Chapter: Information Security : Logical Design
Design of Security Architecture
VISA INTERNATIONAL SECURITY MODEL
ü It
promotes strong security measures in its business associates and has
established guidelines for the security of its information systems.
ü It has
developed two important documents
\endash
Security Assessment Process
\endash
Agreed Upon Procedures.
ü Both
documents provide specific instructions on the use of the VISA Cardholder
Information Security Program.
ü The
Security Assessment Process document is a series of recommendations for the
detailed examination of an organization’s systems with the eventual goal of integration
into the VISA systems.
ü The
Agreed upon Procedures document outlines the policies and technologies required
for security systems that carry the sensitive card holder information to and
from VISA systems.
ü Using the
two documents, a security team can develop a sound strategy for the design of
good security architecture.
ü The only
downside to this approach is the specific focus on systems that can or do
integrate with VISA’s systems with the explicit purpose of carrying the
aforementioned cardholder information.
Baselining & Best Business Practices
\endash
Baselining
and best practices are solid methods for collecting security practices, but
provide less detail than a complete methodology
\endash
Possible
to gain information by baselining and using best practices and thus work
backwards to an effective design
\endash
The
Federal Agency Security Practices (FASP) site (fasp.nist.gov) designed to
provide best practices for public agencies and adapted easily to private
institutions.
\endash
The
documents found in this site include specific examples of key policies and
planning documents, implementation strategies for key technologies, and
position descriptions for key security personnel.
\endash
Of
particular value is the section on program management, which includes the
following:
A summary guide: public law, executive orders, and
policy documents
Position description for computer system security
officer.
Position description for information security
officer
Position description for computer specialist.
Sample of an information technology(IT) security
staffing plan for a large service application(LSA)
Sample of an information technology(IT) security
program policy
Security handbook and standard operating
procedures.
Telecommuting and mobile computer security policy.
\endash
DESIGN OF
SECURITY ARCHITECTURE
\endash
Hybrid
Framework for a Blueprint of an Information Security System
The
framework of security includes philosophical components of the Human Firewall
Project, which maintain that people, not technology, are the primary defenders
of information assets in an information security program, and are uniquely
responsible for their protection.
The
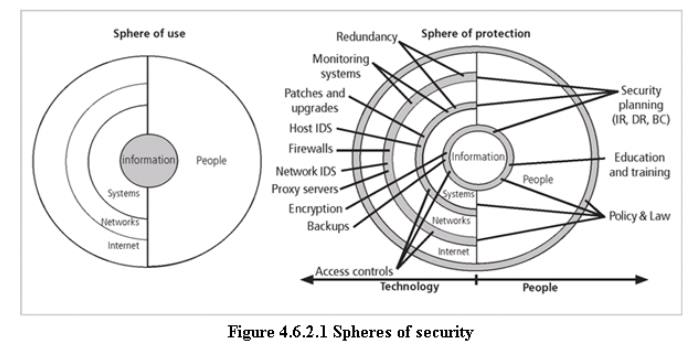
spheres of security are the foundation of the security framework.
The
sphere of use, at the left in fig, explains the ways in which people access information;
for example, people read hard copies of documents and can also access
information through systems.
The
sphere of protection at the right illustrates that between each layer of the
sphere of use there must exist a layer of protection to prevent access to the
inner layer from the outer layer.
Each
shaded band is a layer of protection and control.
\endash
Sphere of
Protection
The
“sphere of protection” overlays each of the levels of the “sphere of use” with
a layer of security, protecting that layer from direct or indirect use through
the next layer
The
people must become a layer of security, a human
firewall that protects the information from unauthorized access and use
Information
security is therefore designed and implemented in three layers
–
policies
–
people
(education, training, and awareness programs)
–
technology
4.6.7 As
illustrated in the sphere of protection, a variety of controls can be used to
protect the information.
4.6.8 The items
of control shown in the figure are not intended to be comprehensive but rather
illustrate individual safeguards that can protect the various systems that are
located closer to the center of the sphere.
4.6.9 However,
because people can directly access each ring as well as the information at the
core of the model, the side of the sphere of protection that attempt to control
access by relying on people requires a different approach to security than the
side that uses technology.
3 Level of Control
Management Controls
ü Risk
Management
ü Review of
Security Controls
ü Life
Cycle Maintenance
ü Authorization
of Processing (Certification and Accreditation)
ü System
Security Plan
Operational Controls
ü Personnel
Security
ü Physical
Security
ü Production,
Input/Output Controls
ü Contingency
Planning
ü Hardware
and Systems Software
ü Data
Integrity
ü Documentation
ü Security
Awareness, Training, and Education
ü Incident
Response Capability
Technical Controls
ü Identification
and Authentication
ü Logical
Access Controls
ü Audit
Trails
Management controls
ü It address
the design and implementation of the security planning process and security
program management.
