Chapter: Cryptography and Network Security Principles and Practice : Mutual Trust : User Authentication
Remote User-Authentication Using Symmetric Encryption
REMOTE
USER-AUTHENTICATION USING SYMMETRIC ENCRYPTION
Mutual Authentication
As was discussed in Chapter 14, a two-level hierarchy of symmetric encryption keys can
be used to provide confidentiality for communication in a distributed environment. In general, this strategy
involves the use of a trusted key distribution center (KDC). Each party in the network
shares a secret
key, known as a master key, with the KDC. The KDC is responsible for generating keys to be used for a
short time over a connection between two parties,
known as session
keys, and for distributing those keys using the master
keys to protect the distribution. This approach is quite common. As an example, we look at the Kerberos system in Section 15.3. The discussion in
this subsection is relevant to an understanding of the Kerberos mechanisms.
Figure 14.3 illustrates a proposal initially
put forth by Needham and Schroeder
for secret
key distribution using
a KDC that, as was mentioned in Chapter 14,
includes authentication features. The protocol can be summarized as follows.
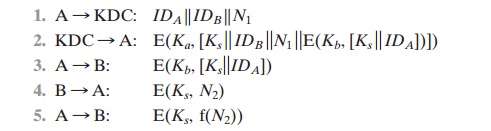
Secret keys Ka and Kb are
shared between A and the KDC and
B and the KDC,
respectively. The purpose of the protocol is to
distribute securely a session key Ks to A and B. A
securely acquires a new session key in step 2. The message in step 3 can be decrypted, and hence understood,
only by B. Step 4 reflects B’s
knowledge of Ks, and step 5 assures B of A’s knowledge of Ks and assures B that this is a fresh mes- sage because of
the use of the nonce N2. Recall from our
discussion in Chapter 14 that the purpose of steps 4 and 5 is to prevent a
certain type of replay attack. In par- ticular, if an opponent is able to
capture the message in step 3 and replay it,
this might in some fashion disrupt operations at B.
Despite the handshake of steps 4 and 5, the protocol
is still vulnerable to a form of replay attack. Suppose that an opponent,
X, has been able to compromise an old ses-
sion key. Admittedly, this is a much more unlikely
occurrence than that an opponent has simply observed and recorded
step 3. Nevertheless, it is a potential
security risk. X can
impersonate A and trick B into using the old key by simply
replaying step 3. Unless B remembers
indefinitely all previous session
keys used with A, B will be unable to determine that this is a replay. If X can intercept
the handshake message
in step 4, then it can impersonate A’s response in step 5. From this point on, X can send bogus mes- sages to B that appear to B to come from A using an authenticated session key.
Denning
proposes to overcome this
weakness by a mod-
ification to the Needham/Schroeder protocol that includes the addition of a
time- stamp to steps 2 and 3. Her proposal assumes that the master keys, Ka and Kb, are secure, and it consists of the following steps.
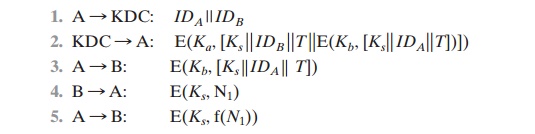
T is a timestamp that assures A and B that
the session key has only just been
generated. Thus, both A and B know that the key distribution is a fresh exchange. A and
B can verify timeliness by checking that
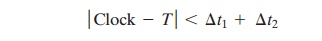
where Δt1 is the estimated normal discrepancy between the KDC’s clock
and the local clock (at A or B) and Δt2 is the expected
network delay time. Each node can set its clock against
some standard reference
source. Because
the timestamp T is
encrypted using the secure
master keys, an opponent, even with knowledge of an old session key, cannot succeed
because a replay
of step 3 will be detected by B as untimely.
A final point: Steps 4 and 5 were not
included in the original presentation [DENN81] but were added later [DENN82].
These steps confirm
the receipt of the
session key at B.
The Denning
protocol seems to provide
an increased degree of security
compared to the Needham/Schroeder protocol. However, a new concern is raised: namely,
that this new scheme requires reliance on clocks that are synchro- nized
throughout the network. [GONG92]
points out a risk involved. The
risk
is
based on the fact that the distributed
clocks can become unsynchronized as a result of sabotage on or faults in the
clocks or the synchronization mechanism.2 The problem occurs when a sender’s clock is ahead of the
intended recipient’s clock. In this case, an opponent can intercept a message
from the sender and
replay it later when the timestamp in the
message becomes current at the recipi- ent’s site. This replay could cause
unexpected results. Gong refers to such attacks as suppress-replay attacks.
