Chapter: Cryptography and Network Security Principles and Practice : Legal And Ethical Aspects
Intellectual Property
INTELLECTUAL PROPERTY
The U.S. legal system, and legal systems generally,
distinguish three primary types of property:
•
Real property: Land and things permanently attached to
the land, such as trees, buildings, and
stationary mobile homes.
•
Personal property: Personal effects, moveable
property and goods, such as cars, bank
accounts, wages, securities, a small business,
furniture, insurance policies, jewelry, patents, pets, and season baseball tickets.
•
Intellectual property: Any intangible asset that consists of human knowledge and ideas. Examples include software, data,
novels, sound recordings, the design of a new type of mousetrap, or a cure for a disease.
This section focuses on the computer
security aspects of intellectual property.
Types of Intellectual Property
There are three main
types of intellectual property for which
legal protection is avail-
able: copyrights, trademarks, and
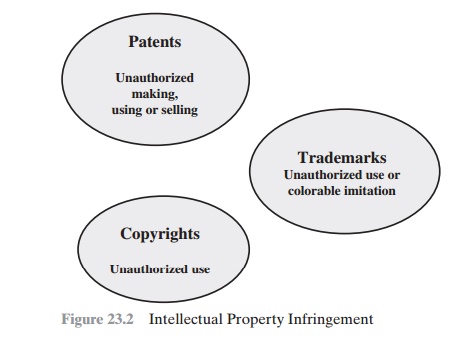
patents. The legal protection is against infringement, which is the invasion of the rights
secured by copyrights, trademarks, and patents.
The right to seek civil recourse
against anyone infringing his or her prop-
erty is granted to the IP owner. Depending upon the type of IP, infringement may vary (Figure 23.2).
COPYRIGHTS Copyright law protects the tangible or fixed expression of an idea, not the idea itself. A creator can claim copyright, and file for the copyright at a national government copyright office, if the following conditions are fulfilled:4
•
The proposed work is original.
•
The creator has put this
original idea into a concrete form, such as hard copy (paper), software, or multimedia form.
Examples
of items that may be copyrighted include
the following [BRAU01]:
•
Literary works: Novels, nonfiction prose, poetry,
newspaper articles and
news- papers, magazine articles and magazines, catalogs, brochures, ads
(text), and compilations such
as business directories
•
Musical works: Songs, advertising jingles, and instrumentals
•
Dramatic works: Plays, operas,
and skits
•
Pantomimes and choreographic works: Ballets, modern dance,
jazz dance, and mime
works
•
Pictorial, graphic, and sculptural works: Photographs, posters, maps, paintings, drawings, graphic art, display ads, cartoon strips and cartoon
characters, stuffed animals, statues, paintings, and works of fine art
•
Motion pictures and other audiovisual
works: Movies, documentaries, travel- ogues, training films and videos,
television shows, television ads, and
interac- tive multimedia works
•
Sound recordings: Recordings of music, sound, or words
•
Architectural works: Building
designs, whether in the form of architectural
plans, drawings, or the constructed building itself
•
Software-related works: Computer software, software documentation and
manuals, training manuals, other
manual
The copyright owner has the following
exclusive rights, protected against infringement:
•
Reproduction right: Lets the owner make
copies of a work
•
Modification right: Also known
as the derivative-works right, concerns modi- fying a work to create a new or derivative work
•
Distribution right: Lets the owner
publicly sell, rent, lease, or lend copies of the work.
•
Public-performance right: Applies
mainly to live performances
•
Public-display right: Lets the owner
publicly show a copy of the work directly or by means of a film, slide, or
television image
PATENTS A patent for an invention is the grant of a property right
to the inventor. The right conferred by the patent grant is, in the language of the U.S. statute
and of the grant itself, “the right to exclude others from making,
using, offering for sale, or selling” the invention in the United
States or “importing” the invention into the United States. Similar wording appears
in the statutes of other nations. There are three types of patents:
•
Utility patents: May be granted to anyone who invents or discovers any new
and useful process, machine, article
of manufacture, or composition of matter,
or any new and useful
improvement thereof;
•
Design patents: May be granted to
anyone who invents a new, original,
and ornamental design for an article
of manufacture; and
•
Plant patents: May be granted to anyone who invents or discovers and asexu-
ally reproduces any distinct and new variety
of plant.
An example of a patent from the computer
security realm is the RSA public-
key cryptosystem. From the time it was granted in 1983 until the patent expired in 2000,
the patent holder,
RSA Security, was entitled
to receive a fee for each imple- mentation of RSA.
