Chapter: Cryptography and Network Security Principles and Practice : Mutual Trust : User Authentication
Kerberos
KERBEROS
Kerberos is an authentication service developed as part of Project Athena
at MIT. The problem that
Kerberos addresses is this: Assume an open distributed environment in which
users at workstations wish to access services on servers distributed throughout
the network. We would like for
servers to be able to restrict access to authorized users and to be able to authenticate requests for service.
In this environ- ment, a workstation cannot be trusted
to identify its users correctly
to network ser- vices. In particular, the following three
threats exist:
1.
A user may gain
access to a particular workstation and pretend to be another user operating
from that workstation.
2.
A user may alter
the network address of a workstation
so that the requests sent from the altered workstation appear to come from the impersonated workstation.
3.
A user may eavesdrop
on exchanges and use a replay attack to gain entrance to a server or to disrupt operations.
In any of these cases, an unauthorized user
may be able to gain access to services and data that he or she is not authorized
to access. Rather than building in elabo- rate authentication
protocols at each server, Kerberos provides a centralized authentication
server whose function is
to authenticate users to servers and
servers to users. Unlike most other authentication schemes described in
this book, Kerberos relies exclusively on symmetric encryption, making no use of public-key encryption.
Two versions of Kerberos are in common use. Version 4 [MILL88, STEI88] implementations still exist. Version 5 [KOHL94] corrects some of the security deficiencies of version 4 and has been issued as a proposed Internet Standard (RFC 4120).5
We begin this section with a brief discussion of
the motivation
for the Kerberos approach. Then,
because of the complexity of Kerberos, it is best to start with a description of the authentication protocol used in version 4. This enables
us to see the essence of the Kerberos
strategy without considering some of the details
required to handle subtle security
threats. Finally,
we examine version
5. Motivation
If a set of users is provided
with dedicated personal
computers that have no network connections, then a user’s
resources and files
can be protected by physically securing each personal computer.
When these users instead are served by a centralized time- sharing system, the time-sharing operating system must
provide the security. The operating system can enforce access-control policies based on user identity
and use the logon procedure to identify users.
Today, neither of these scenarios is typical. More common is a distributed archi- tecture consisting of dedicated user workstations (clients) and distributed or central-
ized servers. In this environment, three approaches to security can be envisioned.
1.
Rely on each individual client workstation to assure the identity of its user or
users and rely on each server to enforce a security policy based on user identi- fication (ID).
2.
Require that client systems authenticate themselves to servers,
but trust the client
system concerning the identity
of its user.
3.
Require the user to
prove his or her identity for each service invoked. Also require that servers prove their identity
to clients.
In a small,
closed environment in which all systems are owned and operated by a single organization, the first or perhaps the second strategy
may suffice.6 But in a more
open environment in which network
connections to other machines are supported, the third approach is needed
to protect user information and resources housed at the server. Kerberos
supports this third approach. Kerberos assumes a distributed client/server
architecture and employs one or more Kerberos servers to provide an authentication service.
The first published report on Kerberos
[STEI88] listed the following requirements.
•
Secure: A network
eavesdropper should not be able to obtain the necessary information to impersonate a user. More generally, Kerberos
should be strong enough that a potential
opponent does not find it to be the weak link.
•
Reliable: For all services that rely on Kerberos for
access control, lack of availability of the Kerberos
service means lack of availability of the supported services. Hence, Kerberos
should be highly reliable and should
employ a distributed server architecture with one system
able to back up another.
•
Transparent: Ideally, the user should
not be aware
that authentication is taking
place beyond the requirement to enter a password.
•
Scalable: The system should
be capable of supporting large
numbers of clients and servers. This suggests
a modular, distributed architecture.
To support these requirements, the overall scheme of Kerberos
is that of a trusted third-party authentication service that uses a protocol
based on that pro- posed by Needham
and Schroeder [NEED78],
which was discussed
in Section 15.2.
It is trusted in the sense that clients and servers trust Kerberos to mediate their mutual authentication. Assuming the Kerberos protocol is well designed, then the authentication service is secure if the Kerberos server itself is secure.7
Kerberos Version 4
Version 4 of Kerberos makes use of DES, in a
rather elaborate protocol, to pro- vide the authentication service. Viewing the
protocol as a whole, it is difficult to see the need for the many elements
contained therein. Therefore, we adopt a strat- egy used by Bill Bryant of Project
Athena [BRYA88] and build up to the full protocol by looking first at several
hypothetical dialogues. Each successive dia- logue adds additional complexity
to counter security vulnerabilities revealed in the preceding dialogue.
After examining the protocol, we look at
some other aspects of version 4.
A SIMPLE AUTHENTICATION DIALOGUE In an unprotected network environment, any client can apply to any server for service. The
obvious security risk is that of impersonation.
An opponent can pretend
to be another client and obtain
unauthorized privileges on server machines. To counter
this threat, servers
must be able to confirm the
identities of clients who request service. Each server can be required to
undertake this task for each client/server interaction, but in an open
environment, this places
a substantial burden
on each server.
