last on which the certifi- cate is valid.
•
Subject name: The name of the
user to whom
this certificate refers.
That is, this certificate certifies the public key of the subject who holds the corresponding
private key.
•
Subject’s public-key information: The public key of the subject, plus an identi- fier of the algorithm for which this key is to be used, together with any associ- ated parameters.
•
Issuer unique identifier: An optional-bit string
field used to identify uniquely the issuing CA in the event the X.500 name has been reused for different
entities.
•
Subject unique identifier: An optional-bit string
field used to identify uniquely the subject in the event the X.500 name has been reused for different entities.
•
Extensions: A set of one or more
extension fields. Extensions were
added in version 3 and are discussed
later in this section.
•
Signature: Covers all of the other
fields of the certificate; it contains the hash
code of the other fields
encrypted with the CA’s private key. This
field includes the signature
algorithm identifier.
The unique identifier fields were added in version 2 to handle
the possible reuse of subject and/or issuer names over time. These fields are
rarely used.
The standard uses the following notation to
define a certificate:
CA <<
A >> = CA {V, SN,
AI, CA, UCA, A, UA, Ap, TA}
where
Y<< X>> = the
certificate of user X issued by certification authority Y
Y {I} = the signing of I by Y. It consists
of I with an encrypted
hash code appended
V = version of the
certificate
SN = serial
number of the certificate
AI = identifier
of the algorithm used to sign the certificate
CA = name of certificate authority
UCA = optional unique identifier of the CA
A = name of user A
UA = optional unique identifier of the user A
Ap = public
key of user A
TA = period of validity of the certificate
The CA signs the certificate with its private key. If the corresponding public key is known to a user, then that user can verify that a certificate signed by the CA
is valid. This is the typical digital
signature approach illustrated in Figure 13.2.
OBTAINING A USER’S CERTIFICATE User certificates generated by a CA have the following
characteristics:
•
Any user with access
to the public key of the CA can verify
the user public
key that was certified.
•
No party
other than the certification authority can modify the certificate with- out this being detected.
Because certificates are unforgeable, they
can be placed in a directory without the need for the directory to make special
efforts to protect them.
If all users subscribe to the same CA, then there is a common trust of that CA. All
user certificates can be placed
in the directory for access
by all users. In addition, a user can transmit
his or her certificate directly
to other users.
In either case, once
B is
in possession of A’s certificate, B has confidence that messages it encrypts with A’s public key will be secure from eavesdropping and that messages
signed with A’s private
key are unforgeable.
If there is a large community of users, it
may not be practical for all users to subscribe to the same CA. Because it is
the CA that signs certificates, each par- ticipating user must have a copy of
the CA’s own public key to verify signatures. This public key must be provided
to each user in an absolutely secure (with respect to integrity and
authenticity) way so that the user has confidence in the associated
certificates. Thus, with many users, it may be more practical for there to be a
number of CAs, each of which securely provides its public key to some fraction
of the users.
Now suppose that A has obtained a certificate from certification authority
X1 and B has obtained a certificate from CA X2. If A does not securely know the pub- lic
key of X2, then
B’s certificate, issued
by X2, is useless to A. A can read B’s certifi- cate, but A cannot verify the signature. However, if the two CAs have securely
exchanged their own public keys, the
following procedure will enable A to obtain B’s public key.
Step 1 A obtains from the directory
the certificate of X2 signed by X1. Because A securely knows X1’s public
key, A can obtain
X2’s public
key from its cer-
tificate and verify it by means of X1’s signature on the certificate.
Step 2 A then goes back to the directory
and obtains the certificate of B signed by
X2. Because
A now has a trusted
copy of X2’s public key, A can verify
the signature and securely
obtain B’s public
key.
A has used a chain of certificates to obtain
B’s public key. In the notation of X.509, this chain is expressed as
X1 << X2 >> X2 << B >>
In the same fashion, B can obtain A’s public
key with the reverse chain:
X2 << X1 >> X1 << A >>
This scheme need not be limited to a chain
of two certificates. An arbitrarily long path of CAs can be followed to produce
a chain. A chain with N elements would be
expressed as
X1 << X2 >> X2 << X3 >> Á XN << B >>
In this case,
each pair of CAs in the chain (Xi, Xi+1) must have created
certifi- cates for each other.
