Chapter: Knowledge Management
Knowledge Management System Life Cycle
KNOWLEDGE MANAGEMENT SYSTEM LIFE
CYCLE
1 Challenges in Building KM Systems
2 Conventional Vrs KM System Life Cycle (KMSLS)
3 Knowledge Creation and Knowledge Architecture
4 Nonaka’s Model of Knowledge
5 Creation and Transformation. Knowledge
Architecture
1 Challenges in Building KM Systems
Knowledge Evaluation:
Involves assessing the worth of information.
Knowledge Processing:
Involves changing people's attitudes and behaviours.
Involves the identification of techniques to acquire, store,
process and distribute information.
Sometimes it is necessary to document how certain decisions were
reached. Knowledge Implementation:
An organization should commit to change, learn, and innovate.
It is important to extract meaning from information that may
have an impact on specific missions.
Lessons learned from feedback can be stored for future to help
others facing the similar problem(s).
2 Conventional Vrs KM System Life
Cycle (KMSLS)
Key Differences:
The systems analyst gathers data and information from the users
and the users depend on analysts for the solution.
The knowledge developer gathers knowledge from people with known
knowledge and the developer depends on them for the solution.
The main interface for the systems analyst is associated with
novice users who knows the problem but not the solution.
The main interface for the knowledge developer is associated
with the knowl- edgeable person who knows the problem and the solution.
Conventional systems development is primarily sequential,
whereas KMSLC is incre- mental and interactive.
In case of conventional systems, testing is usually done towards
the end of the cycle (after the system has been built), whereas in KMSLC, the
evolving system is verified and validated from the beginning of the cycle.
Systems development and systems management is much more
extensive for conven- tional information systems than it is for KMSLC.
The conventional systems life cycle is usually process-driven
and documentation- oriented whereas KMSLC is result-oriented.
The conventional systems development does not support tools such
as rapid prototyping since it follows a predefined sequence of steps
KMSLC can use rapid prototyping incorporating changes on the
spot.
Key Similarities:
Both cycles starts with a problem and end with a solution.
The early phase in case of conventional systems development life
cycle starts with information gathering.
In KMSLC the early phase needs knowledge capture.
Verification and validation of a KM system is often very
similar to conventional systems testing. Both the systems analyst and the
knowledge developer needs to choose the appropriate tools
for designing their intended systems.
3 Knowledge Creation and Knowledge
Architecture
Knowledge Creation
Knowledge update can mean creating new knowledge based on
ongoing experience in a specific domain and then using the new knowledge in
combination with the existing knowledge to come up with updated knowledge for
knowledge sharing.
A team can commit to perform a job over a specific period of
time.
A job can be regarded as a series of specific tasks carried out
in a specific order.
When the job is completed, then the team compares the experience
it had initially (while starting the job) to the outcome
(successful/disappointing).
This comparison translates experience into knowledge.
While performing the same job in future,the team can take
corrective steps and/or modify the actions based on the new knowledge they have
acquired.
