Chapter: Database Management Systems : SQL & Query Optimization
Data Control Language(DCL)
Data
Control Language
A data
control language (DCL) is a syntax similar to a computer programming language
used to control access to data stored in a database. In particular, it is a
component of Structured Query to control access to data stored in a database.
In particular, it is a component of Structured Query Language (SQL).
It is used to create roles, permissions, and
referential integrity as well it is used to control access to database by
securing it. These SQL commands are used for providing security to database
objects. These commands are GRANT and REVOKE.
Examples of DCL commands include:
GRANT to allow specified users to perform specified
tasks.
REVOKE to cancel previously granted or denied
permissions.
The
Data Control Language (DCL) component of the SQL language is
used to create privileges to allow users access to, and manipulation of, the
database. There are two main commands:
GRANT to grant a privilege to a user
REVOKE to revoke (remove) a privilege from a user
The operations for which privileges may be granted
to or revoked from a user or role may include CONNECT, SELECT, INSERT, UPDATE,
DELETE, EXECUTE, and USAGE. In the Oracle database, executing a DCL command
issues an implicit commit. Hence you cannot roll back the command. In
PostgreSQL, executing DCL is transactional, and can be rolled back.
SQL
GRANT REVOKE Commands
DCL commands are used to enforce database security
in a multiple user database environment. Two types of DCL commands are GRANT
and REVOKE. Only Database Administrator's or owner's of the database object can
provide/remove privileges on a database object.
SQL
GRANT Command
SQL GRANT is a command used to provide access or
privileges on the database objects to the users.
The
Syntax for the GRANT command is:
GRANT privilege_name ON object_name TO {user_name
|PUBLIC |role_name} [WITH GRANT OPTION];
privilege_name is the access right or privilege
granted to the user. Some of the access rights are ALL, EXECUTE, and SELECT.
object_name is the name of an database object like
TABLE, VIEW, STORED PROC and SEQUENCE.
user_name is the name of the user to whom an access
right is being granted.
user_name is the name of the user to whom an access
right is being granted.
PUBLIC is used to grant access rights to all users.
ROLES are a set of privileges grouped together.
WITH GRANT OPTION - allows a user to grant access
rights to other users.
For Example: GRANT SELECT ON employee TO user1; This
command grants a SELECT permission on employee table to user1.You should use
the WITH GRANT option carefully because for example if you GRANT SELECT
privilege on employee table to user1 using the WITH GRANT option, then user1
can GRANT SELECT privilege on employee table to another user, such as user2
etc. Later, if you REVOKE the SELECT privilege on employee from user1, still
user2 will have SELECT privilege on employee table.
SQL REVOKE
Command:
The REVOKE command removes user access rights or
privileges to the database objects.
The Syntax for the REVOKE command is:
REVOKE
privilege_name ON object_name FROM {user_name |PUBLIC |role_name}
For Example: REVOKE
SELECT ON employee FROM user1;This command will REVOKE a SELECT
privilege on employee table from user1.When you REVOKE SELECT privilege on a
table from a user, the user will not be able to SELECT data from that table
anymore. However, if the user has received SELECT privileges on that table from
more than one users, he/she can SELECT from that table until everyone who
granted the permission revokes it.
Privileges and Roles:
Privileges: Privileges
defines the access rights provided to a user on a database object. There are
two types of privileges.
1) System
privileges - This allows the user to CREATE, ALTER,
or DROP database objects.
2) Object
privileges - This allows the user to EXECUTE,
SELECT, INSERT, UPDATE, or DELETE data from database objects to which
the privileges apply.
Few CREATE system privileges are listed below:
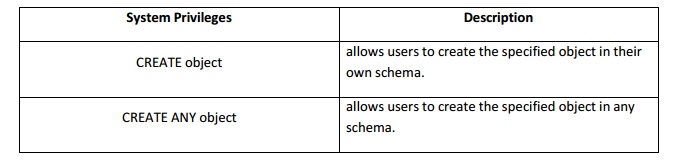
System Privileges Description
CREATE
object allows
users to create the specified object in theirown schema.
CREATE Any
object allows users to create
the specified object in any schema.
.
The above rules also apply for ALTER and
DROP system privileges.
