Chapter: Cryptography and Network Security Principles and Practice : System Security : Firewalls
Firewall Location and Configurations
FIREWALL LOCATION AND CONFIGURATIONS
As Figure 22.1a indicates, a firewall is positioned to
provide a protective barrier between an external,
potentially untrusted source of traffic
and an internal network. With
that general principle in mind, a security administrator must decide on the location and on the number of firewalls
needed. In this section, we look at some common options.
DMZ Networks
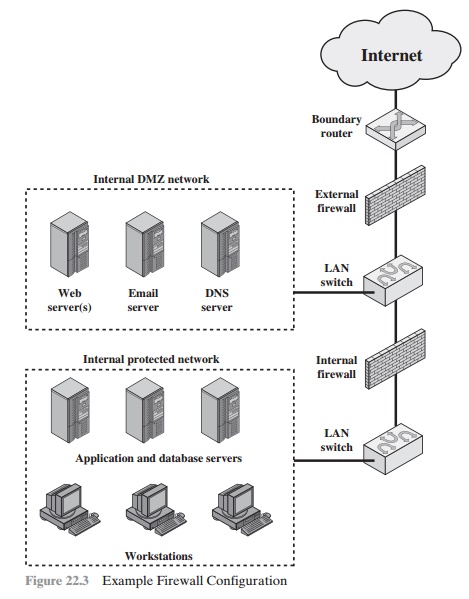
Figure 22.3 suggests
the most common
distinction, that between
an internal and an
external firewall. An external firewall is placed at the edge of a local or
enterprise network, just inside
the boundary router
that connects to the Internet
or some wide area network (WAN). One or more internal firewalls protect the bulk of the
enter- prise network. Between these two types of firewalls are one or more
networked devices in a region referred to as a DMZ (demilitarized zone)
network. Systems that are externally accessible but need some protections are usually located on DMZ networks. Typically, the
systems in the DMZ require or foster external con- nectivity, such as a
corporate Web site, an e-mail
server, or a DNS (domain name system) server.
The external firewall provides a measure of access control and
protection for the DMZ systems consistent with their need for external
connectivity. The external
firewall also provides
a basic level of protection for the remainder
of the enterprise network. In this type of configuration, internal
firewalls serve three purposes:
1.
The internal firewall adds more stringent
filtering capability, compared
to the external firewall, in order to protect enterprise servers and workstations from external attack.
2.
The internal firewall provides two-way protection with respect to the DMZ. First, the internal firewall protects the remainder
of the network from attacks launched
from DMZ systems. Such attacks might originate from worms, rootkits, bots, or other malware lodged in a DMZ system.
Second, an internal
firewall can protect the DMZ systems
from attack from the internal
protected network.
3.
Multiple
internal firewalls can
be used
to protect portions of the internal
network from each other. For example, firewalls can be configured so
that internal servers are protected
from internal workstations and vice versa. A common practice is to place the DMZ
on a different network interface on the external firewall
from that used to access the internal
networks.
Virtual Private Networks
In today’s distributed computing environment, the virtual private network
(VPN) offers an attractive solution
to network managers.
In essence, a VPN consists
of a set of computers that interconnect by means of a relatively
unsecure network and that make use of encryption and special protocols to provide security. At each corporate site, workstations, servers,
and databases are linked by one or more local area net- works (LANs). The Internet
or some other public network
can be used to intercon- nect sites, providing a cost savings
over the use of a private network
and offloading the wide area network
management task to the public network provider.
That same public network provides an access path for telecommuters and other
mobile employees to log on to corporate systems from remote
sites.
But the manager faces a fundamental
requirement: security. Use of a public network
exposes corporate traffic
to eavesdropping and provides an entry point
for unauthorized users. To counter
this problem, a VPN is needed. In essence, a VPN uses encryption and authentication in the lower
protocol layers to provide a secure
connection through an otherwise insecure
network, typically the Internet. VPNs are
generally cheaper than real private networks using private lines but rely on having the same encryption and authentication system at both ends.
The encryption may be performed by firewall software
or possibly by routers. The most common protocol mechanism used for this purpose is at the IP level and is known as IPsec.
An organization maintains LANs at dispersed
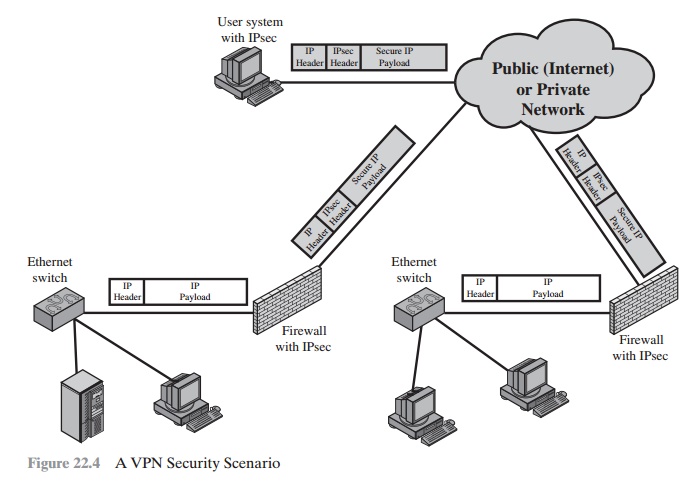
locations. A logical means of implementing an IPsec is in a firewall, as shown
in Figure 22.4, which essentially repeats Figure 19.1. If IPsec is implemented
in a separate box behind (internal to) the firewall, then VPN traffic passing through the firewall
in both directions is encrypted. In this case, the firewall is
unable to perform its filtering function or other
security functions, such as access control, logging, or scanning for viruses. IPsec could
be implemented in the boundary
router, outside the firewall. However, this device is likely to be less
secure than the firewall and thus less desirable as an IPsec platform.
