Chapter: Security in Computing : Security in Networks
Impersonation
Impersonation
In many instances, there is
an easier way than wiretapping for obtaining information on a network:
Impersonate another person or process. Why risk tapping a line, or why bother
extracting one communication out of many, if you can obtain the same data
directly?
Impersonation is a more
significant threat in a wide area network than in a local one. Local
individuals often have better ways to obtain access as another user; they can,
for example, simply sit at an unattended workstation. Still, impersonation
attacks should not be ignored even on local area networks, because local area
networks are sometimes attached to wider area networks without anyone's first
thinking through the security implications.
In an impersonation, an
attacker has several choices:
Guess the identity and
authentication details of the target.
Pick up the identity and
authentication details of the target from a previous communication or from
wiretapping.
Circumvent or disable the authentication
mechanism at the target computer.
Use a target that will not be
authenticated.
Use a target whose
authentication data are known. Let us look at each choice.
Authentication Foiled by Guessing
Chapter 4 reported the
results of several studies showing that many users choose easy-to-guess passwords.
In Chapter 3, we saw that the Internet worm of 1988 capitalized
on exactly that flaw. Morris's worm tried to impersonate each user on a target
machine by trying, in order, a handful of variations of the user name, a list
of about 250 common passwords and, finally, the words in a dictionary. Sadly,
many users' accounts are still open to these easy attacks.
A second source of password
guesses is default passwords. Many systems are initially configured with
default accounts having GUEST or ADMIN as login IDs; accompanying these IDs are
well-known passwords such as "guest" or "null" or
"password" to enable the administrator to set up the system.
Administrators often forget to delete or disable these accounts, or at least to
change the passwords.
In a trustworthy environment,
such as an office LAN, a password may simply be a signal that the user does not
want others to use the workstation or account. Sometimes the password-protected
workstation contains sensitive data, such as employee salaries or information
about new products. Users may think that the password is enough to keep out a
curious colleague; they see no reason to protect against concerted attacks.
However, if that trustworthy environment is connected to an untrustworthy
wider-area network, all users with simple passwords become easy targets.
Indeed, some systems are not originally connected to a wider network, so their
users begin in a less exposed situation that clearly changes when the
connection occurs.
Dead accounts offer a final
source of guessable passwords. To see how, suppose Professor Romine, a faculty
member, takes leave for a year to teach at another university. The existing
account may reasonably be kept on hold, awaiting the professor's return. But an
attacker, reading a university newspaper online, finds out that the user is
away. Now the attacker uses social engineering on the system administration
("Hello, this is Professor Romine calling from my temporary office at
State University. I haven't used my account for quite a while, but now I need
something from it urgently. I have forgotten the password. Can you please reset
it to ICECREAM? No? Well, send me a new password by email to my account
r1@stateuniv.edu.") Alternatively, the attacker can try several passwords
until the password guessing limit is exceeded. The system then locks the
account administratively, and the attacker uses a social engineering attack. In
all these ways the attacker may succeed in resetting or discovering a password.
Authentication Thwarted by Eavesdropping or Wiretapping
Because of the rise in
distributed and client-server computing, some users have access privileges on
several connected machines. To protect against arbitrary outsiders using these
accesses, authentication is required between hosts. This access can involve the
user directly, or it can be done automatically on behalf of the user through a
host-to-host authentication protocol. In either case, the account and
authentication details of the subject are passed to the destination host. When
these details are passed on the network, they are exposed to anyone observing
the communication on the network. These same authentication details can be
reused by an impersonator until they are changed.
Because transmitting a
password in the clear is a significant vulnerability, protocols have been
developed so that the password itself never leaves a user's workstation. But,
as we have seen in several other places, the details are important.
Microsoft LAN Manager was an early method for
implementing networks. It had a password exchange mechanism in which the
password itself was never transmitted in the clear; instead only a
cryptographic hash of it was transmitted. A password could consist of up to 14 characters.
