Chapter: Security in Computing : Security in Networks
Denial of Service
Denial of Service
So far, we have discussed
attacks that lead to failures of confidentiality or integrityproblems we have
also seen in the contexts of operating systems, databases, and applications.
Availability attacks, sometimes called denial-of-service or DOS attacks, are
much more significant in networks than in other contexts. There are many
accidental and malicious threats to availability or continued service.
Transmission Failure
Communications fail for many
reasons. For instance, a line is cut. Or network noise makes a packet
unrecognizable or undeliverable. A machine along the transmission path fails
for hardware or software reasons. A device is removed from service for repair
or testing. A device is saturated and rejects incoming data until it can clear
its overload. Many of these problems are temporary or automatically fixed
(circumvented) in major networks, including the Internet.
However, some failures cannot be easily
repaired. A break in the single communications line to your computer (for
example, from the network to your network interface card or the telephone line
to your modem) can be fixed only by establishment of an alternative link or
repair of the damaged one. The network administrator will say "service to
the rest of the network was unaffected," but that is of little consolation
to you.
From a malicious standpoint,
you can see that anyone who can sever, interrupt, or overload capacity to you
can deny you service. The physical threats are pretty obvious. We consider
instead several electronic attacks that can cause a denial of service.
Connection Flooding
The most primitive
denial-of-service attack is flooding a connection. If an attacker sends you as
much data as your communications system can handle, you are prevented from
receiving any other data. Even if an occasional packet reaches you from someone
else, communication to you will be seriously degraded.
More sophisticated attacks
use elements of Internet protocols. In addition to TCP and UDP, there is a
third class of protocols, called ICMP
or Internet Control Message Protocols. Normally used for system diagnostics,
these protocols do not have associated user applications. ICMP protocols
include
ping, which requests a destination to return a reply, intended to show
that the destination system is reachable and functioning
echo, which requests a destination to return the data sent to it,
intended to show that the connection link is reliable (ping is actually a version of echo)
destination unreachable,
which indicates that a destination address cannot be accessed
source quench, which means
that the destination is becoming saturated and the source should suspend
sending packets for a while
These protocols have
important uses for network management. But they can also be used to attack a
system. The protocols are handled within the network stack, so the attacks may
be difficult to detect or block on the receiving host. We examine how these
protocols can be used to attack a victim.
Echo-Chargen
This attack works between two
hosts. Chargen is a protocol that generates a stream of packets; it is used to
test the network's capacity. The attacker sets up a chargen process on host A
that generates its packets as echo packets with a destination of host B. Then,
host A produces a stream of packets to which host B replies by echoing them
back to host A. This series puts the network infrastructures of A and B into an
endless loop. If the attacker makes B both the source and destination address
of the first packet, B hangs in a loop, constantly creating and replying to its
own messages.
Ping of Death
A ping of death is a simple attack. Since ping requires the recipient
to respond to the ping request, all the attacker needs to do is send a flood of
pings to the intended victim. The attack is limited by the smallest bandwidth
on the attack route. If the attacker is on a 10-megabyte (MB) connection and
the path to the victim is 100 MB or more, the attacker cannot mathematically
flood the victim alone. But the attack succeeds if the numbers are reversed:
The attacker on a 100-MB connection can easily flood a 10-MB victim. The ping
packets will saturate the victim's bandwidth.
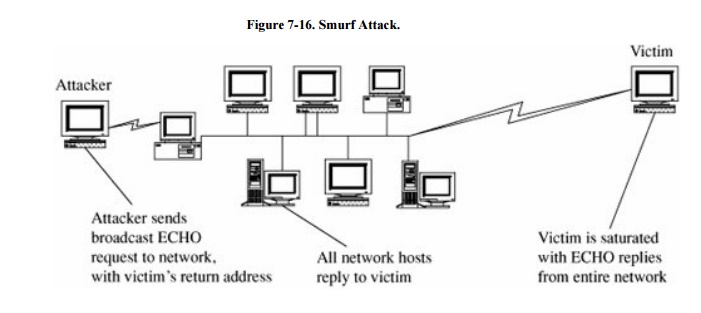
Smurf
The smurf
attack is a variation of a ping attack. It uses the same vehicle, a ping
packet, with two extra twists. First, the attacker chooses a network of
unwitting victims. The attacker spoofs the source address in the ping packet so
that it appears to come from the victim. Then, the attacker sends this request
to the network in broadcast mode by setting the last byte of the address to all
1s; broadcast mode packets are distributed to all hosts on the network. The
attack is shown in Figure 7-16.
Syn Flood
Another popular
denial-of-service attack is the syn
flood. This attack uses the TCP protocol suite, making the session-oriented
nature of these protocols work against the victim.