An alternative is to use an authentication
server (AS) that knows the pass- words of all users and stores these in a
centralized database. In addition, the AS shares a unique secret key with each
server. These keys have been distributed physically or in some other secure
manner. Consider the following hypothetical dialogue:
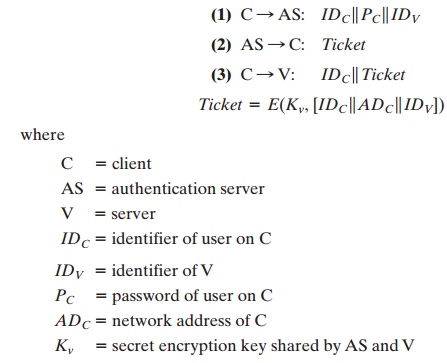
In this scenario, the user logs on to a
workstation and requests access to server V.
The client module C in the user’s workstation requests the user’s
password and then sends a message
to the AS that includes
the user’s ID, the server’s
ID, and the user’s password. The AS checks its database to see if the user has supplied the
proper password for this user ID and whether this
user is permitted access to server
V. If both tests are passed, the AS
accepts the user as authentic and must now convince the server that this user is authentic. To do so, the AS creates a ticket that contains the user’s ID and network address and the
server’s ID. This ticket is encrypted
using the secret key shared by the AS and this server. This ticket is then sent back to C. Because the ticket is
encrypted, it cannot be altered by C or by an opponent.
With this ticket,
C can now apply to V for service. C sends a message to V con- taining C’s ID and the ticket. V
decrypts the ticket and verifies that the user ID in the ticket is the same as the unencrypted user ID in the message.
If these two match,
the server considers the user authenticated and grants the requested service.
Each of the ingredients of message (3) is significant. The ticket is encrypted
to prevent alteration or forgery.
The server’s ID (IDV) is included in the ticket so that the server
can verify that it has decrypted the ticket properly. IDC is included
in the ticket to indicate that this ticket has been issued on behalf of C. Finally,
ADC serves to counter the following threat.
An opponent could
capture the ticket
transmitted in message (2), then use the name IDC and transmit
a message
of form (3) from another
workstation. The server would
receive a valid ticket that matches the user ID and grant access to the user on that other workstation. To prevent
this attack, the AS
includes in the ticket the network address
from which the original request
came. Now the ticket is valid only if it is transmitted from the same
workstation that ini- tially requested the ticket.
A MORE SECURE AUTHENTICATION DIALOGUE Although the foregoing scenario solves some of the
problems of authentication in an open network environment, problems remain.
Two in particular stand
out. First, we would like to minimize
the number of times that a user has to enter a password. Suppose each
ticket can be used only once. If user C logs on to a workstation in the morning
and wishes to check his or her mail at a mail server, C must supply a password
to get a ticket for the mail
server. If C wishes to check the mail several times during the day, each attempt requires reentering the
password. We can improve matters by
saying that tickets are reusable. For a
single logon session, the workstation can store the mail server ticket after it is received
and use it on behalf of the user for multiple accesses to the mail server.
However,
under this scheme,
it remains the case that a user would need a new ticket for every different service.
If a user wished to access a print server, a mail server, a file server,
and so on, the first instance of each access would require
a new ticket and hence require
the user to enter the password.
The second problem
is that the earlier scenario
involved a plaintext
transmis- sion of the password [message (1)]. An eavesdropper could
capture the password and use any service accessible to the victim.
To solve these
additional problems, we introduce a scheme for avoiding plain- text passwords and a new server,
known as the ticket-granting server
(TGS). The new
(but still hypothetical) scenario is as follows.
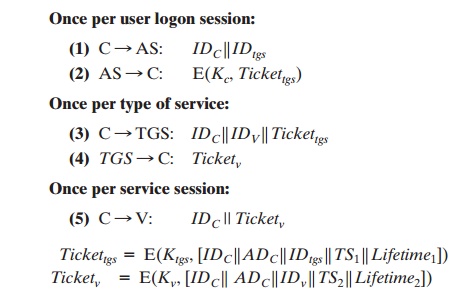
The new service, TGS, issues
tickets to users
who have been authenticated to AS. Thus, the user first requests a ticket-granting ticket (Tickettgs) from the AS. The client
module in the user workstation saves this ticket. Each time the user requires access to a new service, the client applies
to the TGS, using
the ticket to authenticate
itself. The TGS then grants a ticket for the particular service. The client saves each
service-granting ticket and uses it to authenticate its user to a server each
time a particular service is requested. Let us look at the details of this scheme:
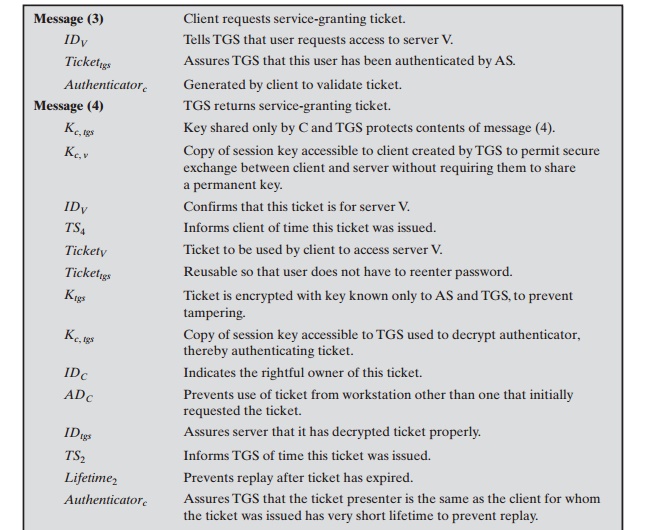
1.