Distributed Firewalls
A distributed firewall configuration involves stand-alone firewall
devices plus host- based firewalls working together
under a central
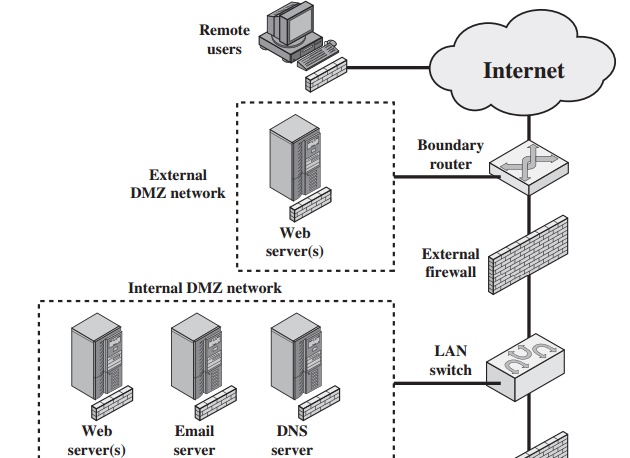
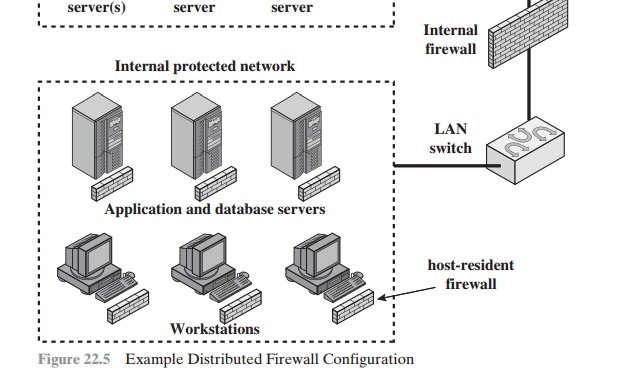
administrative control. Figure
22.5 suggests a distributed firewall configuration. Administrators can
configure host- resident firewalls on hundreds of servers and workstations as
well as configure personal firewalls on local and remote user systems. Tools let the network
adminis- trator set policies and monitor security across the entire
network. These firewalls protect against internal
attacks and provide
protection tailored to specific machines and applications. Stand-alone firewalls provide global protection, including internal
firewalls and an external firewall, as discussed previously.
With distributed firewalls, it may make sense to establish both an internal
and an external DMZ. Web servers
that need less protection because they have less critical information on them could
be placed in an external
DMZ, outside the exter-
nal firewall. What protection is needed is provided by host-based firewalls on these servers.
An important aspect of a distributed
firewall configuration is security moni- toring. Such monitoring typically
includes log aggregation and analysis, firewall statistics, and fine-grained
remote monitoring of individual hosts if needed.
Summary of Firewall Locations
and Topologies
We can now summarize the discussion from
Sections 22.4 and 22.5 to define a spectrum of firewall locations and
topologies. The following alternatives can be identified:
•
Host-resident firewall: This category includes personal firewall software and
firewall software on servers. Such firewalls can be used alone or as part of an in-depth firewall deployment.
•
Screening router: A single
router between internal and external networks with stateless or full packet filtering. This arrangement is typical for small office/home office (SOHO) applications.
Single bastion inline: A single
firewall device between
an internal and external
router (e.g., Figure 22.1a). The firewall may implement stateful
filters and/or application proxies. This is the typical firewall appliance configuration for small
to medium-sized organizations.
•
Single
bastion T: Similar to single bastion
inline but has a third network
interface on bastion to a DMZ where externally visible servers are
placed. Again, this is a common appliance configuration for medium
to large organizations.
•
Double bastion
inline: Figure 22.3 illustrates
this configuration, where the DMZ is sandwiched between
bastion firewalls. This
configuration is common for large businesses and
government organizations.
•
Double bastion T: The DMZ is on a separate network
interface on the bastion
firewall. This configuration is also common for large businesses and govern-
ment organizations and may be required. For
example, this configuration is required
for Australian government use (Australian Government Information Technology Security Manual - ACSI33).
•
Distributed firewall configuration: Illustrated in
Figure 22.5. This configura- tion is used by some large businesses and
government organizations.
Related Topics