Chapter: Security in Computing : The Economics of Cybersecurity
Making a Business Case
Making a Business Case
There are many reasons why
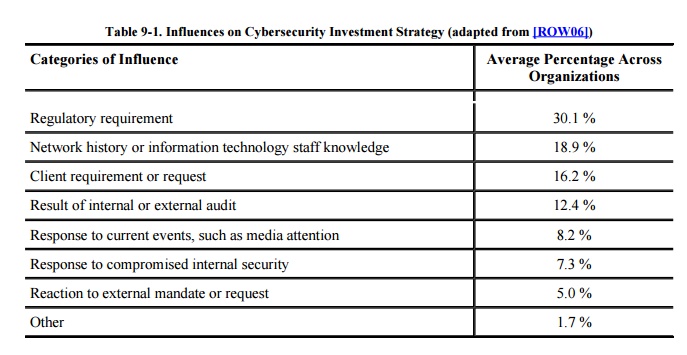
companies look carefully at their investments in cybersecurity. Table 9-1 shows the results of a series of
in-depth interviews with organizations in the U.S. manufacturing industry,
health care companies, universities, Internet service providers, electric
utilities, nonprofit research institutions, and small businesses. It shows that
various pressures, both internal and external, drive organizations to
scrutinize the amount and effectiveness of their cybersecurity practices and
products.
But how do companies decide
how much to invest in cybersecurity, and in what ways? Typically, they use some
kind of benchmarking, in which they learn what other, similar companies are
spending; then they allocate similar amounts of resources. For example, if
Mammoth Manufacturing is assessing the sufficiency of its cybersecurity
investments, it may determine (through surveys or consultants) that other
manufacturing companies usually spend x percent of their information technology
budgets on security. If Mammoth's investment is very different, then Mammoth's
executives may question what is different about Mammoth's needs, practices, or
risk tolerance. It may be that Mammoth has a more capable support staff, or
simply that Mammoth has a higher tolerance for risk. Such analysis helps
Mammoth executives to decide if investments should increase, decrease, or stay
the same.
Notice that this approach
supports only decisions about an appropriate level of spending. Then,
intelligent, detailed decisions must be made about specific expenditures: what
capabilities are needed, which products should be purchased and supported, and
what kind of training may be helpful, for instance. The chief information
security officer at a large, multinational company describes the
decision-making this way: "I am not suggesting this be done slavishlyyou
do not have to follow the herdbut it is important to know in what direction the
herd is going, and at what speed. When we talk about adhering to 'industry
norms and best practices,' these types of things become very important."
But such investment decisions
are not made in a vacuum. Requests for cybersecurity resources usually have to
compete with other types of requests, and the final decisions are made based on
what is best for the business. Thus, there has always been keen interest in how
to make a convincing argument that security is good for business. When
companies have to balance investments in security with other business
investments, it is difficult to find data to support such decision-making.
Because of the many demands on an organization's finite resources, any request
for those resources must be accompanied by a good business case. A business case for a given expenditure
is a proposal that justifies the use of resources. It usually includes the
following items:
·
a description of the problem or need to be addressed by the
expenditure
·
a list of possible solutions
·
constraints on solving the problem
·
a list of underlying assumptions
·
analysis of each alternative, including risks, costs, and benefits
·
a summary of why the proposed investment is good for the
organization
Thus, the business case sets
out everything a manager needs for making an informed decision about the
proposal.
In many instances, several
proposals are considered at once, some competing with others. For example, one
group may propose to implement new network security while another prefers to
focus on physical security. No matter what the proposal, it must be framed as a
business opportunity.
Respected business
publications often address the problem of technology investment. For example,
Kaplan and Norton [KAP92] suggest that
any evaluation of an existing or proposed investment in technology be reported
in several ways at once to form a "balanced scorecard":
from a customer view,
addressing issues such as customer satisfaction
from an operational view,
looking at an organization's core competencies
from a financial view,
considering measures such as return on investment or share price
from an improvement view,
assessing how the investment will affect market leadership and added value
It is typical for companies
to focus exclusively on return on investment, in part because the other views
are less tangible.