The client requests a ticket-granting ticket on behalf of the user by sending its user’s ID to the AS, together with the TGS ID, indicating a request to use the TGS service.
2.
The AS responds with a ticket
that is encrypted with a key that is derived from the
user’s password (Kc), which
is already stored
at the AS. When
this response arrives at the client,
the client prompts
the user for his or her password, gener- ates the key, and attempts to decrypt the incoming message.
If the correct pass- word is supplied, the
ticket is successfully recovered.
Because only the correct user should know the password, only the correct
user can recover the ticket. Thus, we have used the password
to obtain credentials from Kerberos without having to
transmit the password in plaintext. The
ticket itself consists of the ID and network address
of the user, and the ID of the TGS. This cor-
responds to the first scenario.
The idea is that the client can use this ticket to request multiple
service-granting tickets. So the ticket-granting
ticket is to be reusable. However, we do not wish an opponent to be able
to capture the ticket and use it. Consider the following scenario: An opponent
captures the login ticket and waits until the user has logged
off his or her workstation. Then the opponent
either gains access to that
workstation or configures his workstation with the same network address as
that of the victim. The opponent would be able to reuse the ticket to spoof the
TGS. To counter this, the
ticket includes a timestamp, indicating the
date and time at which the ticket was issued, and a lifetime,
indicating the length of time for which the ticket is valid (e.g., eight hours). Thus, the client now has a reusable ticket
and need not bother the user for a password for each new service request.
Finally, note that the ticket-granting ticket is encrypted with a secret key
known only to the AS and the TGS. This prevents alteration of the ticket.
The ticket is reen- crypted with a key based on the user’s password. This assures that the ticket can be recovered only by the correct user, providing the authentication.
Now that the client has a ticket-granting
ticket, access to any server can be obtained with steps 3 and 4.
3.
The client requests a service-granting ticket
on behalf of the user.
For this pur- pose, the
client transmits a message to the TGS containing the user’s ID, the ID of the desired
service, and the ticket-granting ticket.
4.
The TGS decrypts the incoming ticket
using a key shared only by the AS and the
TGS (Ktgs) and verifies
the success of the decryption by the presence
of its ID. It checks
to make sure that the lifetime has not expired.
Then it compares the user ID and network address
with the incoming information to authenti- cate the user. If the user is
permitted access to the server V, the
TGS issues a ticket to grant access to the requested
service.
The service-granting ticket has the same structure
as the ticket-granting ticket.
Indeed, because the TGS is a server, we would expect that the same elements are
needed to authenticate a client to the TGS and to authenticate a client to an
appli- cation server. Again,
the ticket contains
a timestamp and lifetime. If the user wants
access to the same service at a later time, the client can simply use the previously
acquired service-granting ticket and need not bother the user for a password. Note that the ticket is encrypted with a
secret key (Kv) known only to the TGS and the server, preventing alteration.
Finally, with a particular service-granting ticket, the client can
gain access to the corresponding service
with step 5.
5.
The client requests access to a service on behalf of the user. For this
purpose, the client transmits a message to the server containing the
user’s ID and the service-granting ticket. The
server authenticates by using the contents of the ticket.
This new scenario
satisfies the two requirements of only one password query per user session and protection of the user password.
THE VERSION 4 AUTHENTICATION
DIALOGUE Although
the foregoing scenario enhances security compared to the first attempt, two
additional problems remain. The heart of the first problem is the lifetime
associated with the ticket-granting ticket. If this lifetime is very short
(e.g., minutes), then the user will be repeatedly asked for a password. If the
lifetime is long (e.g., hours), then an opponent has a greater opportunity for
replay. An opponent could eavesdrop on the network and capture a copy of the ticket-granting
ticket and then wait for the legitimate user to log out. Then the opponent
could forge the legitimate user’s network address and send the message of step
(3) to the TGS. This would give the opponent unlimited access to the resources
and files available to the legitimate user.
Similarly,
if an opponent captures a service-granting ticket
and uses it before it expires, the opponent has access to the corresponding service.
Thus, we arrive at an additional requirement. A network service
(the TGS or an application service) must be able to prove that the person using
a ticket is the same person to whom that ticket was issued.
The second problem
is that there may be a requirement for servers to authen-
ticate themselves to users. Without
such authentication, an opponent could
sabotage the configuration so that messages
to a server were directed
to another location. The false server
would then be in a position to act as a real server and capture any infor-
mation from the user and deny the true service
to the user.
