Chapter: Security in Computing : Security in Networks
Honeypots, Alarms and Alerts - Security in Networks
Alarms and Alerts
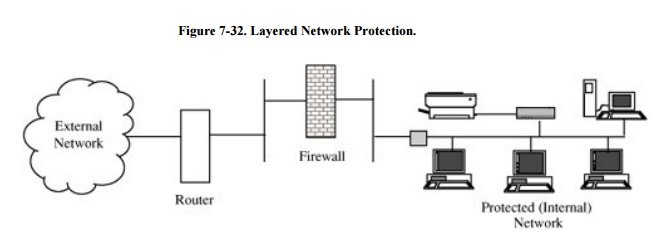
The logical view of network
protection looks like Figure 7-32, in
which both a router and a firewall provide layers of protection for the
internal network. Now let us add one more layer to this defense.
An intrusion detection system
is a device that is placed inside a protected network to monitor what occurs
within the network. If an attacker passes through the router and passes through
the firewall, an intrusion detection system offers the opportunity to detect
the attack at the beginning, in progress, or after it has occurred. Intrusion
detection systems activate an alarm, which can take defensive action. We study
intrusion detection systems in more detail later in this chapter.
Honeypots
How do you catch a mouse? You
set a trap with bait (food the mouse finds attractive) and catch the mouse after it is lured into the trap. You
can catch a computer attacker the same way.
In a very interesting book, Cliff Stoll [STO89] details the story of attracting and
monitoring the actions of an attacker. Cheswick [CHE90,
CHE02] and
Bellovin [BEL92c] tell a similar story. These two cases describe the use of a honeypot: a computer
system open to attackers.
You put up a honeypot for several reasons:
· to watch what attackers do, in order to learn
about new attacks (so that you can strengthen your defenses against these new
attacks)
· to lure an attacker to a place in which you may
be able to learn enough to identify and stop the attacker
· to provide an attractive but diversionary
playground, hoping that the attacker will leave your real system alone
A honeypot has no special features. It is just
a computer system or a network segment, loaded with servers and devices and data.
It may be protected with a firewall, although you want the attackers to have
some access. There may be some monitoring capability, done carefully so that
the monitoring is not evident to the attacker.
The two difficult features of a honeypot are
putting up a believable, attractive false environment and confining and monitoring the
attacker surreptitiously. Spitzner [SPI02,
SPI03a] has done extensive work
developing and analyzing honeypots. He thinks like the attacker, figuring what
the attacker will want to see in an invaded computer, but as McCarty [MCC03] points out, it is always a race between
attacker and defender. Spitzner also tries to move much of his data off the
target platform so that the attacker will not be aware of the analysis and
certainly not be able to modify or erase the data gathered. Raynal [RAY04a. RAY04b]
discusses how to analyze the data collected.
Related Topics