It could include upper- and lowercase letters, digits, and special characters,
for 67 possibilities in any one position, and 6714 possibilities for
a whole 14 -character passwordquite a respectable work factor. However, those
14 characters were not diffused across the entire hash; they were sent in
separate substrings, representing characters 17 and 814. A 7-character or
shorter password had all nulls in the second substring and was instantly
recognizable. An 8-character password had 1 character and 6 nulls in the second
substring, so 67 guesses would find the one character. Even in the best case, a
14- character password, the work factor fell from 6714 to 677
+ 67 7 = 2 * 677. These work factors differ by a factor
of approximately 10 billion. (See [MUD97]
for details.) LAN Manager authentication was preserved in many later systems
(including Windows NT) as an option to support backward compatibility with
systems such as Windows 95/98. This lesson is a good example of why security
and cryptography are very precise and must be monitored by experts from concept
through design and implementation.
Authentication Foiled by Avoidance
Obviously, authentication is
effective only when it works. A weak or flawed authentication allows access to
any system or person who can circumvent the authentication.
In a classic operating system
flaw, the buffer for typed characters in a password was of fixed size, counting
all characters typed, including backspaces for correction. If a user typed more
characters than the buffer would hold, the overflow caused the operating system
to bypass password comparison and act as if a correct authentication had been
supplied. These flaws or weaknesses can be exploited by anyone seeking access.
Many network hosts,
especially those that connect to wide area networks, run variants of Unix
System V or BSD Unix. In a local environment, many users are not aware of which
networked operating system is in use; still fewer would know of, be capable of,
or be interested in exploiting flaws. However, some hackers regularly scan wide
area networks for hosts running weak or flawed operating systems. Thus,
connection to a wide area network, especially the Internet, exposes these flaws
to a wide audience intent on exploiting them.
Nonexistent Authentication
If two computers are used by
the same users to store data and run processes and if each has authenticated
its users on first access, you might assume that computer-to-computer or local
user-to-remote process authentication is unnecessary. These two computers and
their users are a trustworthy environment in which the added complexity of
repeated authentication seems excessive.
However, this assumption is
not valid. To see why, consider the Unix operating system. In Unix, the file
.rhosts lists trusted hosts and .rlogin lists trusted users who are allowed
access without authentication. The files are intended to support
computer-to-computer
connection by users who have
already been authenticated at their primary hosts. These "trusted
hosts" can also be exploited by outsiders who obtain access to one system
through an authentication weakness (such as a guessed password) and then
transfer to another system that accepts the authenticity of a user who comes
from a system on its trusted list.
An attacker may also realize
that a system has some identities requiring no authentication. Some systems
have "guest" or "anonymous" accounts to allow outsiders to
access things the systems want to release to anyone. For example, a bank might
post a current listing of foreign currency rates, a library with an online
catalog might make that catalog available for anyone to search, or a company
might allow access to some of its reports. A user can log in as
"guest" and retrieve publicly available items. Typically, no password
is required, or the user is shown a message requesting that the user type
"GUEST" (or your name, which really means any string that looks like
a name) when asked for a password. Each of these accounts allows access to
unauthenticated users.
Well-Known Authentication
Authentication data should be
unique and difficult to guess. But unfortunately, the convenience of one
well-known authentication scheme sometimes usurps the protection. For example,
one computer manufacturer planned to use the same password to allow its remote
maintenance personnel to access any of its computers belonging to any of its
customers throughout the world. Fortunately, security experts pointed out the
potential danger before that idea was put in place.
The system network management
protocol (SNMP) is widely used for remote management of network devices, such
as routers and switches, that support no ordinary users. SNMP uses a
"community string," essentially a password for the community of
devices that can interact with one another. But network devices are designed
especially for quick installation with minimal configuration, and many network
administrators do not change the default community string installed on a router
or switch. This laxity makes these devices on the network perimeter open to
many SNMP attacks.
Some vendors still ship
computers with one system administration account installed, having a default
password. Or the systems come with a demonstration or test account, with no
required password. Some administrators fail to change the passwords or delete
these accounts.