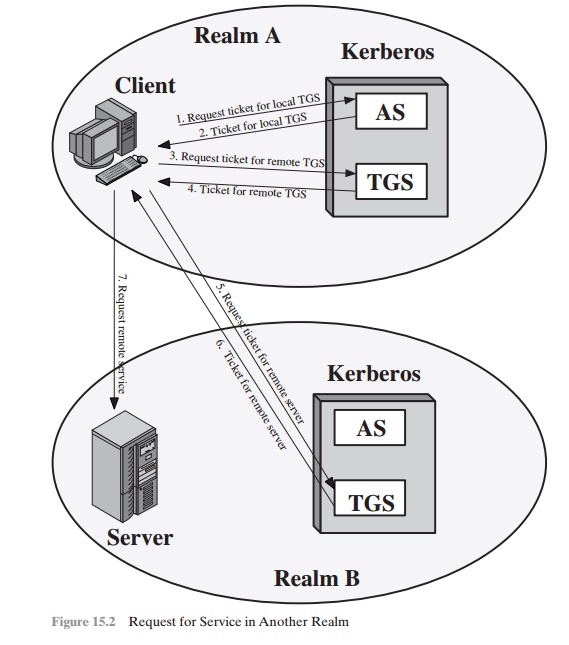
We examine these problems in turn and refer to Table 15.1, which shows the actual Kerberos
protocol.
First, consider the problem of captured ticket-granting tickets and the need to determine that the ticket presenter is the same as the client for whom the ticket was issued. The threat is that an opponent
will steal the ticket and use it before it expires.
To
get around this problem, let us have the AS provide both the client
and the TGS with
a secret piece
of information in a secure
manner. Then the client can prove its identity to the TGS by revealing the secret information—again in a secure
manner. An efficient way of accomplishing this is to use an encryption
key as the secure information; this is referred
to as a session key in Kerberos.
Table
15.1 Summary
of Kerberos Version 4 Message Exchanges
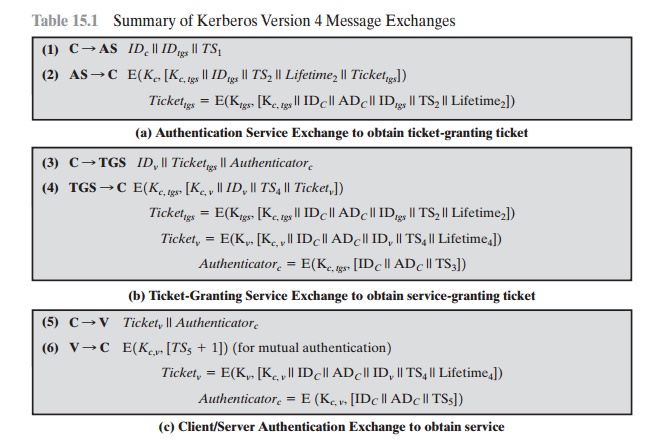
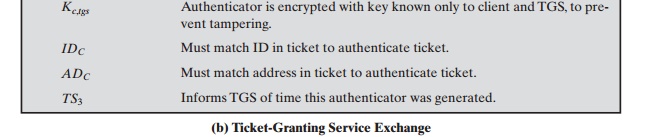
Table 15.1a shows the technique for distributing the session key. As before, the client sends a message to the AS requesting access to the TGS. The AS responds
with a message, encrypted with a key derived from the user’s password (Kc),
that contains the ticket.
The encrypted message
also contains a copy of the session
key, Kc,tgs, where the subscripts indicate that this is a session key
for C and TGS. Because this
session key is inside the message encrypted with Kc, only the user’s
client can read it. The same session
key is included in the ticket, which can be read
only by the TGS. Thus, the session
key has been securely delivered to both C and the TGS.
Note that several additional pieces of
information have been added to this first phase of the dialogue. Message (1) includes
a timestamp, so that the AS knows that the message is timely. Message (2) includes several
elements of the ticket in a form accessible to C. This enables
C to confirm that this ticket is for the TGS and to
learn its expiration time.
Armed with the ticket and the session key, C is ready to approach the TGS. As before, C sends the TGS a message that includes the ticket plus the ID of the requested service (message (3) in Table 15.1b). In addition, C transmits an authenti- cator, which includes the ID and address of C’s user and a timestamp. Unlike the ticket, which is reusable, the authenticator is intended for use only once and has a very short lifetime. The TGS can decrypt the ticket with the key that it shares with the AS. This ticket indicates that user C has been provided with the session key Kc,tgs. In effect, the ticket says, “Anyone who uses Kc,tgs must be C.” The TGS uses the session key to decrypt the authenticator. The TGS can then check the name and address from the authenticator with that of the ticket and with the network address of the incoming message. If all match, then the TGS is assured that the sender of the ticket is indeed the ticket’s real owner. In effect, the authenticator says, “At time TS3, I hereby use Kc,tgs.” Note that the ticket does not prove anyone’s identity but is a way to distribute keys securely. It is the authenticator that proves the client’s iden- tity. Because the authenticator can be used only once and has a short lifetime, the threat of an opponent stealing both the ticket and the authenticator for presentation later is countered.
