Chapter: Cryptography and Network Security Principles and Practice : One Symmetric Ciphers : Block Cipher Operation
Cipher Feedback Mode
CIPHER FEEDBACK MODE
For AES, DES, or any block cipher,
encryption is performed
on a block of b bits. In the
case of DES, b = 64 and in the case of AES, b = 128. However,
it is possible to convert a block cipher
into a stream cipher, using
one of the three modes
to be dis- cussed in this and the next two sections: cipher feedback
(CFB) mode, output feed- back (OFB) mode, and counter (CTR) mode. A stream cipher eliminates the need to pad a message
to be an integral number of blocks.
It also can operate in real time. Thus, if a character stream is being
transmitted, each character can be encrypted and transmitted immediately using
a character-oriented stream
cipher.
One desirable property of a stream cipher
is that the ciphertext be of the same
length as the plaintext. Thus, if 8-bit characters are being transmitted, each character
should be encrypted to produce
a ciphertext output
of 8 bits. If more than 8 bits are
produced, transmission capacity
is wasted.
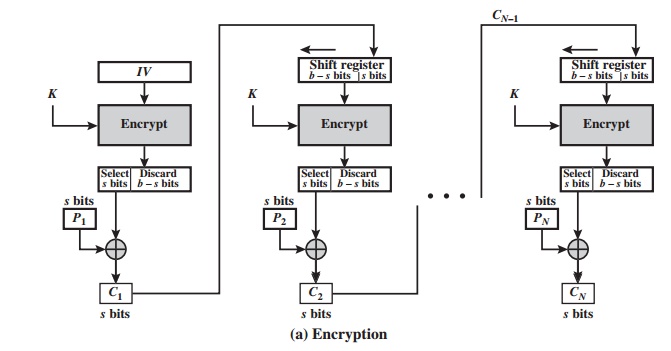
Figure 6.5 depicts the CFB scheme.
In the figure, it is assumed that the unit of
transmission is s bits; a common value
is s = 8. As with CBC, the units
of plaintext are chained
together, so that the ciphertext of any plaintext unit is a function of all the preceding plaintext. In this
case, rather than blocks of b bits,
the plaintext is divided into segments of
s
bits.
First, consider
encryption. The input to the encryption function is a b-bit
shift register that is initially set to some initialization vector
(IV). The leftmost (most
sig- nificant) s bits of the
output of the encryption function are XORed with the first segment of plaintext
P1 to produce
the first unit of ciphertext C1,
which is then transmitted. In addition, the contents of the shift register
are shifted left by s bits, and C1 is
placed in the rightmost (least significant) s
bits of the shift register. This process
continues until all plaintext units have been encrypted.
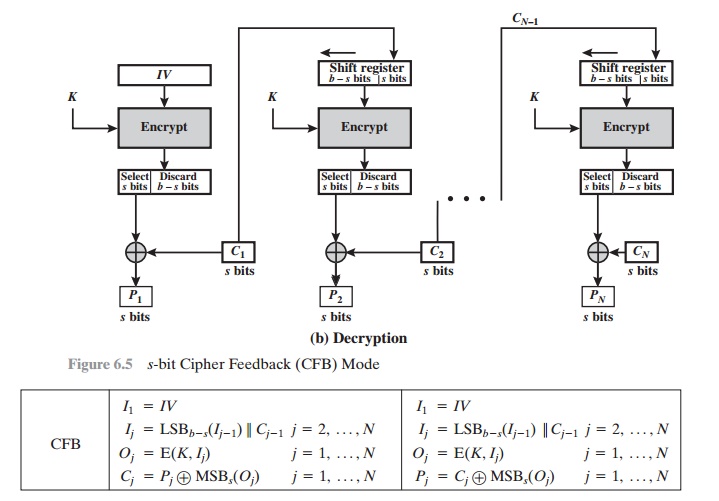
For decryption, the same scheme is used, except
that the received ciphertext unit is XORed with the output of the encryption
function to produce the plaintext unit. Note that it is the encryption function that is used, not
the decryption func- tion. This is easily explained. Let MSBs(X) be defined as the most significant s bits of X. Then
C1 = P1 Ⓧ MSBs[E(K, IV)]
Therefore,
by rearranging terms:
P1 = C1 Ⓧ MSBs[E(K, IV)]
The
same reasoning holds for subsequent steps in the process.
We
can define CFB mode as follows.
Although
CFB can be viewed as a stream cipher, it does not conform to the typical construction of a stream
cipher. In a typical stream
cipher, the cipher
takes as input some initial value and a key and generates a stream of bits, which is then XORed
with the plaintext
bits (see Figure 3.1). In the case of CFB, the stream of bits
that is XORed with the plaintext also depends on the plaintext.
Related Topics