Determining Economic Value
Favaro and Pfleeger [FAV98] suggest that economic value can be a unifying
principle in considering any business opportunity. That is, we can look at each
investment alternative in terms of its potential economic value to the company
or organization as a whole. In fact, maximizing economic value can very well
lead to increases in quality, customer satisfaction, and market leadership.
However, there are many
different ways to capture economic value. For example, Gordon and Loeb [GOR06a] present several ways of thinking about
the economic benefit of cybersecurity, including net present value, internal
rate of return, and return on investment. We must decide which investment
analysis approach is most appropriate for security-related investment
decision-making based on economic value.
Investment analysis is
concerned only with the best way to allocate capital and human resources. Thus,
it is distinctly different from cost estimation or metrics; it weighs several
alternatives, including the possibility of retaining earnings to provide an
expected annual rate of return. In other words, from a high-level corporate
perspective, management must decide how a proposed technology investment
compares with simply letting the money earn interest in the bank.
Not all investment analysis
reflects this reality. Gordon and Loeb [GOR06]
describe how organizations actually budget for information security
expenditures. They show that economic concepts are beginning to gain acceptance
from senior information security managers in preparing information security
budgets.
Gordon and Loeb [GOR02b] also point out conceptual and practical
problems with many of the common accounting approaches. They note that managers
often use accounting rules to measure return on investment, but that the
accounting measure is inappropriate for evaluating information security
projects both before the fact and after they are concluded. To see why,
consider how difficult it would be to evaluate the return on investment in
introducing electronic mail at an organization. We know there is a clear
benefit, but it can be daunting to find a good way to measure the benefit.
Gordon and Loeb recommend that companies focus instead on selecting a profit
goal by optimizing their level of information security investment, rather than
by maximizing a measure of return on investment.
Net Present Value
Taking the perspective of a
financial analyst, Favaro and Pfleeger [FAV98]
look critically at the most commonly used approaches: net present value,
payback, average return on book value, internal rate of return, and
profitability index. Favaro and Pfleeger explain why net present value (NPV)
makes the most sense for evaluating software-related investments. For this
reason, we explore NPV in some detail here.
When proposing technology,
you must be sure to consider all costs. For example, to invest in a new
security tool, a company may spend money for training and learning time, as
well as for the tool itself. The NPV calculation subtracts these initial
investment costs from the projected benefits.
More formally, the net present value is the present value
of the benefits minus the value of the initial investment. That is, NPV
compares the value of a dollar (or euro or yuen) today to the value of that
same dollar (or euro or yuen) in the future, taking into account the effects of
inflation and returns on investment. NPV expresses economic value in terms of
total project life, regardless of scale or time frame. Since investment
planning involves spending money in the future, we can think of the present value of an investment as the
value today of a predicted future cash flow.
Suppose, for example, that
the rationale for spending 100 units today on a proposed project suggests that
the project might yield a benefit (profit) of 200 units five years from now. To
assess the overall project benefit to the company, we must adjust the 200 units
both for inflation and for the interest or growth the firm would otherwise gain
on the 100 units over five years if it were instead to invest the money in a
traditional financial vehicle, such as a bank account. Suppose 100 units
invested traditionally (and wisely) today might yield 170 units in five years.
Then the present value of the proposed project is only 30 units (200 - 170),
although the 30 units of profit represent a net benefit for the company.
In general, if the NPV of a
prospective project is positive, it should be accepted. However, if NPV is
negative, the project should probably be rejected; the negative NPV means that
cash flows from the project will be less than from a safer, more traditional
investment. If our example calculation had yielded a future benefit of only 120
units that, when discounted to present value, yielded 90 units, the proposed
project would likely lead to a net loss of 10 units. In other words, investing
in the project would require 100 units to derive only 90 units of benefitnot a
very savvy business strategy.