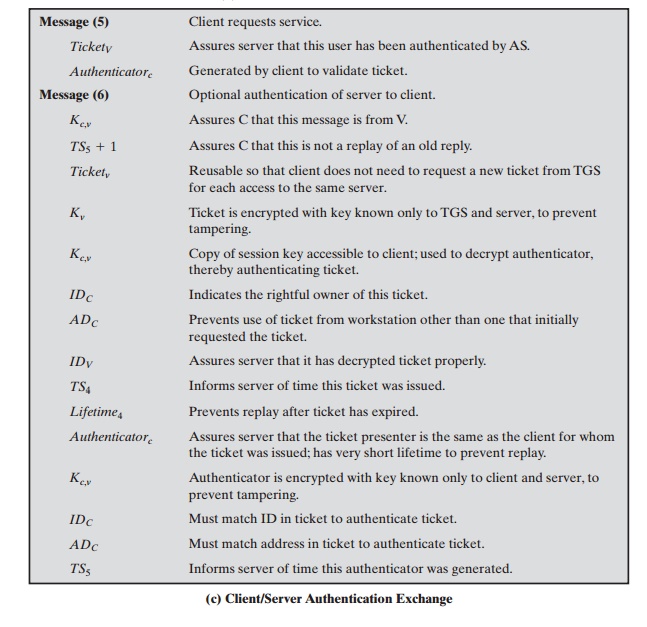
The reply from the TGS in message (4) follows the form of message (2). The message is encrypted with the session
key shared by the TGS and C and includes
a session key to be shared
between C and the server
V, the ID of V, and the timestamp
of the ticket. The ticket itself includes the same session
key.
C now has a reusable
service-granting ticket for V. When C presents this ticket,
as shown in message (5), it also sends an authenticator. The server can
decrypt the ticket, recover the session key, and decrypt the authenticator.
If mutual
authentication is required,
the server can reply as shown in message (6) of
Table 15.1. The server returns the value of the timestamp from the
authenticator, incremented by 1, and
encrypted in the session key. C can
decrypt this message to recover the incremented timestamp. Because the message
was encrypted by the session key, C is assured that it could have been created
only by V. The contents
of the message assure C that this is not a replay of an old reply.
Finally, at the conclusion of this process,
the client and server share a secret key. This key can be used to encrypt
future messages between the two or to exchange a new random session key for
that purpose.
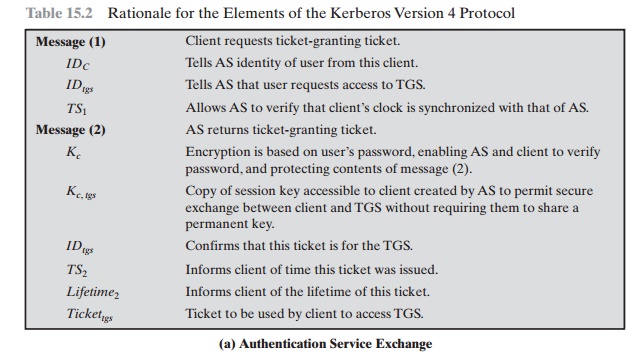
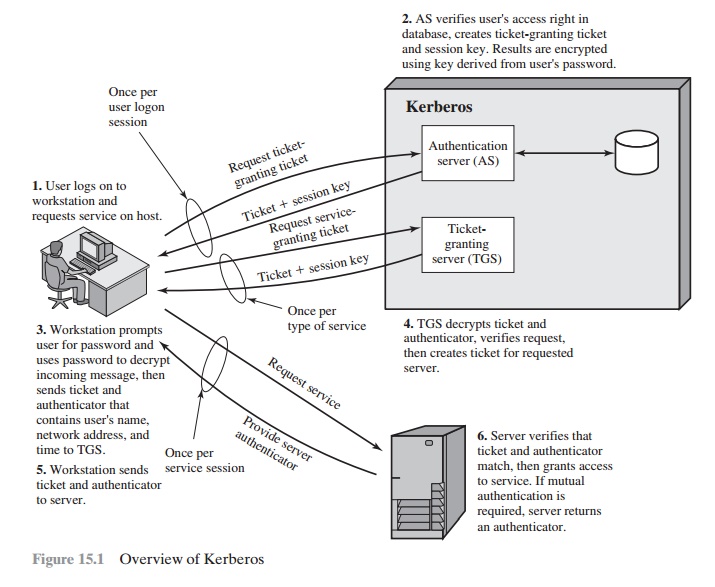
Table 15.2 summarizes the justification for
each of the elements in the Kerberos protocol, and Figure 15.1 provides a
simplified overview of the action.
KERBEROS
REALMS AND MULTIPLE KERBERI
A full-service Kerberos
environment consisting of a Kerberos server, a number of clients, and a number
of application servers requires the following:
1.
The Kerberos server must have the user ID and hashed passwords
of all partic- ipating users in its database.
All users are registered with the Kerberos
server.
2.
The Kerberos server must share a secret key with each server. All servers are registered with the Kerberos server.
Such an environment is referred
to as a Kerberos realm. The concept
of realm can be explained as
follows. A Kerberos realm is a set of managed nodes
that share the same Kerberos database. The Kerberos database
resides on the Kerberos master computer system, which should be
kept in a physically secure room. A read-only
copy of the Kerberos database might also reside on other Kerberos
computer systems. However, all changes to the database must be made on the master
computer system. Changing or accessing
the contents of a Kerberos database requires the Kerberos master password. A related concept is that of a Kerberos principal, which is a service or user
that is known to
the Kerberos system. Each Kerberos principal is identified by its principal name.
