Chapter: Fundamentals of Database Systems : Transaction Processing, Concurrency Control, and Recovery : Concurrency Control Techniques
Multiversion Concurrency Control Techniques
Multiversion Concurrency Control Techniques
Other protocols for concurrency control keep the old values of a data
item when the item is updated. These are known as multiversion concurrency control, because several versions (values)
of an item are maintained. When a transaction requires access to an item, an appropriate version is chosen to
maintain the serializability of the currently executing schedule, if possible.
The idea is that some read operations that would be rejected in other
techniques can still be accepted by reading an older version of the item
to maintain serializability. When a transaction writes an item, it writes a new version and the old version(s) of the item are retained. Some
multiver-sion concurrency control algorithms use the concept of view
serializability rather than conflict serializability.
An obvious drawback of multiversion techniques is that more storage is
needed to maintain multiple versions of the database items. However, older
versions may have to be maintained anyway—for example, for recovery purposes.
In addition, some database applications require older versions to be kept to
maintain a history of the evolution of data item values. The extreme case is a temporal database (see Secton 26.2),
which keeps track of all changes and the times at which they occurred. In such
cases, there is no additional storage penalty for multiversion techniques,
since older versions are already maintained.
Several multiversion concurrency control schemes have been proposed. We
discuss two schemes here, one based on timestamp ordering and the other based
on 2PL. In addition, the validation concurrency control method (see Section
22.4) also maintains multiple versions.
1. Multiversion
Technique Based on Timestamp Ordering
In this
method, several versions X1,
X2, ..., Xk of each data item X are maintained. For each version, the value of version Xi and the following two
timestamps are kept:
read_TS(Xi). The read timestamp of Xi is the largest of all the timestamps
of transactions that have
successfully read version Xi.
write_TS(Xi). The write timestamp of Xi is the timestamp of the transaction
that wrote the value of version Xi.
Whenever
a transaction T is allowed to execute
a write_item(X) operation, a new version Xk+1
of item X is created, with both the write_TS(Xk+1) and the read_TS(Xk+1)
set to TS(T). Correspondingly, when a transaction T is allowed to read the value of version Xi, the value of read_TS(Xi) is set to the larger of
the current read_TS(Xi) and TS(T).
To ensure
serializability, the following rules are used:
If transaction T
issues a write_item(X) operation, and version i of X
has the highest write_TS(Xi) of all versions of X that is also less than or equal to TS(T), and read_TS(Xi) > TS(T), then abort and roll back transaction T; otherwise, create a new version Xj of X with read_TS(Xj) = write_TS(Xj) = TS(T).
If transaction T
issues a read_item(X) operation, find the version i of X
that has the highest write_TS(Xi) of all versions of X that is also less than or equal to TS(T); then return the value of
Xi to transaction T, and
set the value of read_TS(Xi) to the larger of
TS(T) and the current read_TS(Xi).
As we can see in case 2, a read_item(X) is always successful, since it finds the appropriate version Xi to read based on the write_TS of the various existing versions of X. In case 1, however, transaction T may be aborted and rolled back. This happens if T attempts to write a version of X that should have been read by another transaction T whose timestamp is read_TS(Xi); however, T has already read version Xi, which was written by the transaction with timestamp equal to write_TS(Xi). If this conflict occurs, T is rolled back; otherwise, a new version of X, written by transaction T, is created. Notice that if T is rolled back, cascading rollback may occur. Hence, to ensure recoverability, a transaction T should not be allowed to commit until after all the transactions that have written some version that T has read have committed.
2. Multiversion
Two-Phase Locking Using Certify Locks
In this multiple-mode locking scheme, there are three locking modes for an item: read, write, and certify, instead of just the two modes
(read, write) discussed previously. Hence, the state of LOCK(X) for an item X can be one of read-locked,
write-locked, certify-locked, or unlocked. In the standard locking scheme, with
only read and write locks (see Section 22.1.1), a write lock is an exclusive
lock. We can describe the relationship between read and write locks in the
standard scheme by means of the lock
compatibility table shown in Figure 22.6(a). An entry of Yes means that if a transaction T holds the type of lock specified in
the column header
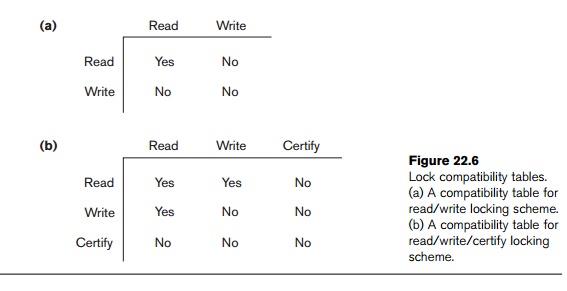
on item X and if transaction T requests the type of lock specified in
the row header on the same item X,
then T can obtain the lock because
the locking modes are compatible. On the other hand, an entry of No in the table indicates that the locks
are not compatible, so T must wait
until T releases the lock.
In the standard locking scheme, once a transaction obtains a write lock
on an item, no other transactions can access that item. The idea behind
multiversion 2PL is to allow other transactions T to read an item X while
a single transaction T holds a write
lock on X. This is accomplished by
allowing two versions for each item X; one version must always have been
written by some committed transaction. The second version X is created when a transaction T
acquires a write lock on the item. Other transactions can continue to read the committed version of X while T holds the write lock. Transaction T can write the value of X
as needed, without affecting the value of the committed version X. However, once T is ready to commit, it must obtain a certify lock on all items that it currently holds write locks on
before it can commit. The certify
lock is not compatible with read locks, so the transaction may have to delay
its commit until all its write-locked items are released by any reading
transactions in order to obtain the certify locks. Once the certify
locks—which are exclusive locks—are acquired, the committed version X of the data item is set to the value
of version X , version X is discarded, and the certify locks
are then released. The lock compatibility table for this scheme is shown in
Figure 22.6(b).
In this multiversion 2PL scheme, reads can proceed concurrently with a
single write operation—an arrangement not permitted under the standard 2PL
schemes. The cost is that a transaction may have to delay its commit until it
obtains exclusive certify locks on all
the items it has updated. It can be shown that this scheme avoids
cascading aborts, since transactions are only allowed to read the version X that was written by a committed
transaction. However, deadlocks may occur if upgrading of a read lock to a
write lock is allowed, and these must be handled by variations of the
techniques discussed in Section 22.1.3.
Related Topics