Chapter: Cryptography and Network Security Principles and Practice : Legal And Ethical Aspects
Network and Computer Privacy
PRIVACY
An issue with considerable overlap
with computer security
is that of privacy.
On the one hand, the scale and interconnectedness of personal
information collected and stored in information systems has increased dramatically, motivated by law enforce- ment, national security, and
economic incentives. The last mentioned has been perhaps the main driving
force. In a global information economy, it is likely that the most economically valuable electronic asset
is aggregations of information on individ-
uals [JUDY09]. On the other hand,
individuals have become
increasingly aware of the extent
to which government agencies, businesses, and
even Internet users
have access to their personal
information and private
details about their
lives and activities.
Concerns about the extent to which personal
privacy has been and may be compromised have led to a variety of legal and technical approaches to reinforcing privacy rights.
Privacy Law and Regulation
A number of
international organizations and national governments have intro- duced laws and regulations intended
to protect individual privacy. We look at two such initiatives in this
subsection.
EUROPEAN
UNION
DATA PROTECTION DIRECTIVE In 1998, the EU adopted
the
Directive on Data Protection to both (1)
ensure that member states protected fundamental privacy rights when processing personal
information, and (2) prevent
member states from restricting the free flow of personal
information within the EU. The Directive
is not itself a law, but requires member states to enact laws
encompassing its terms.
The Directive is organized
around the following
principles of personal information use:
•
Notice: Organizations must notify
individuals what personal
information they are
collecting, the uses of that information, and what choices the individual may have.
•
Consent: Individuals must be able to choose whether
and how their
personal information is used by, or disclosed
to, third parties. They have the right not to
have any sensitive information collected
or used without express permission, including race,
religion, health, union
membership, beliefs, and
sex life.
•
Consistency: Organizations may use personal information only in accordance with the terms of the
notice given the data
subject and any choices with
respect to its use exercised by the subject.
•
Access: Individuals must have the right and ability
to access their information
and correct, modify, or delete any portion of it.
•
Security: Organizations must provide adequate security, using technical and
other means, to protect the
integrity and confidentiality
of personal information.
•
Onward transfer: Third parties
receiving personal information must provide the same level of privacy protection as the organization from whom the infor-
mation is obtained.
•
Enforcement: The Directive grants
a private right of action to data subjects when
organizations do not follow the
law. In addition, each EU member
has a regulatory enforcement agency concerned with
privacy rights enforcement.
UNITED STATES
PRIVACY INITIATIVES The first comprehensive privacy legislation adopted in the United States was the Privacy
Act of 1974, which dealt with personal information collected
and used by federal agencies.
The Act is intended
to
1.
Permit individuals to determine what records pertaining to them are collected,
maintained, used, or disseminated.
2.
Permit individuals
to forbid records obtained for one purpose to be used for another purpose without consent.
3.
Permit individuals to obtain access to records pertaining to them and
to correct
and amend such records
as appropriate.
4.
Ensure that agencies collect, maintain, and use personal
information in a manner
that ensures that the information is current,
adequate, relevant, and not excessive
for its intended use.
5.
Create a private
right of action for individuals whose personal information is not
used in accordance with the Act.
As with all privacy laws and regulations,
there are exceptions and conditions
attached to this Act, such as criminal
investigations, national security
concerns, and conflicts between
competing individual rights
of privacy.
While the 1974
Privacy Act covers
government records, a number of other U.S. laws have been enacted
that cover other
areas, including the following:
•
Banking and financial
records: Personal banking information is protected in certain
ways by a number of laws, including the
recent Financial Services Modernization Act.
•
Credit reports: The Fair Credit Reporting Act confers certain rights on indi- viduals and obligations on credit reporting agencies.
•
Medical and health
insurance records: A variety
of laws have
been in place
for decades dealing with medical
records privacy. The Health Insurance Portability and Accountability Act (HIPPA)
created significant new rights for patients to protect and access their
own health information.
•
Children’s privacy: The Children’s Online Privacy Protection Act places
restrictions on online organizations in the collection of data from
children under the age of 13.
•
Electronic
communications: The Electronic
Communications Privacy Act generally prohibits unauthorized and intentional
interception of wire and electronic communications during the
transmission phase and unauthorized accessing
of electronically stored
wire and electronic communications.
Organizational Response
Organizations need to deploy both management controls
and technical measures
to comply with laws and regulations concerning privacy as well as to implement corpo- rate policies
concerning employee privacy. ISO 17799 (Code of Practice
for Information Security Management) states the
requirement as follows:
ISO
17799: Data protection and privacy of personal information
An organizational data protection and privacy policy
should be developed and implemented. This policy should be communicated to all persons
involved in the processing of personal information. Compliance with this policy and all relevant data protection legislation and
regulations requires appropriate management structure
and control. Often this is best
achieved by the appointment of a responsible person, such
as a data protection officer, who should provide guid- ance to managers, users,
and service providers on their individual responsibilities and the specific
procedures that should be followed.