ü They also
address risk management and security control reviews. They further describe the
necessity and scope of legal compliance and the maintenance of the entire
security life cycle.
Operational controls
ü It deal
with the operational functionality of security in the organization. They
include management functions and lower level planning, such as disaster
recovery and incident response planning.
ü They also
address personnel security, physical security, and the protection of production
inputs and outputs.
ü They
guide the development of education, training and awareness programs for users,
administrators, and management. Finally, they address hardware and software
systems maintenance and the integrity of data.
Technical controls
1. It
address the tactical and technical issues related to designing and implementing
security in the organization, as well as issues related to examining and
selecting the technologies appropriate to protecting information.
2. They
address the specifics of technology selection and the acquisition of certain
technical components. They also include logical access controls, such as
identification, authentication, authorization, and accountability.
3. They
cover cryptography to protect information in storage and transit. Finally, they
include the classification of assets and users, to facilitate the authorization
levels needed.
Using the
three sets of controls, the organization should be able to specify controls to
cover the entire spectrum of safeguards, from strategic to tactical, and from
managerial to technical.
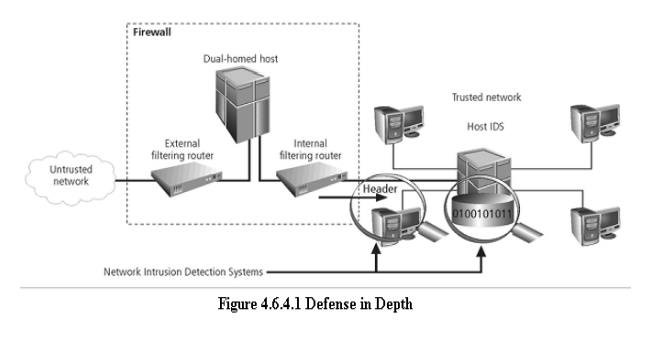
5.
Defense
in Depth
One of
the basic foundations of security architectures is the implementation of
security in layers. This layered approach is called defense in depth.
Defense
in depth requires that the organization establish sufficient security controls
and safeguards, so that an intruder faces multiple layers of controls.
These
layers of control can be organized into policy, training and education and
technology as per the NSTISSC model.
While
policy itself may not prevent attacks, they coupled with other layers and deter
attacks.
Training
and Education are similar.
Technology
is also implemented in layers, with detection equipment, all operating behind
access control mechanisms.
Implementing
multiple types of technology and thereby preventing the failure of one system
from compromising the security of the information is referred to as redundancy.
Redundancy
can be implemented at a number of points throughout the security architecture,
such as firewalls, proxy servers, and access controls. The figure shows the use
of firewalls and intrusion detection systems(IDS) that use both packet-level
rules and data content.
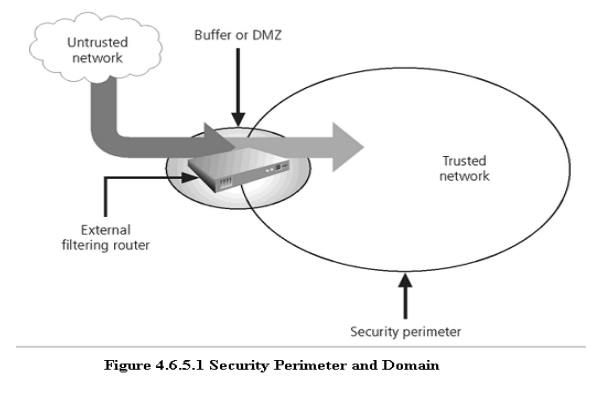
Security Perimeter
ü A
Security Perimeter is the first level of security that protects all internal
systems from outside threats.
ü Unfortunately,
the perimeter does not protect against internal attacks from employee threats,
or on-site physical threats.
ü Security
perimeters can effectively be implemented as multiple technologies that
segregate the protected information from those who would attack it.
ü Within
security perimeters the organization can establish security domains, or areas
of trust within which users can freely communicate.
ü The
presence and nature of the security perimeter is an essential element of the
overall security framework, and the details of implementing the perimeter make
up a great deal of the particulars of the completed security blueprint.
ü The key
components used for planning the perimeter are presented in the following
sections on firewalls, DMZs, proxy servers, and intrusion detection systems.
