Chapter: Web or internet Programming : Basic Network and Web Concepts
TCP and UDP protocols
TCP and UDP protocols
TCP
• TCP is a
transport layer protocol used by applications that require guaranteed delivery.
• It is a
sliding window protocol that provides handling for both timeouts and
retransmissions.
• TCP
establishes a full duplex virtual connection between two endpoints. Each
endpoint is defined by an IP address and a TCP port number.
• The
operation of TCP is implemented as a finite state machine. The byte stream is
transferred in segments. The window size determines the number of bytes of data
that can be sent before an acknowledgement from the receiver is necessary.
• The
Transmission Control Protocol (TCP) is one of the core protocols of the
Internet Protocol Suite. TCP is one of the two original components of the suite
(the other being Internet Protocol, or IP), so the entire suite is commonly
referred to as TCP/IP.
• Whereas
IP handles lower-level transmissions from computer to computer as a message
makes its way across the Internet, TCP operates at a higher level, concerned
only with the two end systems, for example a Web browser and a Web server.
• In particular,
TCP provides reliable, ordered delivery of a stream of bytes from a program on
one computer to another program on another computer.
• Besides
the Web, other common applications of TCP include e-mail and file transfer.
Among other management tasks, TCP controls segment size, flow control, and data
exchange rate.
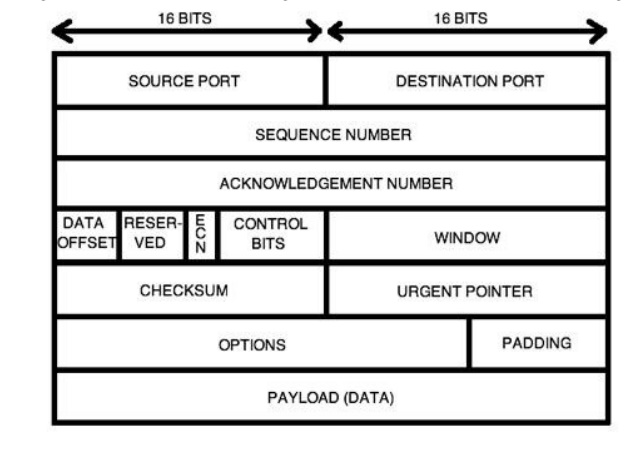
• Source
port (16 bits) – identifies the sending port
• Destination
port (16 bits) – identifies the receiving port
• Sequence
number (32 bits) – has a dual role:
• If the
SYN flag is set, then this is the initial sequence number. The sequence number
of the actual first data byte (and the acknowledged number in the corresponding
ACK) are then this sequence number plus 1.
• If the
SYN flag is clear, then this is the accumulated sequence number of the first
data byte of this packet for the current session.
• Acknowledgment
number (32 bits) – if the ACK flag is set then the value of this field is the
next sequence number that the receiver is expecting. This acknowledges receipt
of all prior bytes (if any). The first ACK sent by each end acknowledges the
other end's initial sequence number itself, but no data.
Data
offset (4 bits) – specifies the size of the TCP header in 32-bit words. The
minimum size header is 5 words and the maximum is 15 words thus giving the
minimum size of 20 bytes and maximum of 60 bytes, allowing for up to 40 bytes
of options in the header. This field gets its name from the fact that it is
also the offset from the start of the TCP segment to the actual data.
• Reserved
(4 bits) – for future use and should be set to zero
• Flags (8
bits) (aka Control bits) – contains 8 1-bit flags
• CWR (1
bit) – Congestion Window Reduced (CWR) flag is set by the sending host to
indicate that it received a TCP segment with the ECE flag set and had responded in congestion control
mechanism
• ECE (1
bit) – ECN-Echo indicates
• If the
SYN flag is set, that the TCP peer is ECN capable.
• If the
SYN flag is clear, that a packet with Congestion Experienced flag in IP header
set is received during normal transmission
• URG (1
bit) – indicates that the Urgent pointer field is significant
• ACK (1
bit) – indicates that the Acknowledgment field is significant. All packets
after the initial SYN packet sent by the client should have this flag set.
• PSH (1
bit) – Push function. Asks to push the buffered data to the receiving
application.
• RST (1 bit)
– Reset the connection
• SYN (1
bit) – Synchronize sequence numbers. Only the first packet sent from each end
should have this flag set. Some other flags change meaning based on this flag,
and some are only valid for when it is set, and others when it is clear.
• FIN (1
bit) – No more data from sender
• Window
(16 bits) – the size of the receive window, which specifies the number of bytes
(beyond the sequence number in the acknowledgment field) that the receiver is
currently willing to receive
• Checksum (16
bits) – The 16-bit checksum field is used for error-checking of the header and
data
• Urgent
pointer (16 bits) – if the URG flag is set, then this 16-bit field is an offset
from the sequence number indicating the last urgent data byte
• Options
(Variable 0-320 bits, divisible by 32) – The length of this field is determined
by the data offset field. Options 0 and 1 are a single byte (8 bits) in length.
The remaining options indicate the total length of the option (expressed in
bytes) in the second byte
UDP
• The User
Datagram Protocol (UDP) is one of the core members of the Internet Protocol
Suite, the set of network protocols used for the Internet.
• With UDP,
computer applications can send messages, in this case referred to as datagram,
to other hosts on an Internet Protocol (IP) network without requiring prior
communications to set up special transmission channels or data paths.
• UDP is
sometimes called the Universal Datagram Protocol. The protocol was designed by
David P.
• UDP uses
a simple transmission model without implicit hand-shaking dialogues for
guaranteeing reliability, ordering, or data integrity. Thus, UDP provides an
unreliable service and datagram may arrive out of order, appear duplicated, or
go missing without notice.
• UDP
assumes that error checking and correction is either not necessary or performed
in the application, avoiding the overhead of such processing at the network
interface level.
• Time-sensitive
applications often use UDP because dropping packets is preferable to waiting
for delayed packets, which may not be an option in a real-time system.
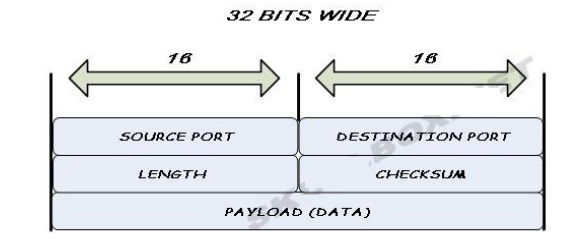
• Source
port number
This field identifies the sender's port when
meaningful and should be assumed to be the port to reply to if needed. If not
used, then it should be zero. If the source host is the client, the port number
is likely to be an ephemeral port number. If the source host is the server, the
port number is likely to be a well-known port number.
• Destination
port number
This field identifies the receiver's port and
is required. Similar to source port number, if the client is the destination
host then the port number will likely be an ephemeral port number and if the
destination host is the server then the port number will likely be a well-known
port number.
• Length
A field that specifies the length in bytes of
the entire datagram: header and data. The minimum length is 8 bytes since
that's the length of the header. The field size sets a theoretical limit of
65,535 bytes (8 byte header + 65,527 bytes of data) for a UDP datagram. The
practical limit for the data length which is imposed by the underlying IPv4
protocol is 65,507 bytes (65,535 − 8 byte UDP header − 20 byte IP header).
• Checksum
The checksum field is used for error-checking
of the header and data. If the checksum is omitted in IPv4, the field uses the
value all-zeros
Differences:
TCP:
• Connection
oriented transport protocol
• Sends
data as a stream of bytes
• Guarantee
of delivery
UDP:
• Connection
less protocol
• Datagram
service
• No
guarantee of delivery
Related Topics