Trusted Authentication
Finally, authentication can
become a problem when identification is delegated to other trusted sources. For
instance, a file may indicate who can be trusted on a particular host. Or the
authentication mechanism for one system can "vouch for" a user. We
noted earlier how the Unix .rhosts, .rlogin, and /etc/hosts/equiv files
indicate hosts or users that are trusted on other hosts. While these features
are useful to users who have accounts on multiple machines or for network
management, maintenance, and operation, they must be used very carefully. Each
of them represents a potential hole through which a remote useror a remote
attackercan achieve access.
Spoofing
Guessing or otherwise
obtaining the network authentication credentials of an entity (a user, an
account, a process, a node, a device) permits an attacker to create a full
communication under the entity's identity. Impersonation falsely represents a
valid entity in a communication. Closely related is spoofing, when an attacker falsely carries on one end of a
networked interchange. Examples of spoofing are masquerading, session
hijacking, and man-in-the-middle attacks.
Masquerade
In a masquerade one host pretends to be another. A common example is URL
confusion. Domain names can easily be confused, or someone can easily mistype
certain names. Thus xyz.com, xyz.org, and xyz.net might be three different
organizations, or one bona fide organization (for example, xyz.com) and two
masquerade attempts from someone who registered the similar domain names. Names
with or without hyphens (coca-cola.com versus cocacola.com) and easily mistyped
names (l0pht.com versus lopht.com, or citibank.com versus citybank.com) are
candidates for masquerading.
From the attacker's point of
view, the fun in masquerading comes before the mask is removed. For example,
suppose you want to attack a real bank, First Blue Bank of Chicago. The actual
bank has the domain name BlueBank.com, so you register the domain name
Blue-Bank.com. Next, you put up a web page at Blue-Bank.com, perhaps using the
real Blue Bank logo that you downloaded to make your site look as much as
possible like that of the Chicago bank. Finally, you ask people to log in with
their name, account number, and password or PIN. (This redirection can occur in
many ways. For example, you can pay for a banner ad that links to your site
instead of the real bank's, or you can send e-mail to Chicago residents and
invite them to visit your site.) After collecting personal data from several
bank users, you can drop the connection, pass the connection on to the real
Blue Bank, or continue to collect more information. You may even be able to
transfer this connection smoothly to an authenticated access to the real Blue
Bank so that the user never realizes the deviation. (First Blue Bank would
probably win a suit to take ownership of the Blue-Bank.com domain.)
A variation of this attack is
called phishing. You send an e-mail
message, perhaps with the real logo of Blue Bank, and an enticement to click on
a link, supposedly to take the victim to the Blue Bank web site. The enticement
might be that your victim's account has been suspended or that you offer your
victim some money for answering a survey (and need the account number and PIN
to be able to credit the money), or some other legitimate-sounding explanation.
The link might be to your domain Blue-Bank.com, the link might say click here
to access your account (where the click here link connects to your fraudulent
site), or you might use some other trick with the URL to fool your victim, like
www.redirect.com/bluebank.com.
In another version of a
masquerade, the attacker exploits a flaw in the victim's web server and is able
to overwrite the victim's web pages. Although there is some public humiliation
at having one's site replaced, perhaps with obscenities or strong messages
opposing the nature of the site (for example, a plea for vegetarianism on a
slaughterhouse web site), most people would not be fooled by a site displaying
a message absolutely contrary to its aims. However, a clever attacker can be
more subtle. Instead of differentiating from the real site, the attacker can
try to build a false site that resembles the real one, perhaps to obtain
sensitive information (names, authentication numbers, credit card numbers) or
to induce the user to enter into a real transaction. For example, if one
bookseller's site, call it Books-R-Us, were overtaken subtly by another, called
Books Depot, the orders may actually be processed, filled, and billed to the
naïve users by Books Depot. Test your ability to distinguish phishing sites
from real ones at http://survey.mailfrontier.com/survey/quiztest.html.