ü
Key
Technology Components
Other key
technology components
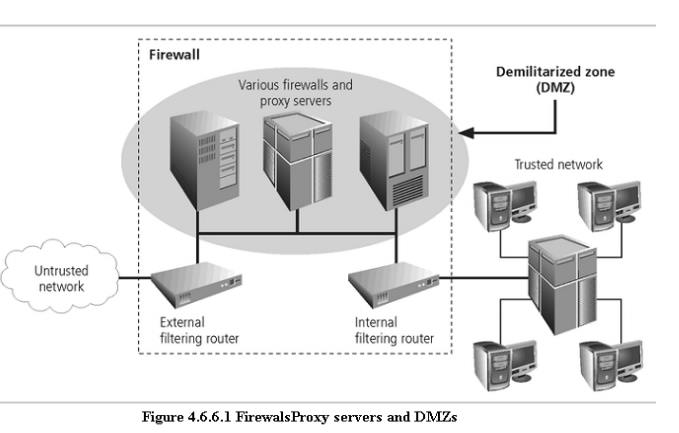
– A firewall is a device that selectively
discriminates against information flowing
into or
out of the organization.
– Firewalls
are usually placed on the security perimeter, just behind or as part of a gateway
router.
– Firewalls
can be packet filtering, stateful packet filtering, proxy, or application level.
– A
Firewall can be a single device or a
firewall subnet, which
consists of multiple firewalls
creating a buffer between the outside and inside networks.
– The DMZ (demilitarized zone) is a
no-man’s land, between the inside and outside networks, where some organizations place Web
servers
– These
servers provide access to organizational web pages, without allowing Web requests to enter the interior
networks.
– Proxy server- An alternative approach to the strategies of using
a firewall subnet or a DMZ
is to use a proxy server, or proxy firewall.
– When an
outside client requests a particular Web page, the proxy server receives the request as if it were the
subject of the request, then asks for the same information from the true Web
server(acting as a proxy for the requestor), and then responds to the request
as a proxy for the true Web server.
– For more
frequently accessed Web pages, proxy servers can cache or temporarily store the page, and thus are
sometimes called cache servers.
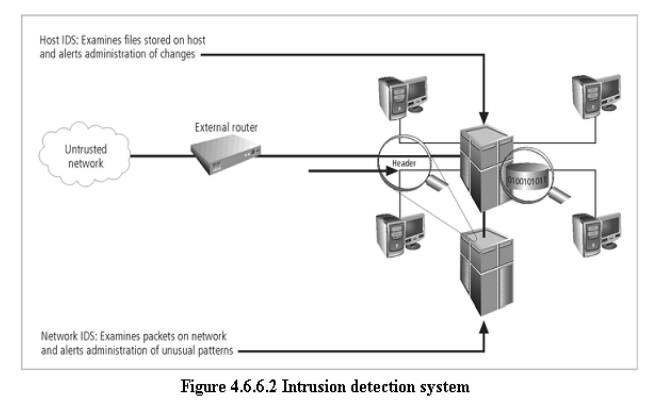
– Intrusion Detection Systems (IDSs). In an effort to detect
unauthorized activity within
the inner network, or on individual machines, an organization may wish to
implement Intrusion Detection Systems or
IDS.
–
IDs come in two versions. Host-based
& Network-based IDSs.
– Host-based IDSs are usually installed on the machines they protect
to monitor the status of
various files stored on those machines.
– Network-based IDSs look at patterns of network
traffic and attempt to detect unusual
activity based on previous baselines.
– This
could include packets coming into the organization’s networks with addresses from machines already
within the organization (IP spoofing).
– It could
also include high volumes of traffic going to outside addresses (as in cases of data theft) or coming
into the network (as in a denial of service attack).
–
Both
host-and network based IDSs require a database of previous activity.
1
Security
Education, Training, and Awareness Program
ü As soon
as general security policy exists, policies to implement security education, training
and awareness (SETA) program should follow.
ü SETA is a
control measure designed to reduce accidental security breaches by employees.
ü Security
education and training builds on the general knowledge the employees must
possess to do their jobs, familiarizing them with the way to do their jobs
securely
4.7.4 The SETA
program consists of three elements: security education; security training; and
security awareness
4.7.5 The
purpose of SETA is to enhance security by:
ü Improving
awareness of the need to protect system resources.
ü Developing
skills and knowledge so computer users can perform their jobs more securely.
ü Building
in-depth knowledge, as needed, to design, implement, or operate security
programs for organizations and systems.
Security Education
1 Everyone
in an organization needs to be trained and aware of information security, but
not every member of the organization needs a formal degree or certificate in
information security.
2 A number
of universities have formal coursework in information security.
3 For those
interested in researching formal information security programs, there are
resources available, such as the NSA-identified Centers of Excellence in
Information Assurance Education.
Security Training
· It
involves providing members of the organization with detailed information and
hands-on instruction to prepare them to perform their duties securely.
· Management
of information security can develop customized in-house training or outsource
the training program.
Security Awareness
ü One of
the least frequently implemented, but most beneficial programs is the security
awareness program
ü Designed
to keep information security at the forefront of users’ minds
ü Need not
be complicated or expensive
ü If the
program is not actively implemented, employees may begin to “tune out” and risk
of employee accidents and failures increases
Related Topics