Principal names consist of three parts: a service or user name, an instance name, and a realm name
Networks of clients and
servers under
different administrative organiza-
tions typically
constitute different realms. That is, it generally is not practical or does not conform to
administrative policy to
have users and servers
in one administrative domain
registered with a Kerberos server elsewhere. However,
users in one realm may need
access to servers in other realms, and some servers may be willing to provide service
to users from other realms, provided that those users are authenticated.
Kerberos
provides a mechanism for supporting such interrealm authentication. For two realms to support interrealm authentication, a third
requirement is added:
2.
The
Kerberos server in each interoperating realm shares a secret key
with the server in the other realm.The
two Kerberos servers are registered with each other.
The scheme requires
that the Kerberos
server in one realm trust
the Kerberos server in the
other realm to authenticate its users. Furthermore, the participating servers
in the second realm must also be willing to trust the Kerberos server in the first realm.
With these ground rules in place, we can
describe the mechanism as follows (Figure 15.2): A user wishing
service on a server in another realm
needs a ticket
for that server. The user’s client follows
the usual procedures to gain access to the local
TGS and then requests a ticket-granting ticket for a remote TGS (TGS in another
realm). The client can then apply to the remote TGS for a service-granting ticket for
the desired server in the realm of the remote
TGS.
The details of the exchanges illustrated in Figure
15.2 are as follows (compare Table 15.1).
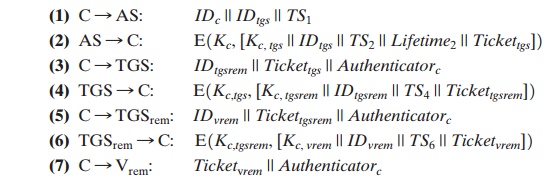
The ticket presented to the remote server (Vrem)
indicates the realm in which the user was originally authenticated. The server
chooses whether to honor the remote request.
One problem presented by the foregoing
approach is that it does not scale well to many
realms. If there are N realms, then
there must be N(N - 1)/2 secure key exchanges
so that each Kerberos
realm can interoperate with all other Kerberos realms.
Kerberos Version 5
Kerberos version 5 is specified in RFC 4120
and provides a number of improve- ments over version 4 [KOHL94]. To begin, we
provide an overview of the changes from version 4 to version 5 and then look at
the version 5 protocol.
DIFFERENCES BETWEEN VERSIONS 4 AND
5 Version 5 is intended to address the limitations of
version 4 in two areas: environmental shortcomings and technical deficiencies.
Let us briefly summarize the improvements in each area.
Kerberos version 4 was developed for use within
the Project Athena
environ- ment and, accordingly, did not fully
address the need to be of general
purpose. This led to the following environmental shortcomings.
Encryption system dependence: Version 4 requires the use of DES. Export
restriction on DES as well as doubts about the strength of DES were thus of concern. In version 5, ciphertext is tagged with an encryption-type identifier
so that any encryption technique may be used. Encryption keys are tagged with a type and a length, allowing the same key to be used in different
algorithms and allowing the specification of different variations on a
given algorithm.
1.
Internet protocol dependence: Version 4 requires the use of Internet
Protocol (IP) addresses. Other address types, such as the ISO network address, are not accommodated. Version
5 network addresses
are tagged with type and length,
allowing any network
address type to be used.
2.
Message byte ordering: In version 4, the sender
of a message employs a byte
ordering of its own choosing
and tags the message to indicate least
significant byte in lowest address or most significant byte in lowest
address. This tech- niques works but
does not follow
established conventions. In version 5, all mes- sage structures are defined using
Abstract Syntax Notation One (ASN.1) and Basic Encoding Rules (BER),
which provide an unambiguous byte ordering.
3.
Ticket lifetime: Lifetime values in version 4 are encoded in an 8-bit quantity in units
of five minutes. Thus, the maximum
lifetime that can be expressed is 28 * 5 = 1280 minutes (a little
over 21 hours).
This may be inadequate for some applications (e.g., a long-running simulation that requires valid Kerberos creden-
tials throughout execution). In version
5, tickets include
an explicit start time and end
time, allowing tickets with arbitrary lifetimes.
4.
Authentication forwarding: Version 4 does not allow credentials issued to one client to be forwarded to some other
host and used by some other client.
This capability would
enable a client
to access a server and have that server access
another server on behalf
of the client. For example, a client
issues a request
to a print server that then accesses
the client’s file from a file server, using the client’s credentials for access.
Version 5 provides
this capability.
5.
Interrealm
authentication: In version 4, interoperability among N realms
requires on the order of N 2 Kerberos-to-Kerberos relationships, as described earlier. Version 5 supports a
method that requires fewer relationships, as described shortly.
Apart from these environmental limitations, there are technical deficiencies in the version 4 protocol
itself. Most of these deficiencies were documented in [BELL90], and version 5 attempts
to address these.
The deficiencies are the following.
1.
Double encryption: Note in Table 15.1 [messages (2) and (4)]
that tickets pro- vided to clients are encrypted
twice—once with the secret key of the target server
and then again with a secret key known
to the client. The second encryption is not necessary and is computationally wasteful.
2.