Over time, experience usually leads to expertise where one team
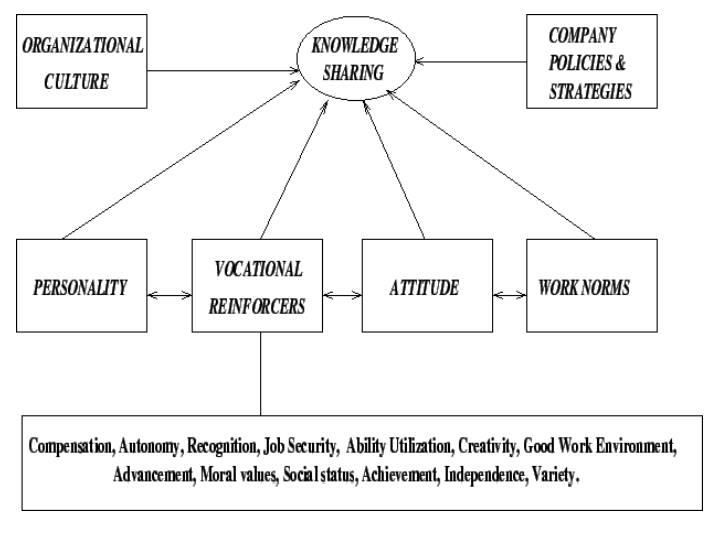
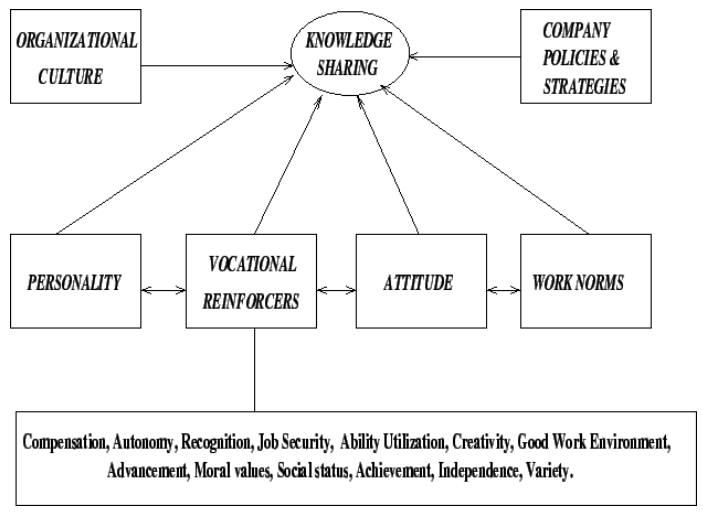
(or ind There exists factors that encourage (or retard) knowledge transfer.
Personality is one factor in case of knowledge sharing.
For example, extrovert people usually posses self-confidence,
feel secure, and tend to share experiences more readily than the introvert,
self-centered, and security-conscious people.
People with positive attitudes, who usually trust others and who
work in environments conductive to knowledge sharing tends to be better in
sharing knowledge.
Vocational reinforcers are the key to knowledge sharing.
People whose vocational needs are sufficiently met by job
reinforcers are usually found to be more likely to favour knowledge sharing
than the people who are deprived of one or more reinforcers.
Knowledge Architecture
Knowledge architecture can be regarded as a prerequisite to
knowledge sharing. The infrastructure can be viewed as a combination of people,
content, and technology.
These components are inseparable and interdependent
By people, here we mean knowledge workers, managers, customers,
and suppliers.
As the first step in knowledge architecture, our goal is to
evaluate the existing information/ documents which are used by people, the
applications needed by them, the people they usually contact for solutions, the
associates they collaborate with, the official emails they send/receive, and
the database(s) they usually access.
All the above stated resources help to create an employee
profile, which can later be used as the basis for designing a knowledge
management system.
4 Nonaka’s Model of Knowledge
In 1995, Nonaka coined the terms tacit knowledge and explicit
knowledge as the two main types of human
knowledge. The key to knowledge creation lies in the way it is mobilized
and converted through technology.
Tacit to tacit communication
(Socialization):
Takes place between people in meetings or in team discussions.
Tacit to explicit communication
(Externalization):
Articulation among people trough dialog (e.g., brainstorming).
Explicit to explicit communication
(Communication):
This transformation phase can be best supported by technology.
Explicit knowledge can be easily captured and then distributed/ transmitted to
worldwide audience.
Explicit to tacit communication
(Internalization):
This implies taking explicit knowledge (e.g., a report) and
deducing new ideas or taking constructive action. One significant goal of
knowledge management is to create technology to help the users to derive tacit
knowledge from explicit knowledge.
5 Creation and Transformation.
5.1 The People Core
By people, here we mean knowledge workers, managers, customers,
and suppliers.
As the first step in knowledge architecture, our goal is to
evaluate the existing information/ documents which are used by people, the
applications needed by them, the people they usually contact for solutions, the
associates they collaborate
with, the official emails they send/receive, and the database(s)
they usually access.
All the above stated resources help to create an employee
profile, which can later be used as the basis for designing a knowledge
management system.