TRADEMARKS A trademark is a word, name, symbol, or device that is
used in trade with goods to indicate
the source of the goods and to distinguish them from the goods of others. A servicemark is the same as a trademark
except that it identifies and distinguishes the source of a service
rather than a product. The terms
trademark and mark are
commonly used to refer to both
trademarks and servicemarks. Trademark rights may be used to prevent
others from using a confusingly similar mark, but not to prevent others from
making the same goods or from selling the same
goods or services
under a clearly different mark.
Intellectual Property Relevant to Network and Computer Security
A number of forms of intellectual property
are relevant in the context of network and computer security. Here we mention
some of the most prominent:
•
Software: This includes programs produced by vendors
of commercial software (e.g., operating systems, utility
programs, applications) as well as shareware,
proprietary software created
by an organization for internal
use, and software produced by individuals. For all
such software, copyright protection is available if desired. In some cases,
a patent protection may also be appropriate.
•
Databases: A database may
consist of data that is collected and organized
in such a fashion that it has potential commercial value. An example
is an eco- nomic forecasting database.
Such databases may be protected
by copyright.
•
Digital
content: This category includes audio files, video files,
multimedia, courseware, Web site content, and any other original
digital work that can be presented in some fashion
using computers or other digital
devices.
•
Algorithms: An example of a
patentable algorithm, previously cited,
is the
RSA public-key cryptosystem.
Digital Millennium Copyright Act
The U.S. Digital Millennium Copyright Act (DMCA)
has had a profound effect
on the protection of digital content
rights in both the United States and worldwide. The DMCA,
signed into law in 1998, is designed to implement World Intellectual Property
Organization (WIPO) treaties, signed in 1996. In essence, DMCA strengthens the
protection of copyrighted materials in digital format.
The DMCA encourages copyright owners to use
technological measures to protect copyrighted works. These measures fall into
two categories: measures that
prevent access to the work and measures
that prevent copying
of the work. Further, the law prohibits attempts
to bypass such measures. Specifically, the law states that
“no person shall circumvent a technological measure
that effectively controls
access to a work protected under
this title.” Among other
effects of this clause, it prohibits
almost all unauthorized decryption of content. The law further prohibits
the manu- facture, release,
or sale of products, services, and devices that can crack encryption
designed to thwart either access to or copying
of material unauthorized by the copyright holder. Both criminal
and civil penalties apply to attempts
to circumvent technological measures
and to assist in such circumvention.
Certain actions are exempted from the
provisions of the DMCA and other copyright
laws, including the following:
•
Fair use: This concept is not tightly
defined. It is intended to permit others
to perform, show, quote, copy, and otherwise distribute portions of
the work for certain purposes. These purposes include
review, comment,
and discussion of copyrighted works.
•
Reverse engineering: Reverse engineering of a software
product is allowed
if the user has the right to use a copy of the program and if the
purpose of the reverse engineering is not to duplicate the functionality of the
program but rather to achieve interoperability.
•
Encryption research: “Good faith”
encryption research is allowed. In essence,
this exemption allows decryption attempts to
advance the development of encryption technology.
•
Security testing: This is the access
of a computer or network for the good faith testing, investigating, or
correcting a security flaw or vulnerability, with the authorization of the
owner or operator.
•
Personal privacy: It is generally permitted to bypass technological measures if that is the only reasonable way to prevent
the access to result in the revealing or recording of personally identifying information.
Despite the exemptions built into the Act, there
is considerable concern,
espe- cially in the
research and academic communities, that the
act inhibits legitimate secu- rity and encryption research. These parties feel that DMCA stifles innovation and academic
freedom and is a threat to open source software development [ACM04].
Digital Rights Management
Digital Rights Management (DRM) refers to systems and
procedures that ensure that holders of digital rights are clearly identified
and receive the stipulated pay- ment for their works. The systems
and procedures may also impose further restric- tions on the use of digital
objects, such as inhibiting printing
or prohibiting further distribution.
There is no single
DRM standard or architecture. DRM encompasses a variety
of approaches to intellectual property management and enforcement by providing
secure and trusted automated
services to control the distribution and use of content. In general,
the objective is to provide
mechanisms for the complete content management
life cycle (creation, subsequent contribution by others,
access, distribution, use), includ-
ing the management of rights information associated with the content.
DRM systems should meet the following
objectives:
1.
Provide
persistent content protection against unauthorized access to the digital content,
limiting access to only those
with the proper
authorization.