Adjusting Future Earnings Against Investment Income
As noted before, if a company
has disposable or uncommitted money on hand today that it wants to invest, it
has several choices: it can spend it now or save it for the future. If the
company decides to save it, the earnings compound so that the value of that
money in the future is greater than it is today (not considering inflation).
Suppose corporate savings generate a 5 percent annual return; then by investing
today's 100 units, the firm can expect to have almost 128 units in five years.
Calculations of this kind suggest a threshold that must be met if a proposed
project is considered by the company to be worthwhile. Thus, if a proposed
cybersecurity (or any other) project requires an up-front investment of 100
units, its profit by the fifth year has to be at least 128 units to be
economically viable. In this way, net present value calculations give companies
a way to compare and contrast several investment strategies and pick the most
economically desirable one(s).
Moreover, an advantage of
using net present value to assess a security project is that it evaluates the
effects of the proposed investment over the life of the project. For example,
if the proposed project loses money for the first two years but then proceeds
to be highly profitable in all succeeding years, it may be a wise long-term
investment. NPV provides a fair comparison for projects that turn profitable at
different times in the future; the hard part is knowing how far in the future
to perform the calculation.
Our example used a five
percent return on savings. In general, the NPV calculation uses a discount rate or opportunity cost, corresponding to the rate of return expected from
an equivalent investment in capital markets; this rate may change over time
and, of course, is difficult to predict for the future. In other words, the
discount rate reflects how much money an organization could make if it invested
its money in the bank or a financial vehicle instead of in software technology.
Companies often use NPV to evaluate proposed projects; for instance,
Hewlett-Packard used NPV to evaluate investment in two multiyear corporate
reuse projects.
The formal equation for
calculating NPV is
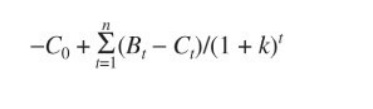
where Bt and Ct are the benefits and costs
anticipated from the investment in each time period t. C0 is the initial investment,
the discount
rate (expected rate of return
on investment) is k, and n is the number of time periods over which the
investment's costs and benefits are considered.
Net Present Value Example
To see how NPV works,
consider the situation at Acme Corporation, where the chief security officer is
considering protecting its networks in one of two ways:
Buy an off-the-shelf intrusion detection system (IDS). This choice
involves a large initial procurement cost, with subsequent high returns (based
on avoided work), but the off-the-shelf product will be outdated and must be
replaced after three years.
Build a customized intrusion detection system with a reusable
design. The reuse requires considerable up-front costs for design and
documentation, but the long-term costs are less because the product's life will
be longer.
In each case, the direct
savings from the software are the same: finding and stopping malicious
behavior. The net present value calculation may resemble Table 9 -2. In this example, suppose it costs
$9,000 to purchase an intrusion detection system, and $4,000 to build one.
Thus, initial investments for each choice are $ 9,000 and $4,000, respectively.
Using a time period of one year, we can assess the cash flows for each choice.
For the purchased IDS, no additional development is likely to be required by
the end of year 1, and we estimate that avoided costs (that is, the benefit of
not having to deal with intrusions) are $5,000. For the home-grown IDS, we
estimate that we will avoid intrusions but will be correcting and perfecting
the software in the first year; hence, we estimate that $7,000 of development
cost will offset the $5,000 in benefit, for a net cost of $2,000 at the end of
year 1. By year 2, we reap benefits for both choices, but maintenance and
documentation still offset the benefits of the home-grown software. In year 3,
we expect more benefit from each choice. By year 4, we must upgrade the
purchased IDS, resulting in a negative cash flow, while the home-grown software
continues to provide positive benefit. Using a discount rate of 15 percent, we
see that the purchased intrusion detection system has a slightly higher NPV and
is therefore preferred.