Phishing is becoming a
serious problem, according to a trends report from the Anti-Phishing Working
Group [APW05]. This group received over
12,000 complaints each month from March 2005 to March 2006, with the number
peaking above 18,000 for March 2006.
Session Hijacking
Session hijacking is intercepting and carrying on a session begun
by another entity. Suppose two entities have entered into a session but then a third entity intercepts the
traffic and carries on the session in the name of the other. Our example of
Books-R-Us could be an instance of this technique. If Books Depot used a
wiretap to intercept packets between you and Books-R-Us, Books Depot could
simply monitor the information flow, letting Books-R-Us do the hard part of
displaying titles for sale and convincing the user to buy. Then, when the user
has completed the order, Books Depot intercepts the "I'm ready to check
out" packet, and finishes the order with the user, obtaining shipping
address, credit card details, and so forth. To Books-R-Us, the transaction
would look like any other incomplete transaction: The user was browsing but for
some reason decided to go elsewhere before purchasing. We would say that Books
Depot had hijacked the session.
A different type of example
involves an interactive session, for example, using Telnet. If a system
administrator logs in remotely to a privileged account, a session hijack
utility could intrude in the communication and pass commands as if they came
from the administrator.
Man-in-the-Middle Attack
Our hijacking example
requires a third party involved in a session between two entities. A man-in-the -middle attack is a similar
form of attack, in which one entity intrudes between two others. We studied one
form of this attack in Chapter 3. The
difference between man-in-the-middle and hijacking is that a man-in-the-middle
usually participates from the start of the session, whereas a session hijacking
occurs after a session has been established. The difference is largely semantic
and not too significant.
Man-in-the-middle attacks are frequently
described in protocols. To see how an attack works, suppose you want to exchange
encrypted information with your friend. You contact the key server and ask for
a secret key with which to communicate with your friend. The key server
responds by sending a key to you and your friend. One man-in-the-middle attack
assumes someone can see and enter into all parts of this protocol. A malicious
middleman intercepts the response key and can then eavesdrop on, or even
decrypt, modify, and reencrypt any subsequent communications between you and
your friend. This attack is depicted in Figure 7-15.
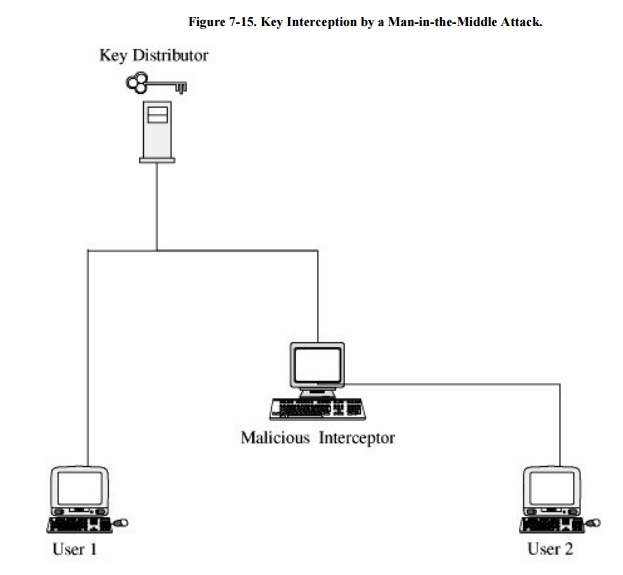
This attack would be changed
with public keys, because the man-in-the-middle would not have the private key
to be able to decrypt messages encrypted under your friend's public key. The
man-in-the-middle attack now becomes more of the three-way interchange its name
implies. The man-in-the-middle intercepts your request to the key server and
instead asks for your friend's public key. The man-in-the-middle passes to you
his own public key, not your friend's. You encrypt using the public key you
received (from the man-in-the-middle); the man-in-the-middle intercepts and
decrypts, reads, and reencrypts, using your friend's public key; and your
friend receives. In this way, the man-in-the-middle reads the messages and
neither you nor your friend is aware of the interception. A slight variation of
this attack works for secret key distribution under a public key.
Related Topics