2.
Support a variety
of digital content
types (e.g., music files, video streams, digital
books, images).
3.
Support content
use on a variety of platforms, (e.g., PCs, PDAs, iPods, mobile phones).
4.
Support
content distribution on a variety of media, including CD-ROMs, DVDs, and flash memory.
Figure 23.3, based
on [LIU03], illustrates a typical DRM model in terms of the
principal users of DRM systems:
Content provider: Holds the digital
rights of the content and wants to protect
these rights. Examples are a music record label and a movie studio.
Distributor: Provides distribution channels, such as an online shop or a Web retailer. For example, an online distributor receives the digital content from
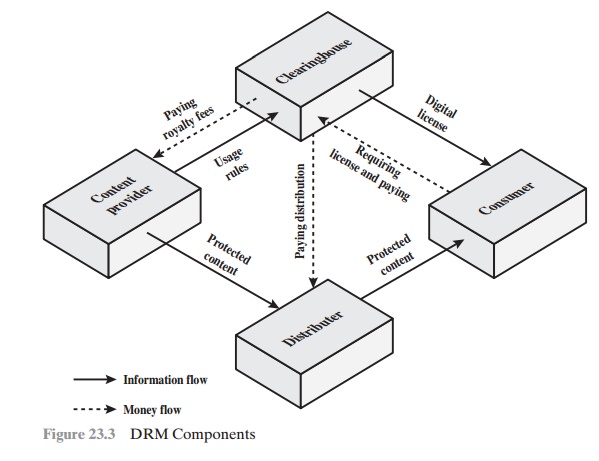
the content provider and creates a Web
catalog presenting the content and rights metadata for the content promotion.
•
Consumer: Uses the system to access the digital
content by retrieving down- loadable or streaming content through the distribution
channel and then pay- ing for the digital
license. The player/viewer application used by the consumer
takes charge of initiating license request to the clearinghouse and enforcing
the content usage rights.
•
Clearinghouse: Handles the financial transaction for issuing
the digital license to the consumer and pays royalty
fees to the content provider
and distribution fees to the
distributor accordingly. The clearinghouse is also responsible for logging license
consumptions for every
consumer.
In this model, the distributor need not
enforce the access rights. Instead, the content provider protects the content
in such a way (typically encryption) that the consumer must purchase a digital
license and access capability from the clearing- house. The clearinghouse consults usage rules provided by the content
provider to determine what access is permitted and
the fee for a particular type of
access. Having collected the fee, the clearinghouse credits
the content provider
and distrib- utor appropriately.
Figure 23.4, from [IANN06], shows a generic system
architecture to support DRM functionality. The system is access by parties in
three roles. Rights holders are the content providers, who either created the content
or have acquired rights to the content. Service providers include distributors and clearinghouses. Consumers
are
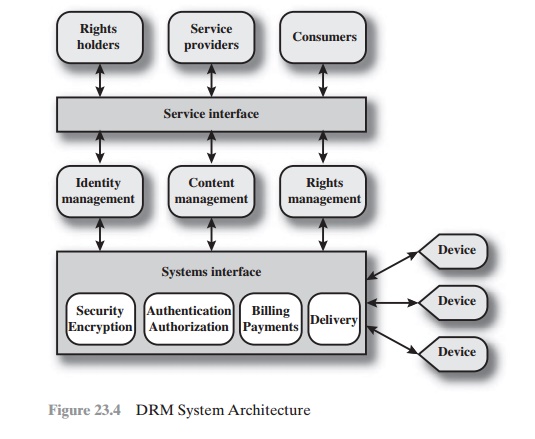
those who purchase the right to access to
content for specific uses. There is system interface to the services provided
by the DRM system:
•
Identity
management: Mechanisms to
uniquely identify entities, such
as parties and content
•
Content management: Processes and functions needed
to manage the content
lifestyle
•
Rights management: Processes and
functions needed to manage rights,
rights holders, and associated requirements
Below these management
modules are a set of common functions.
The security/encryption
module provides
functions to encrypt content and to sign license
agreements. The identity management service makes use of the
authentication and authorization functions to identify all parties in the relationship. Using these
functions, the identity
management service includes
the following:
•
Allocation of unique party
identifiers
•
User profile and preferences
•
User’s device
management
•
Public-key management
Billing/payments functions deal with the collection of usage fees from con-
sumers and the distribution of payments to rights holders
and distributors. Delivery functions deal with the delivery
of content to consumers.
Related Topics