All these certificates of CAs by CAs need to
appear in the directory, and the user needs to know how they are linked to
follow a path to another user’s public- key
certificate. X.509 suggests
that CAs be arranged in a hierarchy so that naviga- tion is straightforward.
Figure 14.15, taken from X.509, is an
example of such a hierarchy. The
con- nected circles indicate the hierarchical relationship among the CAs; the associated boxes indicate certificates maintained in the directory for each CA entry.
The direc- tory entry for each CA includes two types of certificates:
•
Forward certificates: Certificates of X generated by other CAs
•
Reverse certificates: Certificates
generated by X that are the certificates of other CAs
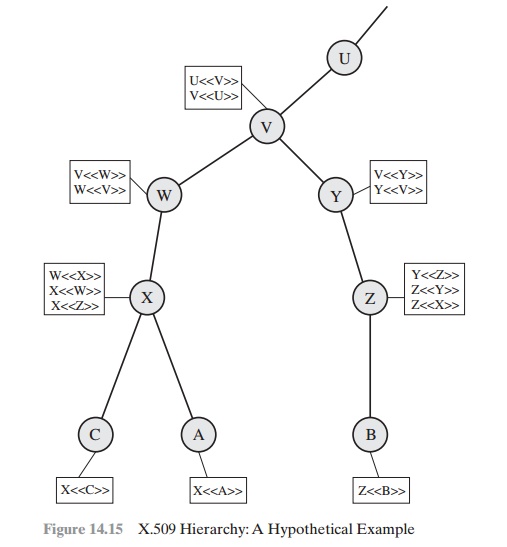
In this example, user A can acquire the following
certificates from the direc- tory to establish a certification path to B:
X <<
W >> W << V W << << Y >> Y << Z >> Z << B >>
When A has obtained these
certificates, it can unwrap the certification path in
sequence to recover a trusted copy of B’s public key. Using this public key, A
can send encrypted messages
to B. If A wishes to receive encrypted messages back from B,
or to sign messages sent to B, then
B will require A’s public key, which can be obtained from the following certification path:
Z <<
Y >> Y << V >> << W >> W << X >> X << A >>
B can obtain this set of certificates from the directory, or A can provide them as
part of its initial message
to B.
REVOCATION OF CERTIFICATES Recall from Figure 14.14 that each certificate includes a period of validity, much like a credit card. Typically, a new certificate is issued just before the expiration of the old one. In addition, it may be desirable on occasion to revoke
a certificate before it expires, for one of the following reasons.
1.
The user’s private key is assumed
to be compromised.
2.
The user is no longer
certified by this CA. Reasons
for this include
that the sub- ject’s name has changed,
the certificate is superseded, or the certificate was not issued in conformance with the CA’s policies.
3.
The CA’s certificate is assumed to be compromised.
Each CA must maintain a list consisting of all revoked
but not expired
certifi- cates issued by that CA, including
both those issued to users and
to other CAs. These lists should also be posted on the directory.
Each certificate revocation list (CRL) posted
to the directory is signed
by the issuer and includes (Figure
14.14b) the issuer’s
name, the date the list was created, the date the next CRL is scheduled to be issued,
and an entry for each revoked cer- tificate. Each entry consists
of the serial number of a certificate and revocation date for
that certificate. Because
serial numbers are unique within
a CA, the serial num- ber
is sufficient to identify the certificate.
When a user
receives a certificate in a message, the user must determine whether
the certificate has been revoked. The user
could check the directory each time a certificate is received. To avoid
the delays (and possible costs)
associated with directory
searches, it is likely that the user would maintain a local cache of certifi- cates and lists of revoked certificates.
X.509 Version 3
The X.509
version 2 format does not convey
all of the information that recent design and implementation experience has shown to be needed.
[FORD95] lists the following requirements not satisfied by version 2.
1.
The subject field is inadequate to convey the identity of a key owner to a public-key user. X.509 names may be relatively short and lacking
in obvious identification
details that may be needed by the user.
2.
The subject field is also inadequate for many applications, which typically recog-
nize entities by an Internet
e-mail address, a URL, or some other Internet-related
identification.
