Chapter: Security in Computing : The Economics of Cybersecurity
Data to Justify Security Action
Data to Justify Security Action
Interest in society's
reliance on information technology has spawned a related interest in
cybersecurity's ability to protect our information assets. However, we lack
highquality descriptive data.
Data are needed to support
cybersecurity decision-making at several levels.
National and global data
address national and international concerns by helping users assess how
industry sectors interact within their country's economy and how cybersecurity
affects the overall economy. These data can help us understand how impairments
to the information infrastructure can generate ripple effects on other aspects of national
and global economies.
Enterprise data enable us to
examine how firms and enterprises apply security technologies to prevent
attacks and to deal with the effects of security breaches.
In
particular, the data capture information about how enterprises balance their
security costs with other economic demands.
Technology data describe
threats against core infrastructure technologies, enabling modelers to develop
a set of least-cost responses.
If we were looking at cost of
labor, raw materials, or finished goods, we would have excellent data from
which to work. Those concepts are easier to quantify and measure, governments
assist in collecting the data, and economists know where to turn to obtain
them. What makes these statistics so valuable to economists is that they are
comparable. Two economists can investigate the same situation and either come
to similar conclusions or, if they differ, investigate the data models
underlying their arguments to determine what one has considered differently
from the other.
Data to support economic
decision-making must have the following characteristics:
Accuracy. Data are accurate
when reported values are equal or acceptably close to actual values. For
example, if a company reports that it has experienced 100 attempted intrusions
per month, then the actual number of attempted intrusions should equal or be
very close to 100.
Consistency. Consistent
reporting requires that the same counting rules be used by all reporting
organizations and that the data be gathered under the same conditions. For
example, the counting rules should specify what is meant by an
"intrusion" and whether multiple intrusion attempts by a single
malicious actor should be reported once per actor or each time an attempt is
made.
Similarly,
if a system consists of 50 computers and an intrusion is attempted
simultaneously by the same actor in the same way, the counting rules should
indicate whether the intrusion is counted once or 50 times.
Timeliness.
Reported data should be current enough to reflect an existing situation. Some
surveys indicate that the nature of attacks has been changing over time. For
instance, Symantec's periodic threat reports [SYM06]
indicate that attack behavior at the companies it surveys has changed from
mischievous hacking to serious criminal behavior. Reliance on old data might
lead security personnel to be solving yesterday's problem.
Reliability. Reliable data
come from credible sources with a common understanding of terminology. Good
data sources define terms consistently, so data collected in one year are comparable
with data collected in other years.
Sidebar 9-2 describes some of
the data available to support cybersecurity decision-making.
Notice that some of the
results in Sidebar 9-2 present trend
data (37 percent in 2003 versus 65 percent in 2005 use security standards) and
others report on events or activities (organizations have hardened their
systems). However, few of the results contain data that could be used directly
in a security investment business case.
Security Practices
The
Information Security Breaches Survey (ISBS) is a particularly rich source of
information about cybersecurity incidents and practices and provides a good
model for capturing information about cybersecurity. A collaborative effort
between the U.K. Department of Trade and Industry and PricewaterhouseCoopers,
this survey is administered every two years to U.K. businesses large and small.
Participants are randomly sampled and asked to take part in a structured
telephone interview. In late 2005 and early 2006, over a thousand companies
agreed to participate in the study. Additionally, PricewaterhouseCoopers
conducted in-depth interviews with a few participants to verify results of the
general interviews.
The survey results are
reported in four major categories: dependence on information technology, the
priority given to cybersecurity, trends in security incidents, and expenditures
on and awareness of cybersecurity. In general, information technology is
essential to U.K. businesses, so computer security is becoming more and more
important. Of businesses surveyed, 97 percent have an Internet connection, 88
percent of which are broadband. More than four in five businesses have a web
site, most of which are hosted externally. Small business is particularly
dependent on information technology: Five of six said that they could not run
their companies without it. Many of the respondents rate security above
efficiency when specifying corporate priorities.
Nearly three times as many
companies have a security policy now than in 2000. Almost every responding
organization does regular backups, and three-quarters store the backups
offsite. These organizations are proactive about fighting viruses and spam; 98
percent of businesses have antivirus software, 80 percent update their
antivirus signatures within a day of notification of a new virus, and 88
percent install critical operating system patches within a week. Moreover, 86
percent of companies filter their incoming e-mail for spam. They view these
controls as sufficient and effective; three-quarters of U.K. businesses are
confident or very confident that they identified all significant security
breaches in the previous year.
Economic Impact
But what is the economic
impact of the policies and controls? Although the large increase in security
incidents during the 1990s has stabilized (62 percent of U.K. companies had a
security incident in 2005, compared with 74 percent in 2003), the reported
costs remain substantial. The average U.K. company spends 4 to 5 percent of its
information technology budget on information security, but two out of five
companies spend less than 1 percent on security.
The average cost of a
company's worst security incident was about £12,000, up from £10,000 in 2003.
Moreover, large businesses are more likely than small businesses to have
incidents and to have more of them (the median is 19 per year). A large
business's worst breach costs on average £90,000. Overall, the cost of security
breaches to U.K. companies has increased by about half since 2003; it is
approximately £10 billion per annum. Fewer than half the companies surveyed
conduct a security risk assessment, and those that do tend to spend more on
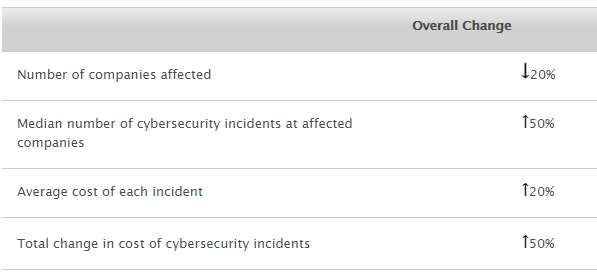
security. Table 9-3 summarizes the
changes in incidents and cost reflected by the ISBS survey.
Related Topics