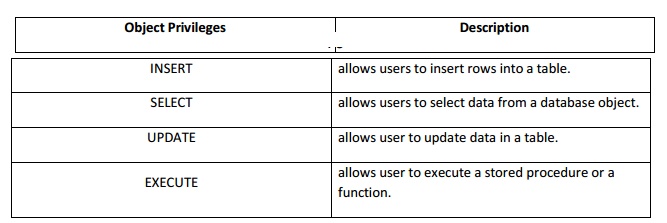
Few of the object privileges are listed below:
Object Privileges with Description
INSERT
allows users to insert rows into a table.
SELECT
allows users to select data from a database object.
UPDATE
allows user to update data in a table.
EXECUTE
allows user to execute a stored procedure or a
function.
Roles: Roles
are a collection of privileges or access rights. When there are many users in a
database it becomes difficult to grant or revoke privileges to users.
Therefore, if you define roles, you can grant or revoke privileges to users,
thereby automatically granting or revoking privileges. You can either create
Roles or use the system roles pre-defined by oracle.
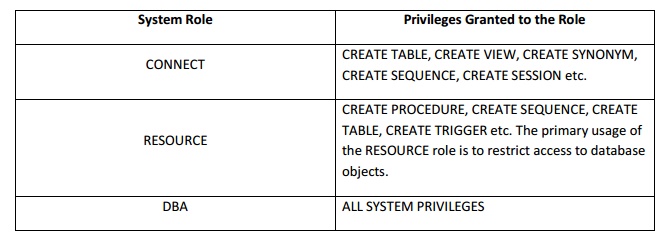
Some
of the privileges granted to the system roles are as given below:
System
Role
Privileges
Granted to the Role
CREATE
TABLE, CREATE VIEW, CREATE SYNONYM,
CONNECT
CREATE
SEQUENCE, CREATE SESSION etc.
CREATE
PROCEDURE, CREATE SEQUENCE, CREATE
TABLE,
CREATE TRIGGER etc. The primary usage of
RESOURCEthe
RESOURCE role is to restrict access to database objects.
DBA
ALL
SYSTEM PRIVILEGES
Creating
Roles:
The
Syntax to create a role is:
CREATE
ROLE role_name [IDENTIFIED BY password];
For
Example: To create a role called "developer" with
password as "pwd",the code will be as follows
CREATE
ROLE testing [IDENTIFIED BY pwd];
It's easier to GRANT or REVOKE privileges to the
users through a role rather than assigning a privilege directly to every user.
If a role is identified by a password, then, when you GRANT or REVOKE
privileges to the role, you definitely have to identify it with the password.
We
can GRANT or REVOKE privilege to a role as below.
For
example: To grant CREATE TABLE privilege to a user by
creating a testing role
First, create a testing Role
CREATE ROLE testing
Second, grant a CREATE
TABLE privilege to the ROLE testing. You can add more privileges to the ROLE.
GRANT CREATE TABLE TO testing;
Third, grant the role to a user.
GRANT testing TO user1;
To revoke a CREATE TABLE privilege from testing
ROLE, you can write:
REVOKE CREATE TABLE FROM testing;
The Syntax to drop a role from the
database is as below:
DROP ROLE role_name;
For example: To
drop a role called developer, you can write:
DROP ROLE testing;
GRANT command
In order to do anything
within an Oracle database you must be given the appropriate privileges. Oracle
operates a closed system in that you cannot perform any action at all unless
you have been authorized to do so. This includes logging onto the database,
creating tables, views, indexes and synonyms, manipulating data (ie select,
insert, update and delete) in tables created by other users, etc.
The SQL command to grant a privilege on a table is:
GRANT SELECT, INSERT, UPDATE, DELETE ON tablename TO
username;
There are many more forms of the GRANT command, but
this is sufficient for this Unit.
Any combination of the
above privileges is allowed. You can issue this command on any tables that you
have created. For example:
GRANT SELECT ON employee TO hn23;
GRANT SELECT, UPDATE, DELETE ON employee TO hn44;
REVOKE
command
The SQL command to revoke a privilege on a table is:
REVOKE
SELECT, INSERT, UPDATE, DELETE ON tablename FROM username;
For example:
REVOKE SELECT ON employee FROM hn23;
REVOKE SELECT, UPDATE, DELETE FROM hn44;
Related Topics