Chapter: Cryptography and Network Security Principles and Practice : Network and Internet Security : Electronic Mail Security
DomainKeys Identified Mail
DOMAINKEYS IDENTIFIED MAIL
DomainKeys
Identified Mail (DKIM)
is a specification for cryptographically signing e-mail messages,
permitting a signing
domain to claim
responsibility for a message in the
mail stream. Message
recipients (or agents
acting in their
behalf) can verify
the signature by querying
the signer’s domain directly to retrieve the appropriate public key and thereby can confirm that the message
was attested to by a party in posses-
sion of the private key for the signing
domain. DKIM is a proposed Internet Standard (RFC 4871: DomainKeys Identified Mail (DKIM) Signatures). DKIM has been widely
adopted by a range of e-mail providers, including corporations, govern- ment agencies, gmail,
yahoo, and many Internet
Service Providers (ISPs).
This section provides
an overview of DKIM. Before
beginning our discussion of DKIM, we introduce the standard Internet
mail architecture. Then
we look at the
threat that DKIM is intended
to address, and finally provide
an overview of DKIM
operation.
Internet Mail Architecture
To understand the operation of
DKIM, it is useful to have a basic grasp of the Internet mail architecture, which is currently
defined in [CROC09].
This subsection provides an overview of the basic
concepts.
At its most fundamental level,
the Internet mail architecture consists
of a user world in the form of Message User Agents (MUA), and the transfer world, in the form of the
Message Handling Service (MHS), which
is composed of Message Transfer Agents (MTA).
The MHS accepts a message from one user and delivers
it to one or more other users, creating a virtual MUA-to-MUA exchange
environ- ment. This architecture involves three types of interoperability. One is directly between users: messages must be
formatted by the MUA on behalf of
the message author so that the message can be displayed to the message
recipient by the destina-
tion MUA. There are also
interoperability requirements between the MUA
and the MHS—first when a message
is posted from an MUA to the MHS and later when it is delivered from the MHS to the
destination MUA. Interoperability is
required among the MTA components along the transfer
path through the MHS.
Figure 18.9 illustrates the key components
of the Internet mail architecture, which include the following.
•
Message User Agent (MUA): Works on behalf
of user actors
and user applica- tions. It is their representative within the e-mail
service. Typically, this function is housed in the user’s computer
and is referred to as a client e-mail program
or a local network
e-mail server.
The author MUA formats a message and performs
initial submission into the MHS via a MSA. The recipient MUA processes received mail
for storage and/or
display to the
recipient user.
•
Mail Submission Agent
(MSA): Accepts the message
submitted by an MUA and enforces the
policies of the hosting
domain and the requirements of Internet standards. This
function may be located together
with the MUA or as
a separate functional model. In the latter
case, the Simple Mail Transfer Protocol (SMTP)
is used between
the MUA and the MSA.
•
Message Transfer Agent
(MTA): Relays mail for one application-level hop. It is like a packet switch or IP router in that its job is
to make routing assess- ments and to move the message closer to the recipients. Relaying
is performed by a sequence of
MTAs until the message reaches a destination MDA. An MTA also adds trace
information to the message header.
SMTP is used between MTAs and between an MTA and
an MSA or MDA.
•
Mail Delivery Agent (MDA): Responsible for transferring the message from the MHS to the MS.
•
Message Store (MS): An
MUA can employ a long-term MS. An MS can be located on a remote
server or on the same machine as the MUA. Typically, an MUA
retrieves messages from a remote server using POP (Post Office Protocol) or IMAP (Internet Message Access Protocol).