One way to counter suppress-replay attacks is to enforce the requirement that parties regularly check their clocks against
the KDC’s clock.
The other alternative,
which avoids the need for clock synchronization, is to rely on handshaking protocols using nonces. This latter alternative is not
vulnerable to a suppress-replay attack, because the nonces the recipient will
choose in the future are unpredictable to the sender. The Needham/Schroeder protocol relies on nonces only but, as we have seen,
has other vulnerabilities.
In [KEHN92], an attempt is made to respond to the concerns
about suppress- replay attacks
and at the same time fix the problems in the Needham/Schroeder protocol.
Subsequently, an inconsistency in this latter protocol was noted and an
improved strategy was presented in . The protocol is
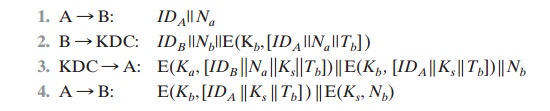
Let us follow this exchange step by step.
1.
A initiates the
authentication exchange by generating
a nonce, Na, and sending that plus its identifier to B in plaintext. This nonce will be returned
to A in an encrypted message that includes the session key, assuring
A of its timeliness.
B alerts
the KDC that a session
key is needed. Its message
to the KDC includes its identifier and a nonce, Nb.
This nonce will be returned to
B in an encrypted message that includes the
session key, assuring B of its
timeliness. B’s message to the KDC also includes
a block encrypted
with the secret
key shared by B and the KDC. This block is used to instruct
the KDC to issue credentials to A; the block specifies the intended
recipient of the credentials, a suggested
expiration time for the credentials, and the nonce received from A.
2.
The KDC passes on to A B’s nonce and a block encrypted with the secret
key that B shares with the KDC. The block serves as a “ticket”
that can be used by A
for subsequent authentications, as will be seen. The KDC also sends to A a block
encrypted with the secret key shared
by A and the KDC. This block verifies that B has received
A’s initial message (IDB) and that this is a timely
message and not a replay
(Na), and it provides A with a session key (Ks) and the time limit on its use
(Tb).
3.
A transmits the
ticket to B, together with the B’s
nonce, the latter encrypted with the session key.
The ticket provides B with
the secret key that is used to
decrypt E(Ks,
Nb) to recover the
nonce. The fact that B’s nonce is
encrypted with the session
key authenticates that the message
came from A and is not a replay.
This protocol provides an effective, secure means for A
and B to establish a session with a secure session
key. Furthermore, the protocol
leaves A in possession
of a key that can be used for subsequent authentication to B, avoiding the need to contact the
authentication server repeatedly. Suppose that A and B establish a ses- sion
using the aforementioned protocol and then
conclude that session. Subsequently, but within the time limit
established by the protocol, A desires a new
session with B. The following protocol ensues:
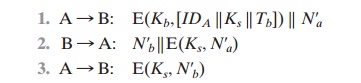
When B receives the message in step 1, it
verifies that the ticket has not expired. The newly
generated nonces N¿a and
N¿b assure each
party that there is no replay
attack. In all the foregoing, the time specified in Tb is a time relative
to B’s clock.
Thus, this timestamp does not require synchronized clocks, because B checks only self-generated timestamps.
One-Way Authentication
Using symmetric encryption, the decentralized key distribution scenario
illustrated in Figure 14.5 is impractical. This scheme requires the
sender to issue a request to the
intended recipient, await a response that includes a session key, and only then send the message.
With some refinement, the KDC strategy
illustrated in Figure
14.3 is a candi-
date for encrypted electronic mail. Because we wish to avoid requiring that the recipient (B) be on line at the same
time as the sender (A), steps 4 and 5 must be eliminated. For a message with content M, the sequence is as follows:
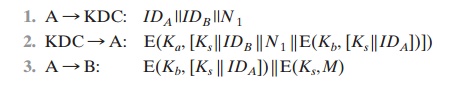
This approach guarantees that only the
intended recipient of a message will be able to read it. It also provides a
level of authentication that the sender is A. As specified, the protocol does
not protect against replays. Some measure of defense could be provided by
including a timestamp with the message. However, because of the potential
delays in the e-mail process, such timestamps may have limited usefulness.
Related Topics