Chapter: Computer Networks : Network Layer
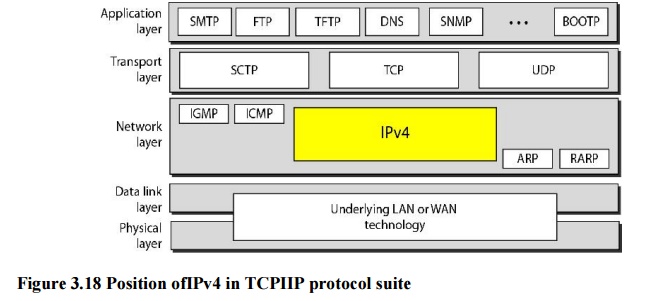
IPv4 (The Internet Protocol version 4)
IPv4:
The
Internet Protocol version 4 (IPv4) is the delivery mechanism used by the TCP/IP
protocols.
IPv4 is
an unreliable and connectionless datagram protocol-a best-effort delivery
service. The term best-effort means
that IPv4 provides no error control or flow control (except for error detection
on the header). IPv4 assumes the unreliability of the underlying layers and
does its best to get a transmission through to its destination, but with no
guarantees.
1. Datagram
Packets
in the IPv4 layer are called datagrams. A datagram is a variable-length packet
consisting of two parts: header and data. The header is 20 to 60 bytes in
length and contains information essential to routing and delivery. It is
customary in TCP/IP to show the header in 4-byte sections.
· Version (VER): This
4-bit field defines the version of the IPv4 protocol. Currently theversion is
4. However, version 6 (or IPv6) may totally replace version 4 in the future.
This field tells the IPv4 software running in the processing machine that the
datagram has the format of version 4. All fields must be interpreted as
specified in the fourth version of the protocol. If the machine is using some
other version of IPv4, the datagram is discarded rather than interpreted
incorrectly
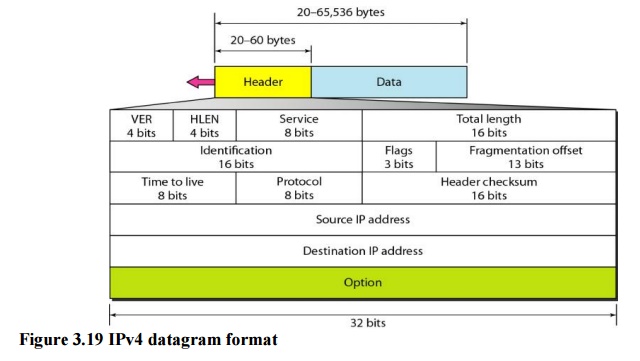
· Header length (HLEN): This
4-bit field defines the total length of the datagram headerin 4-byte words.
This field is needed because the length of the header is variable (between 20
and 60 bytes). When there are no options, the header length is 20 bytes, and
the value of this field is 5 (5 x 4 = 20). When the option field is at its
maximum size, the value of this field is 15 (15 x 4 = 60)
· Services: IETF has
changed the interpretation and name of this 8-bit field. This field,previously
called service type, is now called differentiated services.
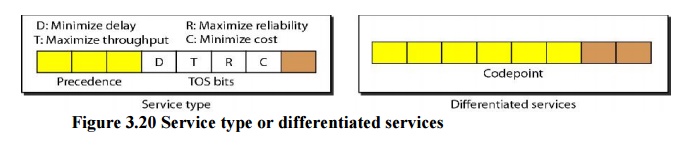
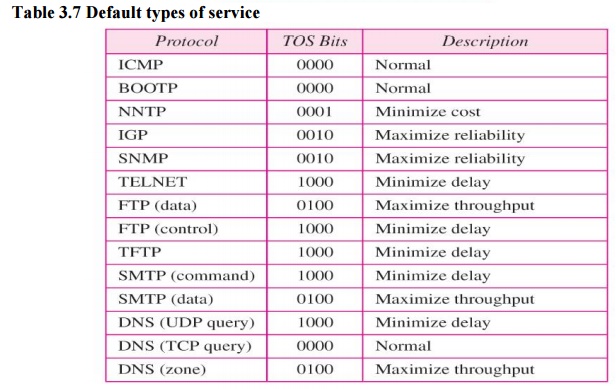
1. Service Type
In this
interpretation, the first 3 bits are called precedence bits. The next 4 bits
are called type of service (TOS) bits, and the last bit is not used.