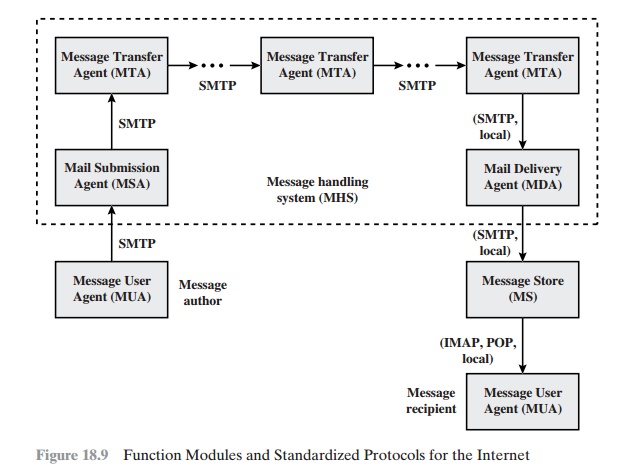
Two other concepts need to be defined. An
administrative
management domain (ADMD) is
an Internet e-mail provider. Examples include a department that operates
a local mail relay (MTA), an IT department that operates an enterprise
mail relay, and an ISP that operates a public shared e-mail service.
Each ADMD can have
different operating policies and trust-based
decision making. One obvious example is the distinction between mail that is exchanged within an organization and mail that is exchanged between independent organizations. The rules for handling the two types of traffic tend to be quite different.
The Domain Name System
(DNS) is a directory lookup service that provides
a mapping between the name of a host on the Internet
and its numerical address.
E-
mail Threats
RFC 4684 (Analysis of Threats Motivating DomainKeys Identified Mail)
describes the threats being addressed by DKIM in terms of the
characteristics, capabilities, and location of potential attackers.
CHARACTERISTICS RFC
characterizes the range of attackers on a spectrum of three levels of threat.
At the low end are attackers who simply want
to send e-mail that a recipient does not want to receive.
The attacker can use one of a number
of commercially available tools
that allow the sender to falsify the origin address
of messages. This makes it difficult for the receiver
to filter spam on the basis of originating
address or domain.
1.
At the next level
are professional senders of bulk spam mail. These attackers often operate as commercial enterprises and send messages on behalf of third
parties. They employ more comprehensive tools for attack, including Mail Transfer
Agents (MTAs) and registered domains and networks
of compromised computers (zombies)
to send messages
and (in some cases) to harvest
addresses to which to send.
2.
The most sophisticated and
financially motivated senders
of messages are
those who stand to receive substantial financial benefit, such as from an e-mail-based fraud scheme. These attackers can
be expected to employ all of the above mechanisms and additionally may attack the
Internet infrastructure itself,
including DNS cache-poisoning attacks and IP routing
attacks.
CAPABILITIES RFC
4686 lists the following as capabilities that an attacker might have.
1.
Submit
messages to MTAs and Message
Submission Agents (MSAs) at multiple
locations in the Internet.
2.
Construct arbitrary
Message Header fields, including those claiming to be mailing lists,
resenders, and
other mail agents.
3.
Sign messages on behalf of domains
under their control.
4.
Generate substantial numbers of either unsigned or apparently signed messages
that might be used to attempt
a denial-of-service attack.
5.
Resend messages that may have been previously signed by the domain.
6.
Transmit messages using any envelope information desired.
7.
Act as an authorized submitter for messages
from a compromised computer.
8.
Manipulation of IP routing. This could be used to submit messages from specific
IP addresses or difficult-to-trace addresses, or to cause diversion of messages
to a specific domain.
9.
Limited
influence over portions of DNS using
mechanisms such as cache poisoning. This might be used to influence message
routing or to falsify adver- tisements of DNS-based keys or signing
practices.
10.
Access to significant computing resources, for example, through the conscription of worm-infected “zombie” computers. This
could allow the “bad actor” to perform various types of brute-force attacks.
11.
Ability to eavesdrop on existing traffic,
perhaps from a wireless network.
LOCATION DKIM focuses primarily on attackers located
outside of the
administrative units of the claimed originator and the recipient.These administrative units frequently correspond to the protected
portions of the network adjacent to the originator and recipient. It is in this area that the trust relationships
required for authenticated message submission do not exist and do not scale
adequately to be practical. Conversely, within
these administrative units, there are other mechanisms (such as
authenticated message submission) that are easier to deploy and more likely to
be used than DKIM. External “bad actors” are usually attempting to exploit the “any-
to-any” nature of e-mail that motivates most recipient MTAs to accept messages
from anywhere for delivery
to their local
domain. They may generate
messages without signatures, with incorrect signatures, or with correct
signatures from domains
with little traceability. They may also pose as mailing
lists, greeting cards, or other agents that legitimately send or resend messages on behalf of others.