PCBC encryption: Encryption in version 4 makes use of a nonstandard mode of DES known as propagating cipher block chaining (PCBC).9 It has been demon- strated that this mode is vulnerable
to an attack involving the interchange of ciphertext blocks [KOHL89]. PCBC was intended to provide
an integrity check as part of the encryption
operation.Version 5 provides
explicit integrity mechanisms,
allowing the standard CBC mode to be used for encryption. In particular, a check- sum or hash code is attached to the message prior to encryption using CBC.
1.
Session
keys: Each ticket includes a session key that is used by the
client to encrypt the authenticator sent to the service associated with that ticket. In addi- tion, the session key may subsequently be used by the client and the server to protect
messages passed during that session. However,
because the same ticket may be used repeatedly to gain service
from a particular server, there is the risk that an opponent will replay messages
from an old session to the client
or the server. In version
5, it is possible
for a client and server
to negotiate a subsession
key, which is to be used only for that one connection. A new access by the client
would result in the use of a new subsession key.
2.
Password attacks: Both versions are vulnerable to a password
attack. The mes-
sage from the AS to the client includes material
encrypted with a key based on
the client’s password.10 An opponent can capture this message and attempt to decrypt it by trying
various passwords. If the result
of a test decryption is of the proper form, then the opponent has discovered the client’s password
and may subsequently use it to
gain authentication credentials from Kerberos. This is the same type of password attack described in Chapter 20, with the same kinds of countermeasures being applicable.
Version 5 does provide a mechanism known as preauthentication, which should make password attacks
more diffi- cult, but it does not prevent them.
THE
VERSION
5 AUTHENTICATION
DIALOGUE
Table 15.3 summarizes the
basic version 5 dialogue. This is best explained by comparison with version 4
(Table 15.1).
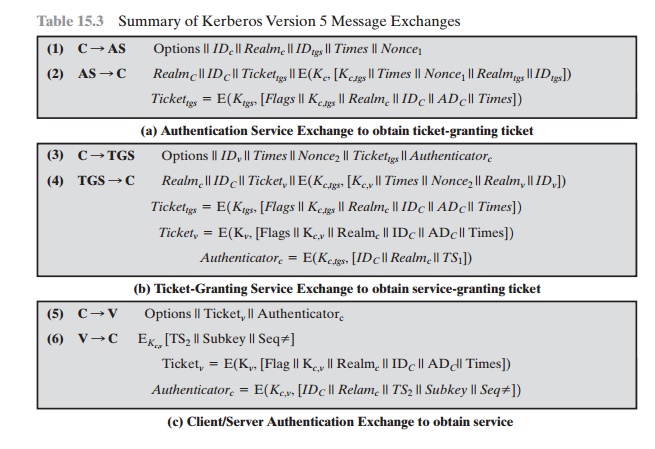
First, consider the authentication
service
exchange. Message (1) is a client request for a ticket-granting ticket. As before,
it includes the ID of the user and the TGS. The following new elements are added:
•
Realm: Indicates realm of user
•
Options: Used to request
that certain flags
be set in the returned
ticket
•
Times: Used by the client to request the following time settings in the ticket:
—from:
the desired start time for the requested ticket
—till: the requested
expiration time for the requested ticket
—rtime: requested
renew-till time
•
Nonce: A random value to
be repeated in message (2)
to assure that the response is fresh and has not been replayed
by an opponent
Message (2) returns a ticket-granting ticket, identifying
information for the client, and a block encrypted
using the encryption key based on the user’s password.
This block includes the session
key to be used between
the client and the TGS, times specified in message (1), the nonce from message
(1), and TGS identifying informa- tion. The ticket itself includes
the session key, identifying information for the client,
the requested time values, and flags that reflect the status of this
ticket and the requested options.
These flags introduce significant new functionality to version 5. For
now, we defer a discussion of
these flags and concentrate on the overall struc- ture of the version
5 protocol.
Let us now compare the ticket-granting service exchange for versions 4 and
3.
We
see that message (3) for both versions
includes an authenticator, a ticket, and the name of the requested service. In
addition, version 5 includes requested times
and options for the ticket and a nonce—all with functions similar
to those of message
(1). The authenticator itself is
essentially the same as the one used
in version 4.
Message (4) has the same structure as
message (2). It returns a ticket plus information needed by the client, with the information encrypted using the session
key now shared by the client and the TGS.
Finally, for the client/server authentication exchange, several new features
appear in version
5. In message (5), the client may request as an option that mutual authentication is required. The authenticator includes several new fields:
•
Subkey: The client’s choice for an encryption key to be used to
protect this specific application session. If this field is omitted, the
session key from the ticket (Kc,v) is used.
•
Sequence number: An optional field that specifies the starting sequence num- ber to be used by the server for messages
sent to the client during this session. Messages may be sequence
numbered to detect replays.
•
If mutual
authentication is required, the server responds with message (6). This message
includes the timestamp from the authenticator. Note that in version 4, the
timestamp was incremented by one. This
is not necessary in version
5, because the nature of the
format of messages is such that it is not possible for an opponent to create message (6) without knowledge of
the appropriate
encryption keys. The subkey
field, if present, overrides the subkey field, if present, in message (5).