·
Precedence
is a
3-bit subfield ranging from 0 (000 in binary) to 7 (111 in binary).The
precedence defines the priority of the datagram in issues such as congestion.
·
TOS bits are a
4-bit subfield with each bit having a special meaning. Although abit can be
either 0 or 1, one and only one of the bits can have the value of 1 in each
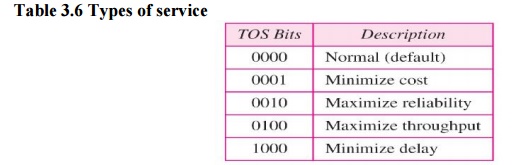
datagram. The bit patterns and their interpretations are given in Table 3.4.
With only 1 bit set at a time, we can have five different types of services.
2. Differentiated Services
In this
interpretation, the first 6 bits make up the code point subfield, and the last
2 bits are not used. The code point subfield can be used in two different ways.
·
When the 3 rightmost bits are 0s, the 3 leftmost
bits are interpreted the same as the precedence bits in the service type
interpretation. In other words, it is compatible with the old interpretation.
·
When the 3 rightmost bits are not all 0s, the 6
bits define 64 services based on the priority assignment by the Internet or
local authorities. The first category contains 32 service types; the second and
the third each contain 16. The first category (numbers 0, 2, 4, ... ,62) is
assigned by the Internet authorities (IETF). The second category (3, 7, 11, 15,
, 63) can be used by local authorities (organizations). The third category (1,
5, 9, .., 61) is temporary and can be used for experimental purposes
· Total length. This is
a In-bit field that defines the total length (header plus data) of theIPv4
datagram in bytes. To find the length of the data coming from the upper layer,
subtract the header length from the total length. The header length can be
found by multiplying the value in the HLEN field by 4.
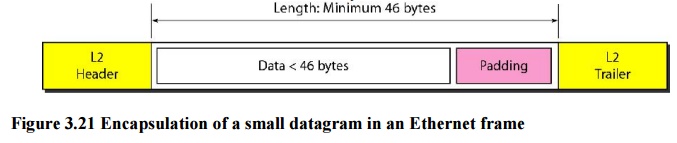
If the
size of an IPv4 datagram is less than 46 bytes, some padding will be added to
meet this requirement. In this case, when a machine decapsulates the datagram,
it needs to check the total length field to determine how much is really data
and how much is padding.
·
Identification. This
field is used in fragmentation.
·
Flags. This
field is used in fragmentation.
·
Fragmentation
offset. This field is used in fragmentation.
·
Time to
live: A
datagram has a limited lifetime in its travel through an internet.This field
was originally designed to hold a timestamp, which was decremented by each
visited router. The datagram was discarded when the value became zero.
·
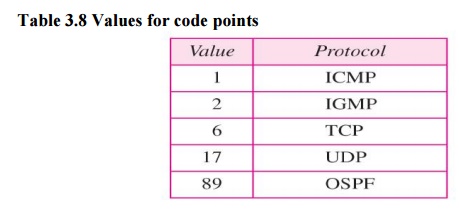
Protocol:
This
8-bit field defines the higher-level protocol that uses the servicesof the IPv4
layer. An IPv4 datagram can encapsulate data from several higher-level
protocols such as TCP, UDP, ICMP, and IGMP. This field specifies the final
destination protocol to which the IPv4 datagram is delivered. In other words,
since the IPv4 protocol carries data from different other protocols.
·
Checksum:
The
checksum concept and its calculation.
·
Source
address: This 32-bit field defines the IPv4 address of the source. Thisfield must
remain unchanged during the time the IPv4 datagram travels from the source host
to the destination host.
·
Destination
address: This 32-bit field defines the IPv4 address of the destination
Example 3.12
An IPv4
packet has arrived with the first 8 bits as shown: 01000010
The
receiver discards the packet. Why?
Solution
There is
an error in this packet. The 4 leftmost bits (0100) show the version, which is
correct. The next 4 bits (0010) show an invalid header length (2 x 4 =8). The
minimum number of bytes in the header must be 20. The packet has been corrupted
in transmission.
Example 3.13
In an
IPv4 packet, the value of HLEN is 1000 in binary. How many bytes of options are
being carried by this packet?
Solution
The HLEN
value is 8, which means the total number of bytes in the header is 8 x 4, or 32
bytes. The first 20 bytes are the base header; the next 12 bytes are the
options.
Example 3.14
In an
IPv4 packet, the value of HLEN is 5, and the value of the total length field is
0x0028. How many bytes of data are being carried by this packet?