DKIM Strategy
DKIM is designed to provide an e-mail authentication technique that is transparent to the end user. In essence, a user’s e-mail message is signed by a private key of the administrative domain from which the e-mail originates. The signature covers all of the content of the message and some of the RFC 5322 message headers. At the receiving end, the MDA can access the corresponding public key via a DNS and ver- ify the signature, thus authenticating that the message comes from the claimed administrative domain. Thus, mail that originates from somewhere else but claims to come from a given domain will not pass the authentication test and can be rejected. This approach differs from that of S/MIME and PGP, which use the originator’s pri- vate key to sign the content of the message. The motivation for DKIM is based on the following reasoning.5
1.
S/MIME depends
on both the
sending and receiving users employing S/MIME. For almost all users, the bulk of incoming
mail does not use S/MIME,
and the bulk of the mail the user wants to send is to recipients not using S/MIME.
2.
S/MIME signs only the message content.
Thus, RFC 5322 header information
concerning origin can
be compromised.
3.
DKIM is not implemented in client
programs (MUAs) and is therefore transpar-
ent to the user; the user need take no action.
4.
DKIM applies to all mail from cooperating domains.
5.
DKIM allows good
senders to prove that they did send a particular message and to prevent forgers
from masquerading as good senders.
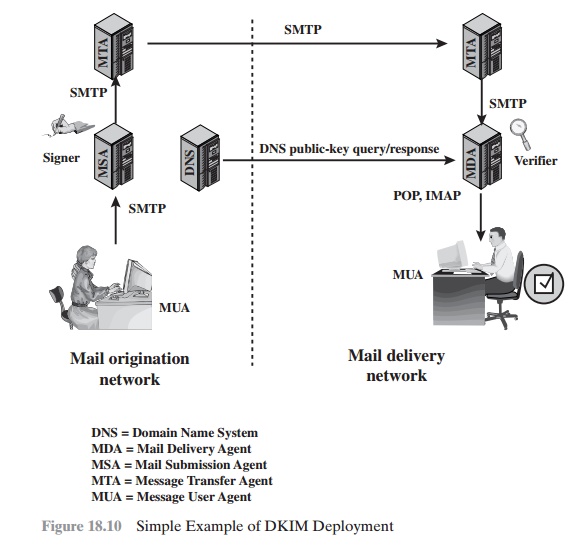
Figure 18.10 is a simple example of the operation
of DKIM. We begin with a message
generated by a user and transmitted into the MHS to an MSA that is within the users administrative domain.
An e-mail message
is generated by an e-mail
client program. The content of the message,
plus selected RFC 5322 headers,
is signed by the
e-mail provider using the provider’s private key. The signer is associated with a
domain, which could be a corporate local network, an ISP, or a public e-mail facility
such as gmail. The signed message
then passes through
the Internet via a sequence of MTAs. At the destination, the MDA
retrieves the public key for the incoming signature and verifies the signature before passing the message on to the destination
e-mail client. The default signing algorithm is RSA with
SHA-256. RSA with SHA-1
also may be used.
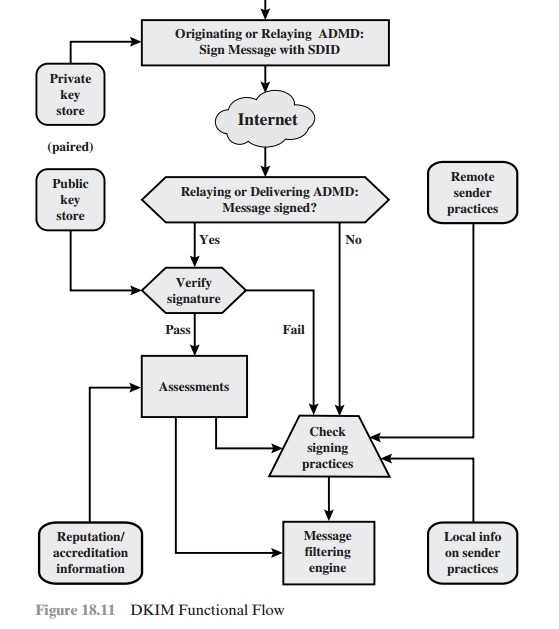
DKIM Functional Flow
Figure 18.11 provides a more detailed look
at the elements of DKIM operation. Basic message processing is divided between
a signing Administrative Management Domain (ADMD) and a verifying ADMD. At its simplest, this is between the
originating ADMD and the delivering ADMD, but it can
involve other ADMDs in the handling path.