3.
There is a need to indicate
security policy information. This enables a security
application or function, such as IPSec,
to relate an X.509 certificate to a given policy.
4.
There is a need to limit the damage
that can result
from a faulty
or malicious CA by setting
constraints on the applicability of a particular certificate.
5.
It is important to be able to identify
different keys used by the same owner
at different times. This feature supports
key lifecycle management: in particular, the
ability to update key pairs for users and CAs on a regular basis or under exceptional circumstances.
Rather than continue to add fields to
a fixed format, standards developers felt that
a more flexible approach was needed. Thus, version
3 includes a number of optional extensions that may be added to the version 2 format.
Each extension consists
of an extension identifier, a criticality indicator, and an extension value. The criticality
indicator indicates whether an extension
can be safely ignored. If the
indicator has a value of TRUE and an implementation does not recognize
the extension, it must treat
the certificate as invalid.
The certificate extensions fall into three main categories: key and policy infor-
mation, subject and issuer attributes, and certification path constraints.
KEY AND POLICY INFORMATION These extensions convey additional information about the
subject and issuer keys, plus
indicators of certificate policy. A certificate policy is a named set of
rules that indicates the applicability of a certificate to a particular community and/or class of application with common security requirements. For example, a policy might be applicable
to the authentication of electronic data interchange (EDI) transactions for the
trading of goods within a given price range.
This area includes:
•
Authority key identifier: Identifies the public key to
be used to verify the signature on
this certificate or CRL. Enables
distinct keys of the same CA to
be differentiated. One use of
this field is to handle
CA key pair updating.
•
Subject key identifier: Identifies the
public key being
certified. Useful for
sub- ject key pair updating. Also,
a subject may have multiple
key pairs and, corre-
spondingly, different certificates for different purposes
(e.g., digital signature and
encryption key agreement).
•
Key usage: Indicates
a restriction imposed as to the purposes for which, and the policies under
which, the certified public key may be used. May indicate one or more of the
following: digital signature, nonrepudiation, key encryp- tion, data encryption, key agreement, CA signature verification on certificates, CA signature
verification on CRLs.
•
Private-key usage period: Indicates the period
of use of the private
key corre- sponding to the
public key. Typically, the private
key is used over a different period from the validity of the public key. For example, with digital signature keys, the usage period for the signing
private key is typically shorter
than that for the
verifying public key.
•
Certificate policies: Certificates may be used in environments where multiple
policies apply. This extension lists policies that the certificate is recognized as supporting, together with optional
qualifier information.
•
Policy mappings: Used only in certificates
for CAs issued by other CAs. Policy mappings allow an issuing CA to
indicate that one or more of that issuer’s policies can be considered
equivalent to another policy used in the subject CA’s domain.
CERTIFICATE SUBJECT AND ISSUER ATTRIBUTES These extensions support
alternative names, in alternative formats, for a certificate subject or
certificate issuer and can convey additional information about the certificate
subject to increase a certificate
user’s confidence that the certificate subject is a particular person or
entity. For example, information such as postal address, position within a corporation, or picture image
may be required.
The extension fields in this area include:
•
Subject alternative name: Contains one or more alternative names, using any of
a variety of forms. This
field is important for supporting certain
applications, such as electronic mail, EDI, and IPSec, which may employ
their own name forms.
•
Issuer alternative name: Contains one or more alternative names, using any
of a variety of forms.
•
Subject directory attributes: Conveys
any desired X.500 directory attribute values for the subject of this certificate.
CERTIFICATION PATH CONSTRAINTS These extensions allow constraint specifications to be included in certificates issued for CAs by other
CAs. The constraints may restrict the types of certificates that
can be issued by the subject CA or that may occur subsequently in a certification chain.
The extension fields in this area include:
•
Basic constraints: Indicates if the subject
may act as a CA. If so, a certification
path length constraint may be specified.
•
Name constraints: Indicates a name space within which all subject
names in subsequent certificates in a certification path must be located.
•
Policy constraints: Specifies constraints that may require
explicit certificate policy identification or inhibit policy
mapping for the remainder of the certifi- cation path.
Related Topics