Chapter: Cryptography and Network Security Principles and Practice : Network and Internet Security : Transport-Level Security
Web Security Considerations
WEB SECURITY
CONSIDERATIONS
The World Wide Web is fundamentally a client/server application running over the Internet and TCP/IP intranets. As such, the security tools and approaches discussed so far in this book are relevant to the issue of Web security.
But, as pointed out in [GARF02], the
Web presents new challenges
not generally appreciated in the context of computer and network security.
The Internet is
two-way. Unlike traditional publishing environments—even electronic publishing systems involving teletext, voice response, or fax-back—
the Web is vulnerable to attacks on the Web servers over the Internet.
•
The Web is increasingly serving as a highly
visible outlet for corporate and product information and as the platform for business transactions. Reputations can be damaged
and money can be lost if the Web servers are subverted.
•
Although Web browsers
are very easy to use, Web servers are relatively easy to
configure and manage,
and Web content is increasingly easy to develop,
the underlying software is extraordinarily complex. This complex
software may hide many potential
security flaws. The short history of the Web is filled with examples of new and upgraded systems,
properly installed, that are vulnerable to a variety of security attacks.
•
A Web server can be exploited as a launching
pad into the corporation’s or agency’s entire computer complex. Once the Web server is subverted,
an attacker may be able to gain
access to data and systems not part of the Web
itself but connected to the server
at the local site.
•
Casual
and untrained (in security matters) users are common clients for Web-based services. Such
users are not necessarily aware of the security
risks that exist and do not
have the tools or knowledge to take effective countermeasures.
Web Security
Threats
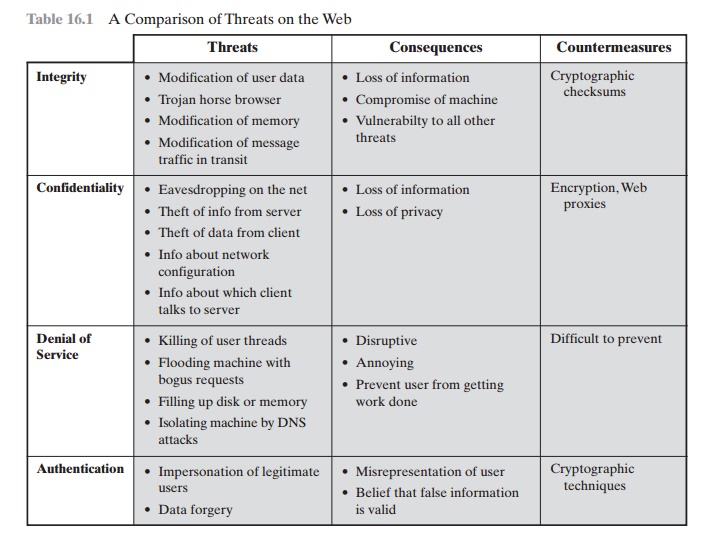
Table 16.1 provides
a summary of the types of security
threats faced when using the Web.
One way to group these threats is in terms of passive
and active attacks. Passive attacks
include eavesdropping on network
traffic between browser and server and gaining
access to information on a Web site
that is supposed to be restricted. Active attacks include
impersonating another user, altering messages
in transit between client and server,
and altering information on a Web site.
Another way to classify Web security
threats is in terms of the location
of the threat: Web server, Web browser, and
network traffic between browser and server. Issues of server and browser security
fall into the category of computer system
secu- rity; Part Four of this
book addresses the issue of system security in general but is also applicable to Web system security. Issues
of traffic security
fall into the category
of network security and are addressed in this chapter.
Web Traffic
Security Approaches
A number of
approaches to providing Web security are
possible. The various approaches
that have been considered are similar in the services they provide
and, to some extent,
in the mechanisms that they use, but they differ
with respect to their scope of
applicability and their relative location within the TCP/IP protocol stack.
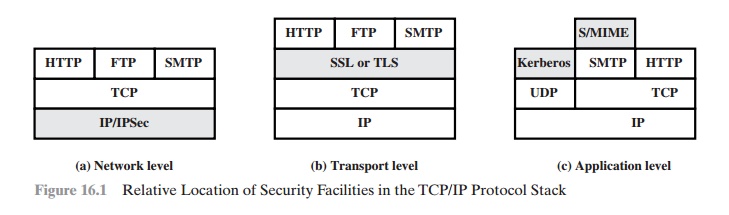
Figure 16.1 illustrates this difference. One
way to provide Web security is to
use IP security (IPsec) (Figure
16.1a). The advantage of using IPsec
is that it is trans- parent
to end users and applications and provides a general-purpose solution. Furthermore, IPsec includes a filtering capability so
that only selected traffic need
incur the overhead of IPsec processing.
Another relatively general-purpose solution
is to implement security just above TCP (Figure 16.1b). The foremost example of
this approach is the Secure
Sockets Layer (SSL) and the follow-on Internet
standard known as Transport
Layer Security (TLS). At this level,
there are two implementation choices.
For full general- ity, SSL (or TLS) could be provided as part
of the underlying protocol suite and therefore be transparent to applications.
Alternatively, SSL can be embedded in specific packages. For example, Netscape and Microsoft
Explorer browsers come equipped with SSL, and most Web servers have implemented the protocol.
Application-specific security services are embedded within
the particular appli-
cation. Figure 16.1c shows examples of this architecture. The advantage
of this approach is that the service
can be tailored to the specific needs
of a given application.
Related Topics