Network Examples and Protocols - Reference Model | 12th Computer Applications : Chapter 11 : Network Examples and Protocols
Chapter: 12th Computer Applications : Chapter 11 : Network Examples and Protocols
Reference Model
Reference
Model
OSI Model
Open System Interconnection (OSI) model was found in the year 1934, general framework that enables network protocols ong with software and systems to be developed based on general set of guidelines. It describes the standards for the inter-computer communication. See Figure 11.9

There are many prompts used to remember the OSI
layer order:
● Everyone Needs Data Processing.
● Everyone Should Try New Diet Pepsi.
OSI Layers:
1. Physical
Layer: This is the 1st layer, it defines the electrical and physical
specifications for devices.
2. Data Link Layer: It is the 2nd layer and it guarantees that the data transmitted are free of errors. This layer has simple protocols like “802.3 for Ethernet” and “802.11 for Wi-Fi”.
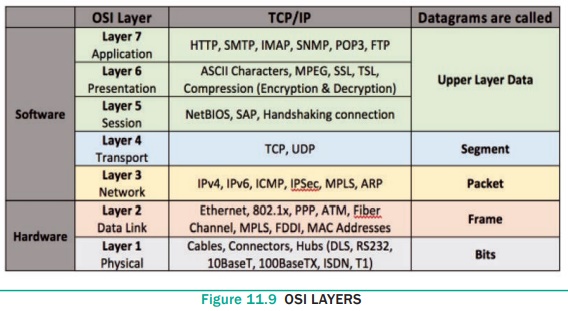
3. Network
Layer: It is the 3rd layer determining the path of the data
packets. This layer is responsible for routing of data packets using IP Addressing.
4. Transport
Layer: It is the 4th layer that guarantees the transportation/sending
of data successfully. It includes the error checking operation.
5. Session
Layer: It is the 5th layer, identifies the established system
session between different network entities. It controls dialogues between
computers .For instance, while accessing a system remotely, session is created
between your computer and the remote system.
6. Presentation
Layer: It is the 6th layer that does the translation of data to
the next layer (Prepare the data to the Application Layer). Encryption and
decryption protocols occur in this layer such as, Secure Socket Layer (SSL).
7. Application
Layer: It is the 7th layer, which acts as the user interface platform
comprising of software within the system.
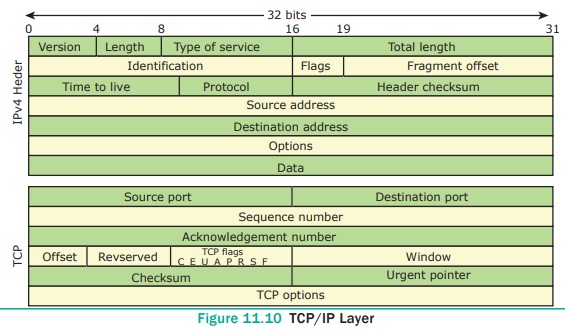
TCP/IP
Transmission
Control Protocol/Internet Protocol, TCP/IP is a set of protocols
which governs communications among all computers on the Internet. TCP/IP
protocol tells how information should be packaged, sent, and received, as well
as how to get to its destination. See Figure 11.10
TCP
WORKING: TCP/IP is a combination of
two protocols: Transmission Control Protocol (TCP) and Internet Protocol (IP).
The Internet Protocol typically specifies the logistics of the packets that are
sent out over networks; it specifies the packets which have to go, where to go
and how to get there. The Transmission Control Protocol is accountable for
guaranteeing the trustworthy transmission of data. It checks if any packet is
not transmitted and submits it again.
Frequent TCP/IP Protocols
● HTTP – It is
used between a web client and a web
server and it guarantees non-secure
data transmissions.
● HTTPS – It is
used between a web client and a web
server ensures secure data
transmissions.
● FTP – It is
used between computers for sending
and receiving file.
Domain Names and TCP/IP Addresses
The address for any website is not as easy as to
remember, domain name are used instead. For example, 216.58.216.164 is one of the IP address for Google and google.com is the domain name.
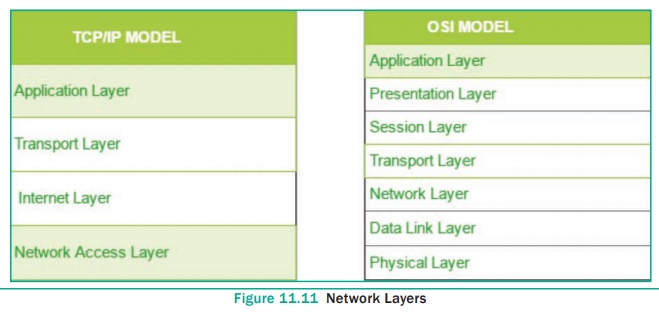
The Different Layers of TCP/IP
There are four total layers of TCP/IP protocol,
each of which is listed below with a brief description.