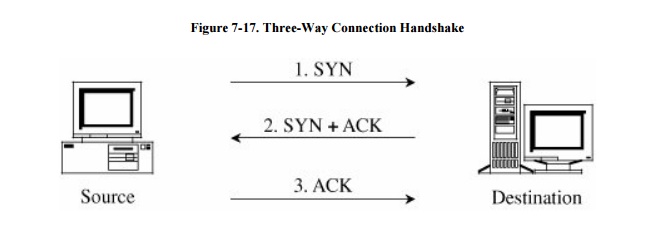
For a protocol such as Telnet, the protocol
peers establish a virtual connection, called a session, to synchronize the
back-and -forth, command-response nature of the Telnet terminal emulation. A
session is established with a three-way TCP handshake. Each TCP packet has flag
bits, two of which are denoted SYN and ACK. To initiate a TCP connection, the
originator sends a packet with the SYN bit on. If the recipient is ready to
establish a connection, it replies with a packet with both the SYN and ACK bits
on. The first party then completes the exchange to demonstrate a clear and
complete communication channel by sending a packet with the ACK bit on, as
shown in Figure 7-17.
Occasionally packets get lost
or damaged in transmission. The destination maintains a queue called the
SYN_RECV connections, tracking those items for which a SYNACK has been sent but
no corresponding ACK has yet been received. Normally, these connections are
completed in a short time. If the SYNACK (2) or the ACK (3) packet is lost,
eventually the destination host will time out the incomplete connection and
discard it from its waiting queue.
The attacker can deny service
to the target by sending many SYN requests and never responding with ACKs,
thereby filling the victim's SYN_RECV queue. Typically, the SYN_RECV queue is
quite small, such as 10 or 20 entries. Because of potential routing delays in
the Internet, typical holding times for the SYN_RECV queue can be minutes. So
the attacker need only send a new SYN request every few seconds and it will
fill the queue.
Attackers using this approach
usually do one more thing: They spoof the nonexistent return address in the
initial SYN packet. Why? For two reasons. First, the attacker does not want to
disclose the real source address in case someone should inspect the packets in
the SYN_RECV queue to try to identify the attacker. Second, the attacker wants
to make the SYN packets indistinguishable from legitimate SYN packets to
establish real connections. Choosing a different (spoofed) source address for
each one makes them unique. A SYNACK packet to a nonexistent address results in
an ICMP Destination Unreachable response, but this is not the ACK for which the
TCP connection is waiting. (Remember that TCP and ICMP are different protocol
suites, so an ICMP reply does not necessarily get back to the sender's TCP
handler.)
Teardrop
The teardrop attack misuses a
feature designed to improve network communication. A network IP datagram is a
variable-length object. To support different applications and conditions, the
datagram protocol permits a single data unit to be fragmented, that is, broken
into pieces and transmitted separately. Each fragment indicates its length and
relative position within the data unit. The receiving end is responsible for
reassembling the fragments into a single data unit.
In the teardrop attack, the
attacker sends a series of datagrams that cannot fit together properly. One
datagram might say it is position 0 for length 60 bytes, another position 30
for 90 bytes, and another position 41 for 173 bytes. These three pieces
overlap, so they cannot be reassembled properly. In an extreme case, the
operating system locks up with these partial data units it cannot reassemble,
thus leading to denial of service.
For more on these and other
denial of service threats, see [CER99
and MAR05].
Traffic Redirection
As we saw earlier, at the
network layer, a router is a device that forwards traffic on its way through
intermediate networks between a source host's network and a destination's
network. So if an attacker can corrupt the routing, traffic can disappear.
Routers use complex
algorithms to decide how to route traffic. No matter the algorithm, they
essentially seek the best path (where "best" is measured in some
combination of distance, time, cost, quality, and the like). Routers are aware
only of the routers with which they share a direct network connection, and they
use gateway protocols to share information about their capabilities. Each
router advises its neighbors about how well it can reach other network
addresses. This characteristic allows an attacker to disrupt the network.
To see how, keep in mind
that, in spite of its sophistication, a router is simply a computer with two or
more network interfaces. Suppose a router advertises to its neighbors that it
has the best path to every other address in the whole network. Soon all routers
will direct all traffic to that one router. The one router may become flooded,
or it may simply drop much of its traffic. In either case, a lot of traffic
never makes it to the intended destination.
DNS Attacks
Our final denial-of-service attack is actually
a class of attacks based on the concept of domain name server. A domain name
server (DNS) is a table that converts domain names like ATT.COM into network
addresses like 211.217.74.130; this process is called resolving the domain
name. A domain name server queries other name servers to resolve domain names
it does not know. For efficiency, it caches the answers it receives so it can
resolve that name more rapidly in the future. A pointer to a DNS server can be
retained for weeks or months.
In the most common
implementations of Unix, name servers run software called Berkeley Internet
Name Domain or BIND or named (a shorthand for "name daemon"). There
have been numerous flaws in BIND, including the now-familiar buffer overflow.
By overtaking a name server
or causing it to cache spurious entries (called DNS cache poisoning), an
attacker can redirect the routing of any traffic, with an obvious implication
for denial of service.
In October 2002, a massive
flood of traffic inundated the top -level domain DNS servers, the servers that
form the foundation of the Internet addressing structure. Roughly half the
traffic came from just 200 addresses. Although some people think the problem
was a set of misconfigured firewalls, nobody knows for sure what caused the
attack.
An attack in March 2005 used
a flaw in a Symantec firewall to allow a change in the DNS records used on
Windows machines. The objective of this attack was not denial of service,
however. In this attack, the poisoned DNS cache redirected users to advertising
sites that received money from clients each time a user visited the site.
Nevertheless, the attack also prevented users from accessing the legitimate
sites.
Related Topics