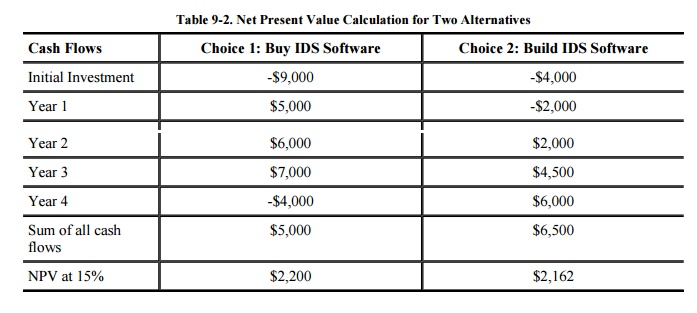
Notice that, even though the
home-grown software has a higher total cash flow, the NPV suggest that Acme
should invest in an off-the-shelf IDS. This result reflects the fact that the
NPV approach is sensitive to the timing of the cash flows; the later the
return, the more the overall value is penalized. Thus, time to market is
essential to the analysis and affects the outcome. The size or scale of a
project is also reflected in the NPV.
Because NPV is additive, we
can evaluate the effects of collections of projects simply by summing their
individual NPVs. On the other hand, significant gains from one technology can
mask losses from investment in another; for this reason, it is useful to
evaluate each type of investment separately. In real-world practice, NPV is not
used for naive single-project evaluation, but rather in the context of a more
comprehensive financial and strategic framework [FAV96].
Internal Rate of Return
The internal rate of return (IRR) is derived from the net present
value; it is equal to the discount rate that makes the NPV equal to zero. In
other words, it is the expected rate of return from this investment. If the
internal rate of return is 4 percent and the discount rate is 12 percent, we
have a poor proposal, because we could do better investing money elsewhere. If,
however, the internal rate of return is 18 percent versus a discount rate of 12
percent, our proposal is wise because it generates a higher rate of return than
we would be able to earn in other ways.
Return on Investment
Return on investment (ROI) calculations are closely related to IRR
and NPV. The ROI is generated by dividing the last period's accounting profits (calculated from revenues and costs) by the
cost of the investments required to generate those profits. Thus, ROI looks
back at how a company or organization has performed, whereas NPV and IRR
project likely future performance of new investments.
According to the CSI/FBI
Computer Security Survey administered in 2005, 38 percent of respondents use
ROI to assess the value of cybersecurity, 19 percent use IRR, and 18 percent
use NPV.
Estimating Costs Fairly
Davidson [DAV05] describes how Oracle evaluated two
different intrusion detection systems. The value and accuracy of each system
were assessed as contributions to how well the company could do its job:
"The old system had a ridiculously high number of alarms every week, and
an extraordinary amount of them70 to 80 percentwere false positives. We looked
at what it was costing us to track down the alarms that we really needed to do
something about, including the costs for people to sort through the alarms and
analyze them. The new product had a much lower alarm rate as well as a lower
false positive rate. The information provided by the new product was better, at
a lower cost. Economic analysis, specifically return on investment, helped us
choose the new supplier over the old one."
In this example Davidson
tries to put a value on the time it takes her staff to investigate alarms.
Although there were many false alarms (that is, not real incidents), the time
invested still represents a cost associated with using the old system.
In general, businesses need
to know whether and how investing one more unit buys them more security. The
effects on security depend on various perspectives, such as effects on the
global economy, the national economy, and corporate supply chains. Sidebar 9-1 illustrates how an organization can
generate a business case for a security technology.
A business case is an
argument for doing something: investing in new technology, training people,
adding a security capability to a product, or maintaining the status quo. As we
have seen, because many management arguments are made in terms of money,
computer security business cases are often framed in economic terms: amount
saved, return for taking an action, or cost avoided. Sometimes it is difficult
to separate the security effects from the more general effects, such as
improved functionality or better access to assets. This separation problem
makes it harder to answer the question, "How much more security does that
investment buy me?" Moreover, these arguments beg the question of how to
derive sound numbers in computer security. In the next section we analyze
sources of quantitative data.
Related Topics