5.2 Knowledge Architecture
The idea behind assessing the people core is to do a proper job
in case of assigning job content to the right person and to make sure that the
flow of information that once was obstructed by departments now flows to right
people at right time.
In order to expedite knowledge sharing, a knowledge network has
to be designed in such a way as to assign people authority and responsibility
for specific kinds of knowledge content, which means:
5.3 Identifying knowledge centers:
Here, the term knowledge center means areas in the organization
where knowledge is available for capturing.
These centers supports to identify expert(s) or expert teams in
each center who can collaborate in the necessary knowledge capture process.
Activating knowledge content satellites
After determining the knowledge that people need, the next step
is to find out where the required knowledge resides, and the way to capture it
successfully.
This step breaks down each knowledge center into some more
manageable levels, satellites, or areas.
5.4 Assigning experts for each
knowledge center:
After the final framework has been decided, one manager should
be assigned for each knowledge satellite who will ensure integrity of
information content, access, and update. Ownership is a crucial factor in case
of knowledge capture, knowledge transfer, and knowledge implementation.
In a typical organization, departments usually tend to be
territorial.
Often, fight can occur over the budget or over the control of
sensitive processes (this includes the kind of knowledge a department owns).
These reasons justify the process of assigning department
ownership to knowledge content and knowledge process adjacent/interdependent
departments should be cooperative and ready to share knowledge.
5.6 The Technical Core
The objective of the technical core is to enhance communication
as well as ensure effective knowledge sharing.
Technology provides a lot of opportunities for managing tacit
knowledge in the area of communication.
Communication networks create links between necessary databases.
Here the term technical core is meant to refer to the totality
of the required hardware, software, and the specialized human resources.
5.7 User Interface Layer
Usually a web browser represents the interface between the user
and the KM system. It is the top layer in the KM system architecture.
The way the text, graphics, tables etc are displayed on the
screen tends to simplify the technology for the user.
The user interface layer should provide a way for the proper
flow of tacit and explicit knowledge.
The necessary knowledge transfer between people and technology
involves capturing tacit knowledge from experts,storing it in knowledge base,
and making it available to people for solving complex problems.
Features to be considered in case of
user interface design:
ü Consistency
ü Relevancy
ü Visual clarity
ü Usability
ü Ease of Navigation
Authorized Access Layer
This layer maintains security as well as ensures authorized
access to the knowledge captured and stored in the organization's repositories.
The knowledge is usually captured by using internet, intranet of
extranet.
An organization's intranet represents the internal network of
communication systems.
Extranet is a type of intranet with extensions allowing
specified people (customers, suppliers, etc.) to access some organizational information.Issues
related to the access layer: access privileges, backups.
The access layer is mostly focused on security, use of protocols
(like passwords), and software tools like firewalls.
Firewalls can protect against:
ü E-mails that can cause problems.
ü Unauthorized access from the outside world.
ü Undesirable material (movies, images, music etc).
A mobile agent roams around the internet across multiple servers
looking for the correct information. Some benefits can be found in the areas
of:
Fault tolerance. Heterogeneous operation.
Key components of this layer:
Membership in specific services, such as sales promotion, news
service etc. The registration directory that develops tailored information
based on user profile. The search facility such as a search engine.
In terms of the prerequisites for this layer, the following
criteria can be considered:
ü Security.
ü Portability.
ü Flexibility
ü Scalability
Issues related to the access layer: access privileges, backups.
The access layer is mostly focused on security, use of protocols
(like passwords), and software tools like firewalls.
Firewalls can protect against:
ü E-mails that can cause problems.
ü Unauthorized access from the outside world.
ü Undesirable material (movies, images, music etc).
A mobile agent roams around the internet across multiple servers
looking for the correct information. Some benefits can be found in the areas
of:
ü Fault tolerance.
ü Heterogeneous operation.
ü
Key components of this layer:
Membership in specific services, such as sales promotion, news
service etc. The registration directory that develops tailored information
based on user profile. The search facility such as a search engine.
In terms of the prerequisites for this layer, the following
criteria can be considered: Security.
ü Portability.
ü Flexibility
ü Scalability