Chapter: Cryptography and Network Security Principles and Practice : Overview
A Model For Network Security
A MODEL FOR NETWORK SECURITY
•
A security-related
transformation on the information to be sent. Examples include the encryption
of the message, which scrambles the message so that it is unreadable by the
opponent, and the addition of a code based on the contents of the message,
which can be used to verify the identity of the sender.
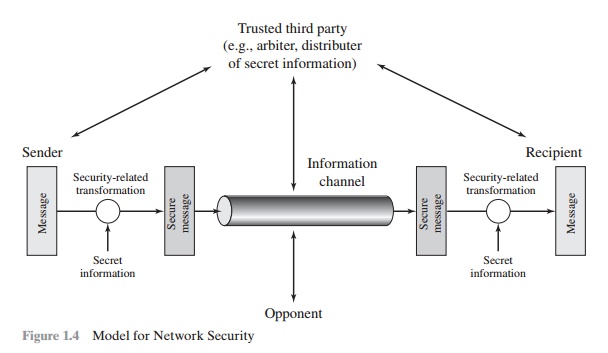
•
Some secret information
shared by the two principals and, it is hoped, unknown to the opponent. An
example is an encryption key used in conjunc-tion with the transformation to
scramble the message before transmission and unscramble it on reception.6
A trusted
third party may be needed to achieve secure transmission. For example, a third
party may be responsible for distributing the secret information to the two
principals while keeping it from any opponent. Or a third party may be needed
to arbitrate disputes between the two principals concerning the authenticity of
a message transmission.
This
general model shows that there are four basic tasks in designing a particular
security service:
1.
Design an algorithm
for performing the security-related transformation. The algorithm should be
such that an opponent cannot defeat its purpose.
2.
Generate the secret
information to be used with the algorithm.
3.
Develop methods for
the distribution and sharing of the secret information.
4.
Specify a protocol to
be used by the two principals that makes use of the security algorithm and the
secret information to achieve a particular security service.
Parts One
through Five of this book concentrate on the types of security mecha-nisms and
services that fit into the model shown in Figure 1.4. However, there are other
security-related situations of interest that do not neatly fit this model but
are consid-ered in this book. A general model of these other situations is
illustrated by Figure 1.5, which reflects a concern for protecting an
information system from unwanted access. Most readers are familiar with the
concerns caused by the existence of hackers, who attempt to penetrate systems
that can be accessed over a network. The hacker can be someone who, with no
malign intent, simply gets satisfaction from breaking and entering a computer
system. The intruder can be a disgruntled employee who wishes to do damage or a
criminal who seeks to exploit computer assets for financial gain
(e.g.,
obtaining credit card numbers or performing illegal money transfers).
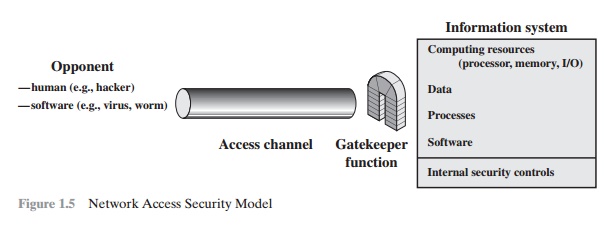
Another
type of unwanted access is the placement in a computer system of logic that
exploits vulnerabilities in the system and that can affect application
pro-grams as well as utility programs, such as editors and compilers. Programs
can pre-sent two kinds of threats:
•
Information
access threats: Intercept
or modify data on behalf of users who should not have access to that
data.
•
Service
threats: Exploit
service flaws in computers to inhibit use by legitimate users.
Viruses and worms are two examples of software attacks. Such
attacks can be introduced into a system by means of a disk that contains the
unwanted logic con-cealed in otherwise useful software. They can also be
inserted into a system across a network; this latter mechanism is of more
concern in network security.
The security mechanisms needed to cope with unwanted access fall
into two broad categories (see Figure 1.5). The first category might be termed
a gatekeeper function. It includes password-based login procedures that are
designed to deny access to all but authorized users and screening logic that is
designed to detect and reject worms, viruses, and other similar attacks. Once
either an unwanted user or unwanted software gains access, the second line of
defense consists of a variety of internal controls that monitor activity and
analyze stored information in an attempt to detect the presence of unwanted
intruders. These issues are explored in Part Six.
Related Topics