Responsibility for handling personal information and ensuring
awareness of the data protection principles should
be dealt with in accordance with relevant legislation and
regulations. Appropriate technical and organizational measures
to protect personal
informa- tion should be implemented.
Privacy and Data Surveillance
The demands of homeland security
and counterterrorism have imposed new threats
to personal privacy. Law enforcement
and intelligence agencies have become
increasingly aggressive in using data surveillance techniques to fulfill their
mission. In addition, private
organization are exploiting a number of trends to increase their ability to build detailed
profiles of individuals, including the spread of the Internet,
the increase in electronic payment methods, near-universal use of cellular
phone communications, ubiquitous computation, sensor webs, and so on.
Both policy and technical approaches are needed to protect privacy
when both government and
nongovernment organizations seek to learn as much as possible about
individuals. In terms of technical approaches, the requirements for privacy protection for information systems can be addressed
in the context of database security. That is, the approaches that are appropriate for privacy protection involve technical means that have been developed for database security.
A specific proposal for a database security
approach to privacy protection is outlined in [POPP06]
and illustrated in Figure 23.5. The privacy appliance
is a tam- per-resistant, cryptographically protected
device that is interposed between
a data- base and the access
interface, analogous to a firewall
or intrusion prevention device. The device implements privacy
protection functions, including
verifying the user’s access permissions and credentials
and creating an audit log. Some of the specific functions of the appliance
are as follows:
•
Data transformation: This function encodes or encrypts portions of the
data so as to preserve privacy
but still allow data analysis
functions needed for effec-
tive use. An example of such data analysis functions is the detection of terror- ist activity
patterns.
•
Anonymization: This function removes
specific identifying information from query results, such as last name and telephone number, but
creates some sort of anonymized unique identifier so that analysts can detect connections between queries.
•
Selective revelation: This is a method for minimizing exposure
of individual information while enabling continuous analysis of potentially interconnected data. The function initially
reveals information to the analyst
only in sanitized form, that is, in terms of statistics and categories that do not reveal (directly
or indirectly) anyone’s private
information. If the analyst sees reason for concern, he or she can follow up by seeking permission to get
more precise information. This permission would be granted if the initial information
provides sufficient cause to allow the revelation of more information,
under appropriate legal and
policy guidelines.
•
Immutable audit: A tamper-resistant method that identifies where data go and
who has seen the data. The audit
function automatically and permanently
records all data
accesses, with strong
protection against deletion, modification, and unauthorized use.
•
Associative memory: This is a software module that can recognize patterns and
make connections between pieces of data that the human user may have missed or didn’t know existed. With this method,
it can discover relationships
quickly between data points found
in massive amounts
of data.
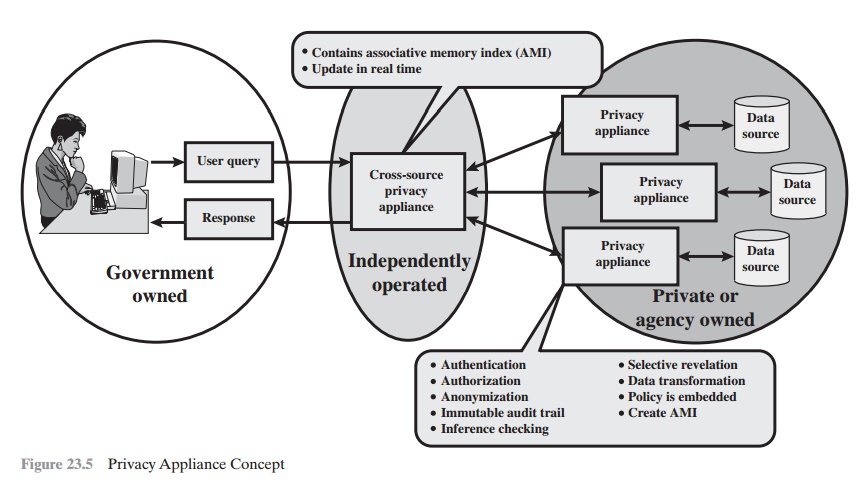
As Figure 23.5 indicates, the owner of a database
installs a privacy
appliance tailored to the database content and structure and to its
intended use by outside organizations. An independently operated privacy appliance can interact with multi-
ple databases from multiple organizations to collect and interconnect data for their ultimate use by law enforcement, an intelligence user,
or other appropriate user.
Related Topics