•
The optional
sequence number field specifies the starting sequence number to be used by the
client.
•
TICKET FLAGS
The flags field included in
tickets in version 5 supports expanded functionality compared to that available
in version 4. Table 15.4 summarizes the flags that may be included in a ticket.
•
The INITIAL flag
indicates that this ticket was issued by the AS, not by the TGS. When a client
requests a service-granting ticket from the TGS, it presents a ticket-granting
ticket obtained from the AS. In version 4, this was the only way to obtain a
service-granting ticket. Version 5 provides the additional capability that the
client can get a service-granting ticket directly from the AS. The utility of
this is as follows: A server, such as a password-changing server, may wish to
know that the client’s password was recently tested.
•
The PRE-AUTHENT flag, if set, indicates that when the AS received
the ini- tial request [message
(1)], it authenticated the client before issuing a ticket. The exact form of
this preauthentication is left unspecified. As an example, the MIT implementation of version 5 has
encrypted timestamp preauthentication, enabled by default. When a user wants
to get a ticket, it has to send to the AS a preauthenti- cation block containing a
random confounder, a version number, and a timestamp all encrypted in the client’s password-based key. The AS decrypts the block and will
not send a ticket-granting ticket
back unless the timestamp in the preauthentication block is within the allowable time skew (time interval to account for clock drift and
network delays). Another possibility is the use of a smart card that generates
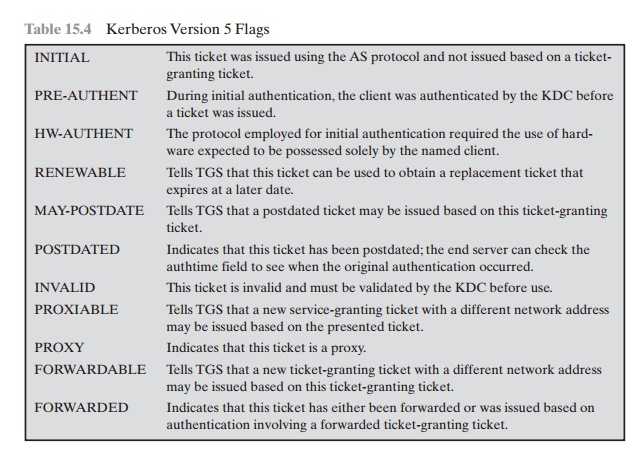
continually
changing passwords that are included
in the preauthenticated messages.
The passwords generated by the card can be based on a user’s password but
be transformed by the card so that,
in effect, arbitrary passwords are used. This pre- vents an attack based
on easily guessed
passwords. If a smart card or similar
device was used, this is indicated
by the HW-AUTHENT flag.
When a ticket has a long lifetime, there is
the potential for it to be stolen and
used by an opponent for a considerable period. If a short lifetime is used to
lessen the threat, then
overhead is involved
in acquiring new tickets. In the case of a ticket-
granting ticket, the client would either have to store the user’s secret key, which is clearly risky, or repeatedly ask the user for a password. A compromise scheme
is the use of renewable tickets. A ticket with the RENEWABLE flag set
includes two expiration times: one for this specific ticket and one that
is the latest permissible value for an expiration time.
A client can have the ticket renewed
by presenting it to
the TGS with a requested new expiration time.
If the new time is within the limit of the
latest permissible value,
the TGS can issue a new ticket
with a new session time and a later specific expiration
time. The advantage of this mechanism is that the
TGS may refuse
to renew a ticket reported
as stolen.
A client may
request that the AS provide a ticket-granting
ticket with the MAY-POSTDATE flag set. The client can then use this ticket to request a ticket that is flagged as POSTDATED and INVALID from
the TGS. Subsequently, the client
may submit the postdated ticket for validation. This scheme can be useful for
run- ning a long batch job on a server that requires a ticket periodically. The client can obtain a number of tickets for this session
at once, with spread out time values.
All but the first ticket are initially invalid. When the execution
reaches a point in time when a new ticket is required, the client can get the
appropriate ticket validated. With this approach, the client does not have to
repeatedly use its ticket-granting ticket to obtain
a service-granting ticket.
In version 5, it is possible for a server to act as a proxy on behalf of a client,
in effect adopting the credentials and privileges of the client
to request a service from another server. If a client wishes
to use this mechanism, it requests a ticket-granting
ticket with the PROXIABLE flag set. When this ticket is presented
to the TGS, the TGS
is permitted to issue a service-granting ticket with a different network
address; this latter ticket
will have its PROXY flag set. An application receiving such a ticket
may accept it or require additional authentication to provide an audit trail.11
The proxy concept is a limited case of the
more powerful forwarding proce- dure. If a
ticket is set with the FORWARDABLE
flag, a TGS can issue to the requestor
a ticket-granting ticket with a different network address and the FOR- WARDED flag set. This ticket then can be
presented to a remote TGS. This
capa- bility allows a client to gain access to a server on another realm
without requiring that each Kerberos
maintain a secret key with
Kerberos servers in every other realm. For example, realms could be structured hierarchically. Then a
client could walk up the tree to a common node and then back down to reach a
target realm. Each step of the walk would involve
forwarding a ticket-granting ticket to the next
TGS in the path.
Related Topics