● Network
Access Layer - concerned with
building packets.
● Internet
Layer - describes how packets are
to be delivered.
● Transport
Layer - ensure the proper transmission
of data.
● Application
Layer - application network processes.
These processes include File Transfer Protocol (FTP), Hypertext Transfer
Protocol (HTTP), and Simple Mail Transfer Protocol (SMTP).
Other Network Protocols
Network protocol sotherthan OSI and TCP/ IP were simply
known as other network protocols which implements security over the network
communication that include HTTPs, SSL, and SFTP. Other networks similarly classified in network layer
are IP, ARP, ICMP,IGMP, at transport layer are TCP,UDP at Application Layer are HTTP, FTP, Telenet, SMTP, and
DNS.
HTTPS positions
for Hypertext Transfer Protocol
Secure. It’s a protocol where encoded data transfer on a secure connection.
This HTTPS make data more safe and provides data security over the network
mainly on public networks like Wi-Fi. See Figure 11.11
For example, let us take a bank website, when we go to login page, we may watch an HTTPS in address bar with some specific design. HTTPS mainly deals with financial transactions or transfer users personal data highly sensitivily. Banking websites are common examples for HTTPS. Data exchanged between the user and the website is not stolen, read or altered by a third party.
In layman’s terms, HTTPS gurantees that users watch
websites that they want to watch. Data exchanged between the user and the
website is not read, stolen or tampered by a third party. But it can’t encrypt
everything - it has some limitations too. For example, HTTPS can’t encrypt host
addresses and port numbers.
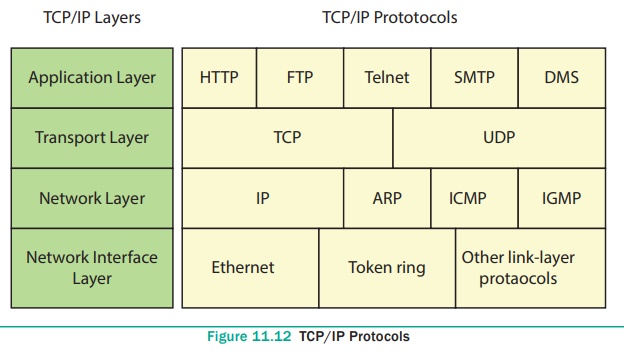
TCP/IP procedures are based on a layered framework.
TCP/IP has four layers. See Figure 11.12
Network Interface Layer
It is the bottommost level layer. It is comparable
to that of the Open System Interconnection Physical and Data Link layers.
Different TCP/IP protocols are being used at this layer, Ethernet and Token
Ring for local area networks and protocols such as X.25, Frame Relay, and ATM
for wide area networks. It is assumed to be an unreliable layer.
Network Layer
It is the layer where data is addressed, packaged, and routed among networks. The important Internet protocols that operate at the Network layer are:
● Internet
Protocol (IP): Routable protocol
which uses IP addresses to deliver packets. It is an unreliable protocol, does
not guarantee delivery of information.
Address
Resolution Protocol (ARP): Resolves IP addresses to MAC (Medium Access Control) addresses. (A MAC address is a
hardware identification number that uniquely identifies each device on a
network.)i.e., to map IP network addresses to the hardware addresses.
Internet
Control Message Protocol (ICMP): Used by network devices to send error messages and operational
information. Example: A host or router might not be reached or a request
service is not presented.
● Internet
Group Management Protocol (IGMP): It is a communication protocol used by hosts and routers to send
Multicast (group Communication) messages to multiple IP addresses at once.
Transport Layer
The sessions are recognized and data packets are
swapped between hosts in this layer. Two main protocols established at this
layer are:
● Transmission Control Protocol (TCP): Provides
reliable connection oriented
transmission between two hosts. It ensures delivery of packets between the
hosts.
User
Datagram Protocol (UDP): Provides connectionless, unreliable, one-to-one or
one-to-many delivery.
Application Layer
The Application layer of the TCP/IP model is
similar to the Session, Presentation, and Application layers of the OSI
Reference Model. The most popular Application layer protocols are:
Hypertext
Transfer Protocol (HTTP): The core protocol of the World Wide Web. File Transfer Protocol (FTP): enables a
client to send and receive complete files from a server. Telnet: connect to another computer on the Internet. Simple Mail Transfer Protocol (SMTP): Provide e-mail services. Domain Name System (DNS): Refer to
other host computers by using names
rather than numbers.
Related Topics