Solution
The HLEN
value is 5, which means the total number of bytes in the header is 5 x 4, or 20
bytes (no options). The total length is 40 bytes, which means the packet is
carrying 20 bytes of data (40- 20).
Example 3.15
An IPv4
packet has arrived with the first few hexadecimal digits as shown.
0x45000028000100000102 ...
How many
hops can this packet travel before being dropped? The data belong to what
upper-layer protocol?
Solution
To find
the time-to-live field, we skip 8 bytes (16 hexadecimal digits). The
time-to-live field is the ninth byte, which is 01. This means the packet can
travel only one hop. The protocol field is the next byte (02), which means that
the upper-layer protocol is IGMP..
Fragmentation
A
datagram can travel through different networks. Each router decapsulates the
IPv4 datagram from the frame it receives, processes it, and then encapsulates
it in another frame. The format and size of the received frame depend on the
protocol used by the physical network through which the frame has just
traveled. The format and size of the sent frame depend on the protocol used by
the physical network through which the frame is going to travel. For example,
if a router connects a LAN to a WAN, it receives a frame in the LAN format and
sends a frame in the WAN format.
Checksum
The
implementation of the checksum in the IPv4 packet follows the same principles.
First, the value of the checksum field is set to O. Then the entire header is
divided into 16-bit sections and added together. The result (sum) is
complemented and inserted into the checksum field.
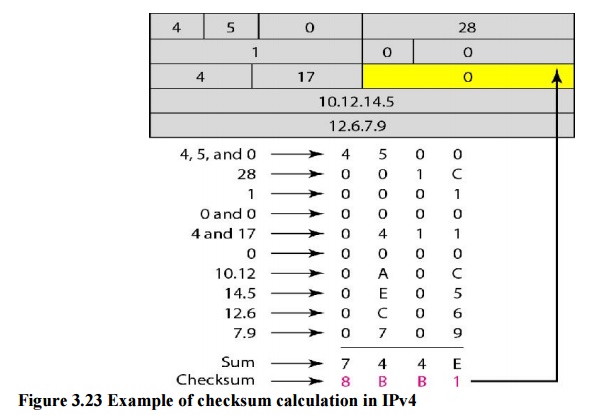
Example 3.16
Figure
3.23 shows an example of a checksum calculation for an IPv4 header without
options. The header is divided into 16-bit sections. All the sections are added
and the sum is complemented.
The
result is inserted in the checksum field.
Options
The
header of the IPv4 datagram is made of two parts: a fixed part and a variable
part. The fixed part is 20 bytes long and was discussed in the previous
section. The variable part comprises the options that can be a maximum of 40
bytes. Options, as the name implies, are not required
for a
datagram. They can be used for network testing and debugging. Although options
are not a required part of the IPv4 header, option processing is required of
the IPv4 software. This means that all implementations must be able to handle
options if they are present in the header.
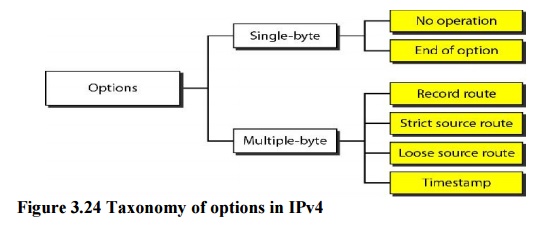
No Operation
A no-operation option is a 1-byte option
used as filler between options.
End of Option
An
end-of-option option is a 1-byte option used for padding at the end of the
option field. It, however, can only be used as the last option.
Record Route
A record
route option is used to record the Internet routers that handle the datagram.
It can list up to nine router addresses. It can be used for debugging and
management purposes.
Strict Source Route
A strict
source route option is used by the source to predetermine a route for the
datagram as it travels through the Internet. Dictation of a route by the source
can be useful for several purposes. The sender can choose a route with a
specific type of service, such as minimum delay or maximum throughput. Alternatively,
it may choose a route that is safer or more reliable for the sender's purpose.
Loose Source Route
A loose
source route option is similar to the strict source route, but it is less
rigid. Each router in the list must be visited, but the datagram can visit
other routers as well.
Timestamp
A
timestamp option is used to record the time of datagram processing by a router.
The time is expressed in milliseconds from midnight, Universal time or
Greenwich mean time. Knowing the time a datagram is processed can help users
and managers track the behavior of the routers in the Internet.
Related Topics