Signing is performed
by an authorized module within the signing
ADMD and uses private information from a Key Store. Within the originating ADMD, this might be performed
by the MUA, MSA, or an MTA. Verifying is performed by an
authorized module within the verifying
ADMD. Within a delivering ADMD, verify- ing might be performed by an MTA, MDA, or MUA. The module verifies
the signa- ture or determines whether
a particular signature
was required. Verifying the signa- ture uses public information from the Key Store. If the signature
passes, reputation information
is used to assess the signer and that information is passed to the mes- sage filtering
system. If the signature fails or there is no signature using the author’s domain, information about signing
practices related to the author can be retrieved remotely and/or
locally, and that information is passed to the message
filtering sys- tem. For example,
if the sender (e.g., gmail) uses DKIM but no DKIM signature
is present, then the message may be considered fraudulent.
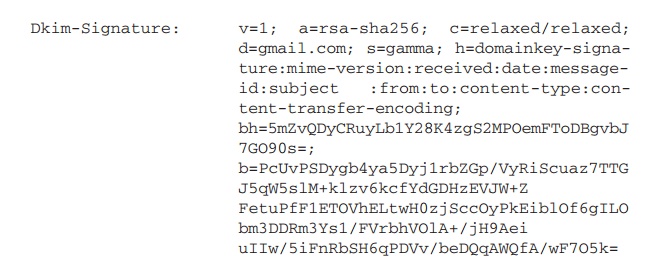
The signature is inserted into the RFC 5322 message as an
additional header entry, starting with the keyword
Dkim-Signature. You can view examples from your
own incoming mail by using the View Long
Headers (or similar wording)
option for an incoming message.
Here is an example:
Before a message is signed, a process known
as canonicalization is per- formed on both the header and body of the RFC 5322
message. Canonicalization is necessary to deal with the possibility of minor
changes in the message made en route, including character encoding, treatment
of trailing white space in message lines, and the “folding” and “unfolding” of
header lines. The intent of canonical- ization is to make a minimal
transformation of the message (for the purpose of signing; the message itself
is not changed, so the canonicalization must be per- formed again by the
verifier) that will give it its best chance of producing the same canonical
value at the receiving end. DKIM defines two header canonical- ization
algorithms (“simple” and “relaxed”) and two for the body (with the same names).
The simple algorithm tolerates almost no modification, while the relaxed
tolerates common modifications.
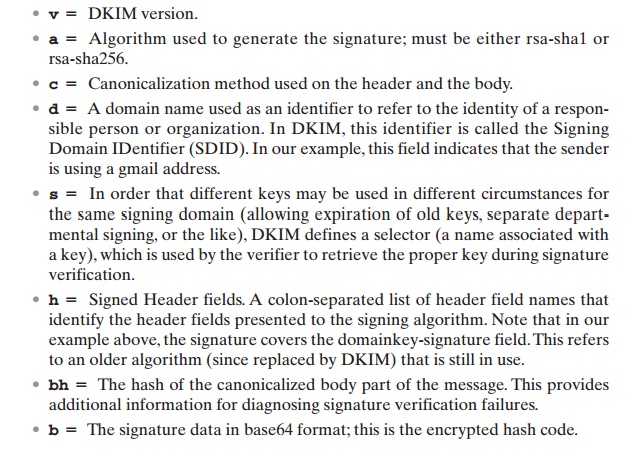
The signature includes a number of fields.
Each field begins with a tag consist- ing of a tag code followed by an equals
sign and ends with a semicolon. The fields include the following:
Related Topics