Chapter: Cryptography and Network Security Principles and Practice : Overview
Security Mechanisms
SECURITY MECHANISMS
Table 1.3
lists the security mechanisms defined in X.800. The mechanisms are divided into
those that are implemented in a specific protocol layer, such as TCP or an
application-layer protocol, and those that are not specific to any particular
protocol layer or security service. These mechanisms will be covered in the
appro-priate places in the book. So we do not elaborate now, except to comment
on the
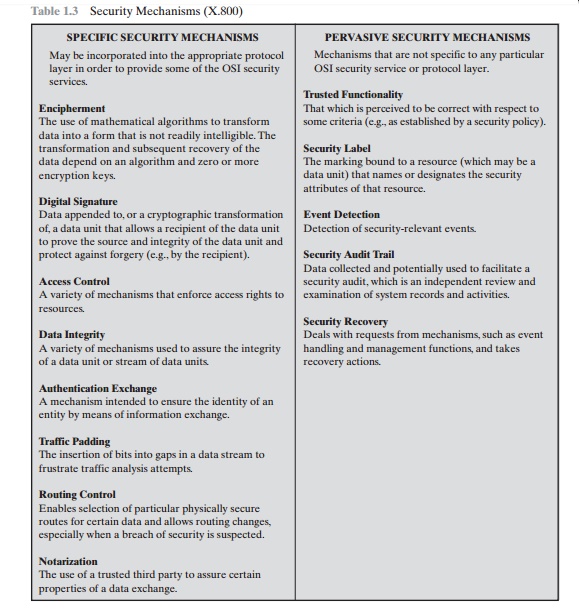
definition
of encipherment. X.800 distinguishes between reversible encipherment mechanisms
and irreversible encipherment mechanisms. A reversible encipherment mechanism
is simply an encryption algorithm that allows data to be encrypted and
subsequently decrypted. Irreversible encipherment mechanisms include hash
algo-rithms and message authentication codes, which are used in digital
signature and message authentication applications.
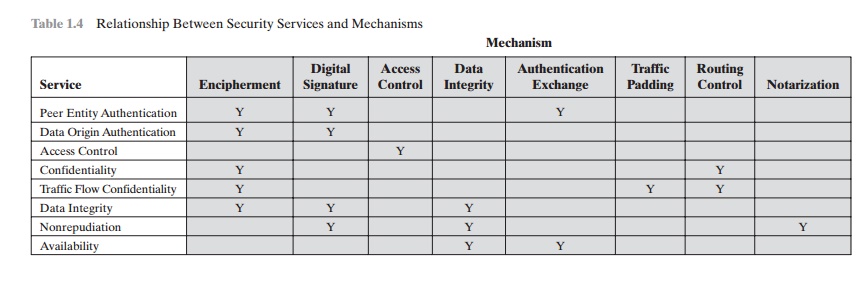
Table
1.4, based on one in X.800, indicates the relationship between security
services and security mechanisms.
A model
for much of what we will be discussing is captured, in very general terms, in
Figure 1.4. A message is to be transferred from one party to another across
some sort of Internet service. The two parties, who are the principals
in this transaction, must cooperate for the exchange to take place. A logical
information channel is estab-lished by defining a route through the Internet
from source to destination and by the cooperative use of communication
protocols (e.g., TCP/IP) by the two principals.
Security
aspects come into play when it is necessary or desirable to protect the
information transmission from an opponent who may present a threat to
confi-dentiality, authenticity, and so on. All the techniques for providing
security have two components:
Related Topics